A zero-day exploit targets vulnerabilities in software or hardware that developers have not yet identified or patched. One notable example is the Stuxnet worm, discovered in 2010, which exploited multiple zero-day flaws to attack Iran's nuclear centrifuges. This malware leveraged unknown vulnerabilities in Windows systems to gain unauthorized access and sabotage industrial control systems. Zero-day exploits pose significant challenges for cybersecurity as they evade traditional detection methods and prompt immediate response to minimize damage. The Shadow Brokers group revealed several zero-day exploits in 2017, which were later used in widespread ransomware attacks like WannaCry. Continuous monitoring and timely patch management remain critical strategies to defend against such stealthy and high-impact threats.
Table of Comparison
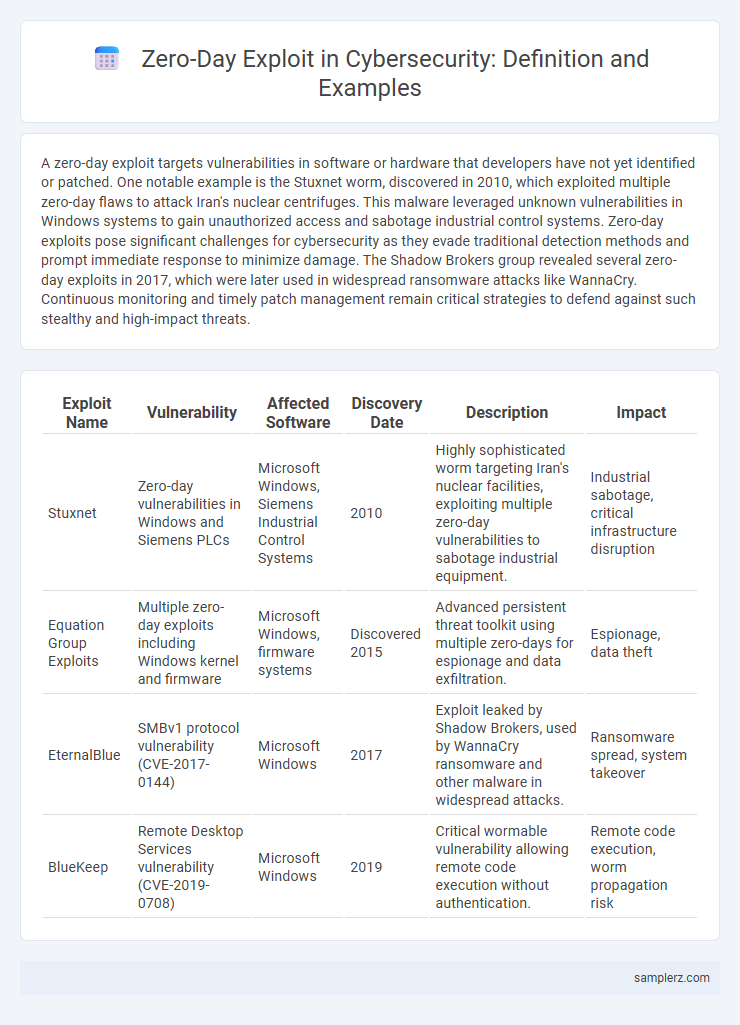
| Exploit Name | Vulnerability | Affected Software | Discovery Date | Description | Impact |
|---|---|---|---|---|---|
| Stuxnet | Zero-day vulnerabilities in Windows and Siemens PLCs | Microsoft Windows, Siemens Industrial Control Systems | 2010 | Highly sophisticated worm targeting Iran's nuclear facilities, exploiting multiple zero-day vulnerabilities to sabotage industrial equipment. | Industrial sabotage, critical infrastructure disruption |
| Equation Group Exploits | Multiple zero-day exploits including Windows kernel and firmware | Microsoft Windows, firmware systems | Discovered 2015 | Advanced persistent threat toolkit using multiple zero-days for espionage and data exfiltration. | Espionage, data theft |
| EternalBlue | SMBv1 protocol vulnerability (CVE-2017-0144) | Microsoft Windows | 2017 | Exploit leaked by Shadow Brokers, used by WannaCry ransomware and other malware in widespread attacks. | Ransomware spread, system takeover |
| BlueKeep | Remote Desktop Services vulnerability (CVE-2019-0708) | Microsoft Windows | 2019 | Critical wormable vulnerability allowing remote code execution without authentication. | Remote code execution, worm propagation risk |
Understanding Zero-Day Exploits in Cybersecurity
Zero-day exploits target vulnerabilities unknown to software vendors, allowing attackers to infiltrate systems before patches become available. These exploits pose significant risks to cybersecurity as they bypass traditional defenses and security measures. Understanding zero-day threats is crucial for developing proactive detection and response strategies to minimize damage.
