A rogue access point (AP) in a wireless network is an unauthorized device installed within the network's range, often by employees or attackers, without proper security approval. These devices can mimic legitimate APs, creating backdoors for cybercriminals to intercept sensitive data or launch attacks. Detecting rogue APs requires continuous network monitoring and the implementation of advanced security protocols. An example of a rogue AP is a wireless router set up by a disgruntled employee to bypass network restrictions, allowing unfiltered network access to outsiders. Another example involves cyber attackers installing a fake AP resembling the company's SSID, tricking users into connecting and exposing confidential information. Security solutions such as rogue AP detection tools and wireless intrusion prevention systems (WIPS) play a crucial role in mitigating these threats.
Table of Comparison
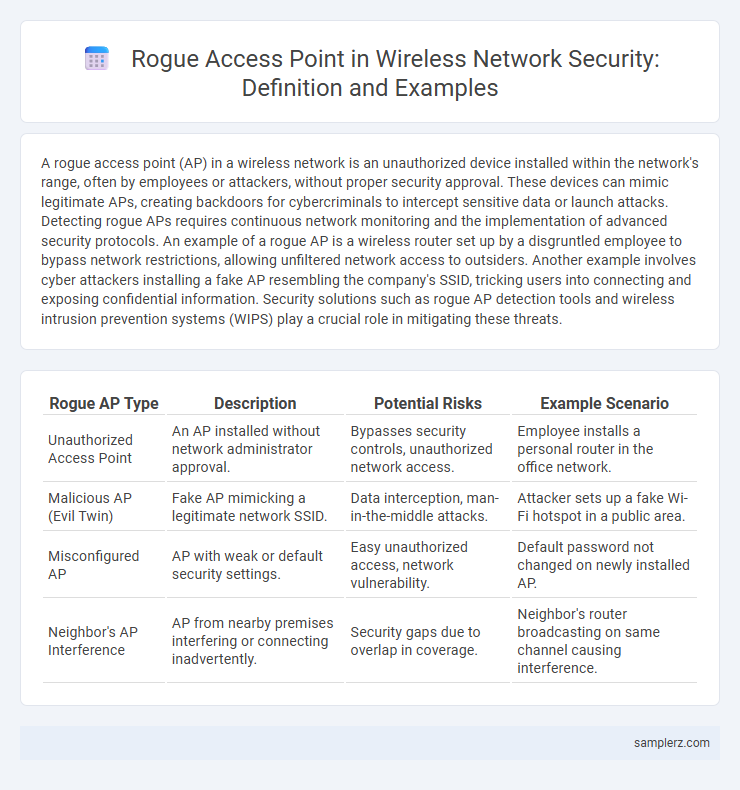
| Rogue AP Type | Description | Potential Risks | Example Scenario |
|---|---|---|---|
| Unauthorized Access Point | An AP installed without network administrator approval. | Bypasses security controls, unauthorized network access. | Employee installs a personal router in the office network. |
| Malicious AP (Evil Twin) | Fake AP mimicking a legitimate network SSID. | Data interception, man-in-the-middle attacks. | Attacker sets up a fake Wi-Fi hotspot in a public area. |
| Misconfigured AP | AP with weak or default security settings. | Easy unauthorized access, network vulnerability. | Default password not changed on newly installed AP. |
| Neighbor's AP Interference | AP from nearby premises interfering or connecting inadvertently. | Security gaps due to overlap in coverage. | Neighbor's router broadcasting on same channel causing interference. |
Introduction to Rogue Access Points in Wireless Networks
A rogue access point (AP) is an unauthorized wireless access device installed within a secure network, often by employees or attackers, bypassing security protocols. These devices can create vulnerabilities by allowing malicious users to intercept, alter, or disrupt network traffic, leading to data breaches and unauthorized access. Detecting rogue APs involves continuous network monitoring and deploying wireless intrusion prevention systems to ensure network integrity and security compliance.
