Whaling in phishing targets high-profile individuals such as CEOs or senior executives by crafting deceptive emails that appear urgent and legitimate. These emails often mimic trusted sources like government agencies or business partners to trick victims into revealing sensitive information or authorizing large financial transactions. Such attacks leverage personalized data gathered from social media or corporate websites, increasing their effectiveness in breaching security protocols. Organizations report that whaling attacks result in significant financial losses and data breaches due to the leverage of executive credentials. Security systems focusing on phishing detection employ advanced email filtering and user-awareness training to combat these targeted threats. Regularly updating security policies and conducting simulated phishing attacks enhance defenses against rising whaling phishing campaigns.
Table of Comparison
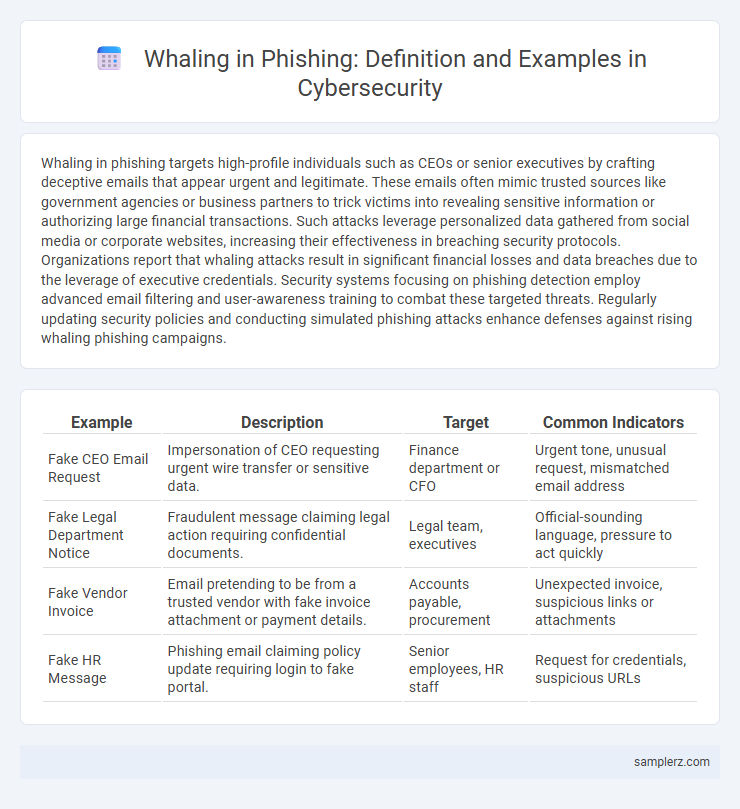
| Example | Description | Target | Common Indicators |
|---|---|---|---|
| Fake CEO Email Request | Impersonation of CEO requesting urgent wire transfer or sensitive data. | Finance department or CFO | Urgent tone, unusual request, mismatched email address |
| Fake Legal Department Notice | Fraudulent message claiming legal action requiring confidential documents. | Legal team, executives | Official-sounding language, pressure to act quickly |
| Fake Vendor Invoice | Email pretending to be from a trusted vendor with fake invoice attachment or payment details. | Accounts payable, procurement | Unexpected invoice, suspicious links or attachments |
| Fake HR Message | Phishing email claiming policy update requiring login to fake portal. | Senior employees, HR staff | Request for credentials, suspicious URLs |
Understanding Whaling: A Targeted Phishing Threat
Whaling is a sophisticated phishing attack specifically targeting high-profile executives and decision-makers to steal sensitive information or authorize fraudulent transactions. These attacks often use personalized, well-researched emails that appear to come from trusted sources within the organization, increasing their credibility and success rate. Recognizing whaling attempts requires vigilance in verifying sender identities and scrutinizing unexpected requests for confidential data or financial actions.