Real-World Cases of Zero-Day Attacks
The 2021 Microsoft Exchange Server zero-day exploit targeted vulnerabilities in on-premises Exchange servers, allowing attackers to access email accounts and install malware. Another notorious case is the Stuxnet worm, which exploited multiple zero-day vulnerabilities in Windows to disrupt Iran's nuclear program. These real-world zero-day attacks highlight the critical importance of timely patch management and advanced threat detection in cybersecurity defense.
High-Profile Zero-Day Vulnerabilities: Notable Examples
The 2017 WannaCry ransomware attack exploited a high-profile zero-day vulnerability in the SMB protocol (EternalBlue) that affected thousands of organizations globally, causing massive disruption. Another notable example is the 2021 Microsoft Exchange Server zero-day vulnerabilities, which were leveraged by state-sponsored hackers to gain persistent access to corporate networks. These zero-day exploits demonstrate the critical need for timely patch management and advanced threat detection in cybersecurity defenses.
How Zero-Day Exploits Are Discovered and Weaponized
Zero-day exploits are discovered through rigorous vulnerability research, often by security researchers or malicious actors analyzing software code for unknown flaws before vendors release patches. These exploits are weaponized by creating malware or attack tools that leverage the unpatched vulnerability to gain unauthorized access, escalate privileges, or execute arbitrary code. Advanced persistent threat groups and cybercriminals frequently use automated frameworks and exploit kits to distribute zero-day attacks rapidly, targeting high-value systems.
Zero-Day Incidents: Lessons from Recent Breaches
Zero-day incidents such as the 2021 Microsoft Exchange Server breach demonstrate the devastating impact of undisclosed vulnerabilities exploited by threat actors before patches are available. Attackers leveraged zero-day exploits to gain unauthorized access, steal data, and deploy ransomware, emphasizing the urgent need for proactive threat intelligence and rapid incident response. These breaches highlight the critical importance of continuous monitoring and timely application of security updates to mitigate the risks of zero-day vulnerabilities.
The Lifecycle of a Zero-Day Exploit in the Wild
A zero-day exploit remains undetected from the moment it is discovered by attackers until it is patched by software vendors, during which it can cause significant damage. This lifecycle includes initial discovery, stealthy exploitation to infiltrate systems, and eventual detection through monitoring or incident reports. Understanding this timeline helps organizations prioritize vulnerability management and implement proactive threat intelligence to minimize exposure.
Notorious Zero-Day Exploits Targeting Widely-Used Software
The WannaCry ransomware attack exploited a notorious zero-day vulnerability in Microsoft Windows' SMB protocol, affecting over 200,000 computers across 150 countries in 2017. Another high-profile zero-day was the EternalBlue exploit, leveraged by cybercriminals to propagate malware rapidly through unpatched Windows systems. These zero-day exploits highlight critical risks in widely-used software, underscoring the necessity for timely patching and robust security monitoring.
Impact of Zero-Day Exploits on Organizations
Zero-day exploits pose severe security risks by targeting unknown software vulnerabilities before patches are available, allowing attackers to bypass traditional defenses. Organizations face data breaches, intellectual property theft, and operational disruptions, often resulting in substantial financial losses and reputational damage. Real-world cases, such as the Stuxnet attack and SolarWinds breach, demonstrate how zero-day exploits can compromise critical infrastructure and sensitive information on a massive scale.
Zero-Day Exploit Detection: Challenges and Approaches
Zero-day exploit detection faces significant challenges due to the unknown nature of vulnerabilities and the absence of prior signatures, making traditional detection methods ineffective. Behavioral analytics and machine learning models analyze anomalies in system behavior and network traffic to identify potential zero-day attacks with higher accuracy. Continuous threat intelligence integration and sandboxing techniques further enhance early detection and mitigation of these sophisticated exploits.
Mitigating Risks from Emerging Zero-Day Threats
Mitigating risks from emerging zero-day threats requires proactive vulnerability management and real-time threat intelligence integration to identify and neutralize unknown exploits before widespread damage occurs. Implementing behavior-based detection systems and employing endpoint protection platforms can limit the impact of zero-day attacks in enterprise environments. Continuous patching cycles combined with network segmentation further reduce attack surfaces, minimizing exposure to zero-day vulnerabilities.
example of zero-day in exploit Infographic
 samplerz.com
samplerz.com