How Rogue APs Compromise Network Security
Rogue Access Points (APs) compromise network security by creating unauthorized wireless entry points that bypass established security protocols, allowing attackers to intercept sensitive data and inject malicious traffic. These rogue devices often mimic legitimate APs, enabling man-in-the-middle attacks and credential theft through techniques like Evil Twin attacks. The presence of Rogue APs undermines network segmentation and enforces vulnerabilities that security systems cannot detect, leading to significant data breaches and unauthorized access.
Common Methods of Deploying Rogue Access Points
Common methods of deploying rogue access points in wireless networks include unauthorized physical installation of devices mimicking legitimate APs and the use of software-based APs on compromised or employee devices. Attackers often leverage default or weak credentials to configure these devices, enabling eavesdropping, credential theft, and network infiltration. Rogue APs may also be set up as evil twins, broadcasting identical SSIDs to capture sensitive data from unsuspecting users.
Real-World Examples of Rogue AP Attacks
Rogue access points, such as the 2018 case where a fake Wi-Fi hotspot named "Starbucks_WiFi" was set up in a busy New York cafe, demonstrate real-world risks by capturing unsuspecting users' sensitive data. In another example, the 2020 attack on a major university involved a rogue AP mimicking the official campus network, leading to widespread credential theft and network infiltration. These incidents highlight the critical need for continuous wireless network monitoring and the implementation of robust rogue AP detection systems to prevent data breaches.
Signs and Symptoms of a Rogue AP in Your Network
Unusual wireless access points appearing in your network inventory indicate the presence of rogue APs, often broadcasting unfamiliar SSIDs or mimicking legitimate network names. Network performance degradation, including increased latency and frequent disconnections, can signal unauthorized devices consuming bandwidth or causing interference. Security alerts from intrusion detection systems highlighting suspicious device activity and authentication failures also serve as critical indicators of rogue APs in your wireless environment.
Case Study: Corporate Data Breach via Rogue AP
A corporate data breach occurred when an attacker installed a rogue access point (AP) within the company's wireless network, mimicking the legitimate SSID to intercept sensitive information. The unauthorized AP enabled man-in-the-middle attacks, capturing employee credentials and confidential business data. This breach exposed vulnerabilities in network monitoring and highlighted the importance of robust wireless intrusion detection systems.
Detection Techniques for Rogue Access Points
Detection techniques for rogue access points in wireless networks include wireless intrusion detection systems (WIDS) that continuously monitor the radio frequency spectrum for unauthorized devices. Signature-based detection identifies known rogue AP patterns, while anomaly-based detection uses machine learning algorithms to spot unusual network behaviors. Passive detection relies on scanning network traffic for unauthorized devices, whereas active detection involves sending probes to verify the legitimacy of access points.
Mitigation and Prevention Strategies Against Rogue APs
Mitigation and prevention strategies against rogue access points (APs) include implementing continuous wireless network monitoring tools that detect unauthorized devices by analyzing MAC addresses and SSID patterns. Employing strong authentication protocols such as WPA3 and network access control (NAC) systems can restrict rogue AP connectivity and enforce device compliance. Regularly conducting wireless site surveys and educating employees on the risks of connecting unauthorized devices further strengthen defenses against rogue AP threats.
The Role of Employee Awareness in Preventing Rogue APs
Employee awareness plays a critical role in preventing rogue access points (APs) within wireless networks by ensuring staff recognize unauthorized devices and understand the security risks they pose. Training programs that emphasize identifying suspicious network behavior and adhering to organizational security policies reduce the chances of inadvertent rogue AP deployment. Regular security audits combined with employee vigilance create a proactive defense against potential breaches caused by rogue APs.
Future Trends and Threats Related to Rogue Access Points
Rogue access points (APs) continue to pose significant security risks in wireless networks, with future trends indicating increased sophistication through evasion techniques such as mimicry of legitimate SSIDs and use of encrypted tunnels to bypass detection. Emerging threats involve AI-powered rogue APs capable of dynamically adapting signal characteristics and launching targeted man-in-the-middle (MITM) attacks, making traditional security measures less effective. Organizations must invest in advanced wireless intrusion detection systems (WIDS) integrated with machine learning algorithms to proactively identify and mitigate these evolving rogue AP threats.
example of rogue AP in wireless network Infographic
 samplerz.com
samplerz.com