Notorious Whaling Attacks: Real-Life Examples
Notorious whaling attacks often target high-profile executives through spear-phishing emails that mimic trusted corporate communications, such as fake invoices or urgent legal notices. In the 2016 Snapchat incident, attackers deceived a finance executive into transferring $23,000 by impersonating the company's CEO via an email crafted with personalized details. These real-life examples underscore the critical need for advanced email authentication protocols and employee awareness training to prevent costly executive-targeted fraud.
Anatomy of a Whaling Email: Key Red Flags
A whaling email typically targets high-level executives by impersonating trusted sources like CEOs or legal departments, often containing urgent requests for sensitive information or wire transfers. Key red flags include personalized greetings that exploit specific company details, unusual email addresses that mimic legitimate domains, and language that induces fear or pressure to bypass normal verification protocols. These emails often lack proper signatures and contain subtle inconsistencies in tone or formatting, signaling potential fraud and warranting immediate scrutiny.
High-Profile Whaling Cases in the Corporate World
High-profile whaling cases, such as the 2016 FACC AG attack, saw cybercriminals impersonate top executives to defraud companies of millions through fraudulent wire transfers. Another notable incident involved the Ubiquiti Networks breach in 2015, where attackers spoofed CEO email accounts to trick employees into transferring $46.7 million. These sophisticated phishing attacks target C-level executives, exploiting corporate hierarchies for significant financial gain.
How Cybercriminals Craft Convincing Whaling Messages
Cybercriminals craft convincing whaling messages by leveraging detailed research on high-profile targets, such as executives or financial officers, to mimic legitimate communication styles and organizational language. They employ personalized information like recent transactions, project details, or hierarchical relationships to increase credibility and bypass basic security filters. Advanced social engineering techniques enhance message authenticity, often prompting urgent actions like wire transfers or confidential data disclosure.
Whaling Incidents Affecting Financial Institutions
Whaling incidents targeting financial institutions involve highly sophisticated spear-phishing attacks aimed at senior executives to gain unauthorized access to critical financial data. One notable example occurred in 2016 when cybercriminals impersonated a CEO to trick a CFO into transferring $17 million to fraudulent accounts. These attacks exploit social engineering techniques and require stringent email authentication protocols and employee training to mitigate financial and reputational risks.
Recent Whaling Scams Targeting Executives
Recent whaling scams have increasingly targeted C-level executives by impersonating CEOs or CFOs in urgent, high-stakes email requests for wire transfers or sensitive financial data. Attackers leverage sophisticated social engineering tactics and domain spoofing to bypass traditional email security filters, exploiting executives' trust and busy schedules. Organizations report millions in losses as these scams bypass standard phishing defenses, emphasizing the need for enhanced executive-focused security training and multifactor authentication protocols.
Impact of Whaling Attacks on Organizational Security
Whaling attacks specifically target high-level executives, leading to significant financial losses and reputational damage for organizations. These sophisticated phishing scams can compromise sensitive corporate data and enable unauthorized access to critical systems. The resulting security breaches often disrupt business operations and erode stakeholder trust.
Lessons Learned from Famous Whaling Breaches
Famous whaling breaches highlight the critical importance of verifying executive communications through multiple channels to prevent financial fraud. Attackers often exploit trust and authority by impersonating high-level executives in targeted phishing emails, leading to significant financial losses and data breaches. Implementing rigorous email authentication protocols and employee training on recognizing social engineering tactics can significantly reduce the risk of whaling attacks.
Best Practices to Prevent Whaling Phishing Attacks
Implement multi-factor authentication and conduct regular employee training to recognize whaling phishing tactics targeted at executives and high-value employees. Employ email filtering solutions using artificial intelligence to detect and block spear-phishing messages impersonating trusted sources. Establish strict verification protocols for financial and sensitive information requests to reduce the risk of fraudulent executive impersonation.
example of whaling in phishing Infographic
 samplerz.com
samplerz.com