Jailbreaking in device security refers to the process of removing software restrictions imposed by the device manufacturer. This practice is commonly performed on smartphones and tablets to gain root access to the operating system. Jailbreaking allows users to install unauthorized applications, modify system settings, and access restricted features that are typically locked for security reasons. The security risks associated with jailbreaking include increased vulnerability to malware, unauthorized data access, and potential breaches of personal information. Devices that have been jailbroken may bypass critical security protocols and updates, making them more susceptible to cyber attacks. Security teams often highlight jailbreaking as a significant threat vector that compromises the integrity of device security frameworks.
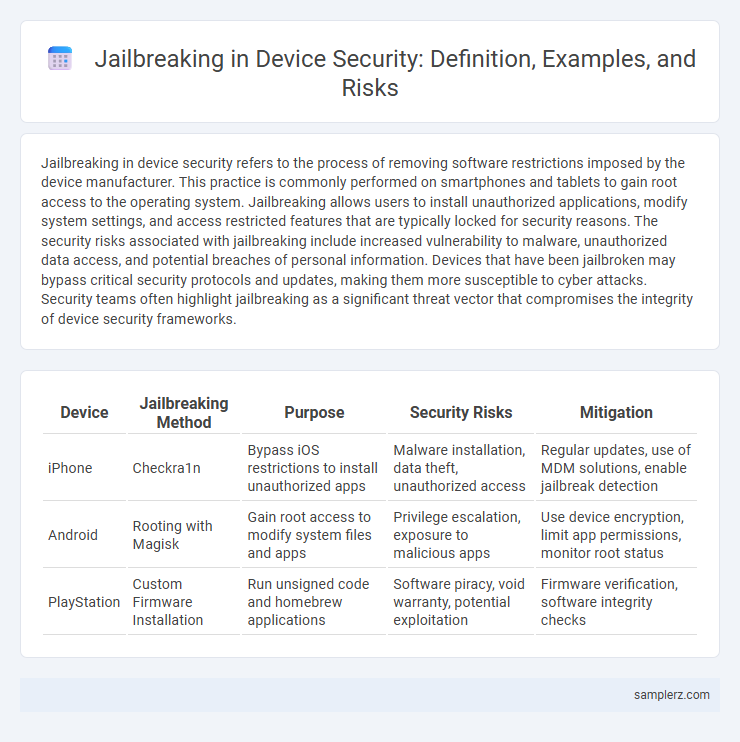
Table of Comparison
| Device | Jailbreaking Method | Purpose | Security Risks | Mitigation |
|---|---|---|---|---|
| iPhone | Checkra1n | Bypass iOS restrictions to install unauthorized apps | Malware installation, data theft, unauthorized access | Regular updates, use of MDM solutions, enable jailbreak detection |
| Android | Rooting with Magisk | Gain root access to modify system files and apps | Privilege escalation, exposure to malicious apps | Use device encryption, limit app permissions, monitor root status |
| PlayStation | Custom Firmware Installation | Run unsigned code and homebrew applications | Software piracy, void warranty, potential exploitation | Firmware verification, software integrity checks |
Understanding Jailbreaking: Definition and Security Implications
Jailbreaking is the process of removing software restrictions imposed by a device's operating system, typically on iOS devices, to allow unauthorized access to system files and third-party applications. This practice exposes devices to significant security risks such as malware infections, data breaches, and compromised device integrity. Understanding jailbreaking is crucial for assessing its impact on device security and implementing protective measures against potential vulnerabilities.
Common Devices Vulnerable to Jailbreaking
Smartphones such as iPhones and Android devices remain the most commonly targeted devices for jailbreaking due to their widespread use and locked-down operating systems. Gaming consoles like PlayStation and Xbox also face jailbreak attempts to bypass restrictions and enable unauthorized software. Tablets, including iPads, exhibit vulnerabilities that allow users to gain root access, compromising device security and manufacturer control.
Popular Jailbreaking Methods and Tools
Popular jailbreaking methods exploit vulnerabilities in iOS firmware, with tools like Checkra1n and Unc0ver leading the scene by enabling root access and bypassing Apple's restrictions. These tools often utilize kernel exploits or privilege escalation techniques to unlock the device, allowing installation of unauthorized apps and customization beyond default security protocols. Understanding the mechanics of such jailbreaks is critical for developing robust device security measures and mitigating risks associated with unauthorized access.
Risks Associated With Jailbreaking Devices
Jailbreaking devices exposes them to significant security risks, including increased vulnerability to malware, unauthorized access, and data breaches. Removing built-in security restrictions allows malicious apps to bypass traditional safeguards, compromising sensitive information. This practice can also void warranties and prevent users from receiving critical security updates from the device manufacturer.
Real-World Examples of Jailbreaking in Action
Real-world examples of jailbreaking highlight significant security risks on devices such as iPhones and gaming consoles, where users bypass manufacturer restrictions to install unauthorized software. The 2010 iPhone jailbreak by the Chronic Dev Team exposed vulnerabilities in Apple's iOS, allowing users to gain root access and customize their phones beyond Apple's guidelines. Similarly, jailbreaking Xbox and PlayStation consoles has enabled piracy and unauthorized modifications, prompting constant security updates from manufacturers to combat such exploits.
Notorious Jailbreaking Incidents in Device Security History
The 2010 iPhone 4 jailbreak by the jailbreak community through the "JailbreakMe" web-based tool showcased a significant breach in device security, allowing unauthorized app installation. Another notorious incident is the 2014 Android Stagefright vulnerability exploit, enabling attackers to remotely execute code by sending malicious multimedia messages. These historical jailbreaks highlight persistent risks in device security, emphasizing the need for robust protective measures against unauthorized access.
Impact of Jailbreaking on Operating System Integrity
Jailbreaking compromises operating system integrity by bypassing built-in security mechanisms, allowing unauthorized access to system files and kernel modifications. This exposes devices to malware infections, data breaches, and instability due to unauthorized apps running with elevated privileges. The removal of security controls undermines trust in the operating system's ability to enforce access restrictions and maintain system reliability.
How Jailbreaking Facilitates Malware and Unauthorized Access
Jailbreaking a device removes manufacturer-imposed restrictions, allowing installation of unauthorized apps that can bypass security protocols. This process exposes vulnerabilities, enabling malware to infiltrate the system and access sensitive information without detection. Exploited jailbroken devices often become entry points for hackers to gain unauthorized access and control over personal and corporate data.
Preventative Measures Against Jailbreaking
Implementing robust firmware integrity checks and secure boot mechanisms significantly reduce the risk of jailbreaking in iOS and Android devices. Enforcing strict app sandboxing and timely security patch deployments prevent unauthorized code execution and privilege escalation exploited by jailbreaking tools. Device manufacturers incorporate hardware-level security features like Trusted Execution Environments (TEE) to ensure sensitive operations remain protected from jailbreak attempts.
Legal and Ethical Considerations of Jailbreaking
Jailbreaking a device often violates manufacturer warranties and can breach terms of service agreements, leading to potential legal repercussions. It raises ethical concerns by exposing devices to security vulnerabilities, which may compromise user data and privacy. Understanding these legal and ethical implications is critical for informed decision-making in device security management.
example of jailbreaking in device security Infographic
 samplerz.com
samplerz.com