Keyloggers are a common type of malware designed to record keystrokes on infected devices. These malicious programs capture sensitive information such as usernames, passwords, and credit card details. One prominent example of keylogger malware is Zeus, which has been widely used to steal banking credentials. Zeus operates by embedding itself into the system and logging all keyboard inputs without the user's knowledge. It transmits the collected data to remote servers controlled by cybercriminals. Security professionals recommend using updated antivirus software and monitoring network traffic to detect and prevent keylogger infections effectively.
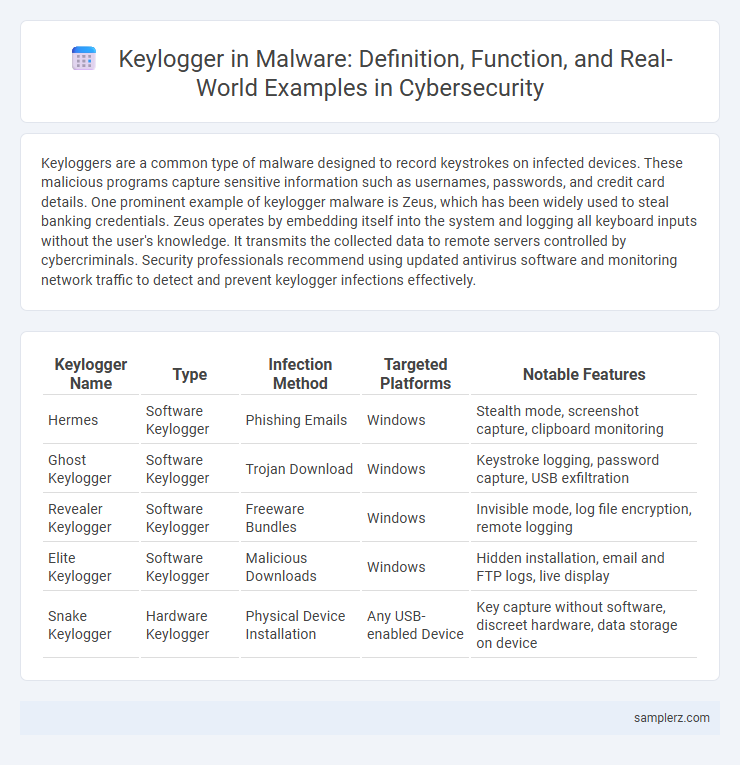
Table of Comparison
| Keylogger Name | Type | Infection Method | Targeted Platforms | Notable Features |
|---|---|---|---|---|
| Hermes | Software Keylogger | Phishing Emails | Windows | Stealth mode, screenshot capture, clipboard monitoring |
| Ghost Keylogger | Software Keylogger | Trojan Download | Windows | Keystroke logging, password capture, USB exfiltration |
| Revealer Keylogger | Software Keylogger | Freeware Bundles | Windows | Invisible mode, log file encryption, remote logging |
| Elite Keylogger | Software Keylogger | Malicious Downloads | Windows | Hidden installation, email and FTP logs, live display |
| Snake Keylogger | Hardware Keylogger | Physical Device Installation | Any USB-enabled Device | Key capture without software, discreet hardware, data storage on device |
Keylogger Definition in Malware Context
A keylogger in malware context is a type of malicious software designed to secretly record keystrokes on a victim's device, capturing sensitive information such as passwords, credit card numbers, and personal messages. This spyware operates silently in the background, often evading antivirus detection and transmitting stolen data to cybercriminals. Effective cybersecurity measures include using updated security software and practicing cautious online behavior to mitigate keylogger threats.
How Keyloggers Work in Cyber Threats
Keyloggers operate by secretly recording keystrokes on a victim's device, capturing sensitive information such as passwords, credit card numbers, and personal messages. These malicious programs infiltrate systems through phishing emails, infected downloads, or compromised websites, embedding themselves deeply to avoid detection by antivirus software. Cybercriminals use the harvested data for identity theft, financial fraud, and unauthorized account access, making keyloggers a persistent security threat in malware attacks.
Famous Real-World Keylogger Attacks
The Zeus Trojan stands as one of the most notorious real-world keylogger attacks, having compromised millions of banking credentials globally. Another significant example is the Ghost Keylogger, widely used by cybercriminals to stealthily capture keystrokes and sensitive information. These keylogger malware exemplify the persistent threat to personal and organizational cybersecurity through covert data theft.
Types of Keyloggers Used by Hackers
Hardware keyloggers, such as USB devices or keyboard overlays, physically capture keystrokes by intercepting signals between the keyboard and computer. Software-based keyloggers include form grabbers, kernel-based, API-based, and JavaScript keyloggers that stealthily record keystrokes through various system vulnerabilities and browser scripts. Wireless keyloggers intercept keystrokes transmitted over wireless keyboards, exploiting unencrypted signals to monitor user input remotely.
Notorious Malware Families Featuring Keyloggers
Notorious malware families featuring keyloggers include Zeus, Emotet, and Agent Tesla, each designed to secretly capture keystrokes and steal sensitive information such as login credentials and financial data. Zeus primarily targets banking details, while Emotet acts as a modular malware capable of downloading additional payloads including keyloggers. Agent Tesla is widely used for corporate espionage, extracting data from various applications to compromise organizational security.
Keylogger Techniques: Hardware vs Software
Keylogger techniques in malware include hardware-based methods, where physical devices such as USB keystroke loggers intercept and record keystrokes, and software-based methods involving malicious programs that capture input data at the operating system level. Hardware keyloggers are difficult to detect as they operate independently of the system's software, whereas software keyloggers use techniques like kernel-level hooking, API hooking, or form grabbing to stealthily monitor user input. Understanding the differences in keylogger implementations is essential for developing effective cybersecurity defenses and forensic investigations.
Key Indicators of Keylogger Infections
Key indicators of keylogger infections include unusual CPU usage, unexpected network activity, and frequent pop-ups or system slowdowns. Monitoring keystroke logs and detecting unauthorized access to keyboard input buffers can reveal the presence of spyware such as malware-based keyloggers like Agent Tesla or HawkEye. Early identification through behavioral analysis and real-time monitoring tools mitigates data theft risks and preserves system integrity.
Keylogger Payload Delivery Methods
Keylogger payload delivery methods in malware commonly include phishing emails with malicious attachments, drive-by downloads from compromised websites, and trojanized software installers. These techniques exploit user trust or system vulnerabilities to stealthily install keyloggers that record keystrokes and capture sensitive information. Understanding these delivery methods is crucial for developing effective endpoint protection and intrusion detection strategies.
Data Stolen by Keylogger Malware Examples
Keylogger malware frequently targets sensitive data such as usernames, passwords, credit card numbers, and personal identification information. Examples include Zeus and Emotet, which stealthily capture keystrokes to harvest banking credentials and login details for unauthorized access. These stolen data enable cybercriminals to commit fraud, identity theft, and financial theft with minimal detection.
Preventing and Removing Keyloggers in Cybersecurity
Keyloggers, often embedded within malware like Trojan horses or spyware, silently record keystrokes to steal sensitive information such as passwords and credit card numbers. Preventing keyloggers involves employing robust antivirus solutions, regularly updating software, and avoiding suspicious links or downloads. Removing keyloggers requires thorough system scans with advanced anti-malware tools, coupled with vigilance in monitoring unusual system behavior to ensure complete eradication.
example of keylogger in malware Infographic
 samplerz.com
samplerz.com