The kill chain in a security attack outlines the step-by-step phases a threat actor follows to infiltrate and exploit a target network. It typically begins with reconnaissance, where attackers gather information about the target, followed by weaponization, where malicious tools are developed or selected. The process continues with delivery, exploiting vulnerabilities to deliver malware, establishing command and control, and finally executing the intended malicious activities. Data collected from attack investigations often reveals these stages clearly, enabling security teams to identify and disrupt threats at various points. Entities such as cybersecurity firms and security operation centers utilize kill chain models to enhance detection capabilities and response strategies. Understanding the kill chain phases improves incident response effectiveness and helps in deploying preventive controls to protect critical assets.
Table of Comparison
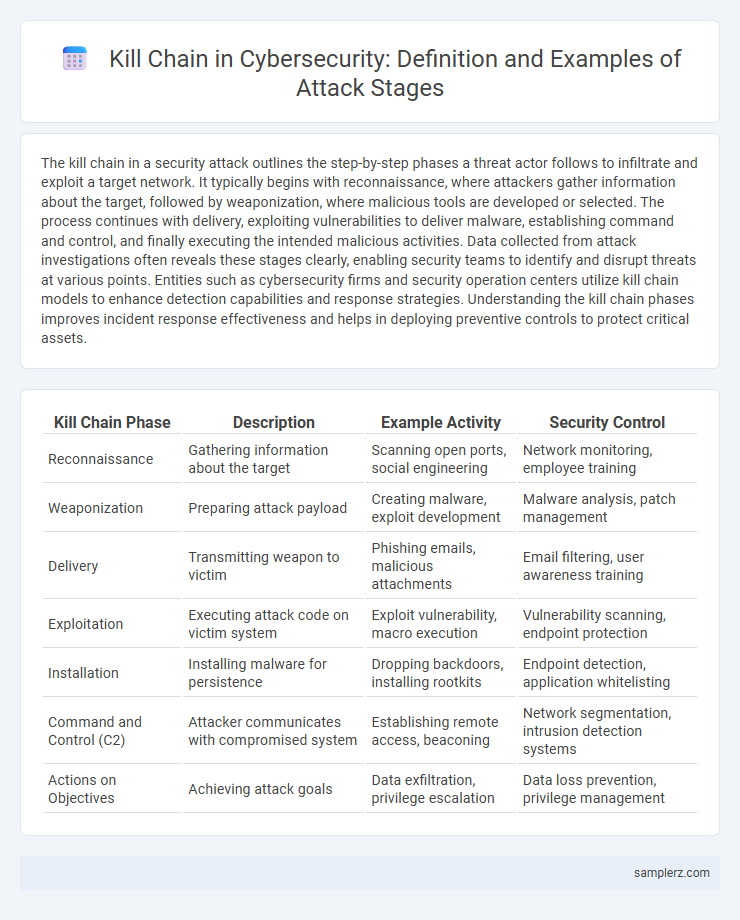
| Kill Chain Phase | Description | Example Activity | Security Control |
|---|---|---|---|
| Reconnaissance | Gathering information about the target | Scanning open ports, social engineering | Network monitoring, employee training |
| Weaponization | Preparing attack payload | Creating malware, exploit development | Malware analysis, patch management |
| Delivery | Transmitting weapon to victim | Phishing emails, malicious attachments | Email filtering, user awareness training |
| Exploitation | Executing attack code on victim system | Exploit vulnerability, macro execution | Vulnerability scanning, endpoint protection |
| Installation | Installing malware for persistence | Dropping backdoors, installing rootkits | Endpoint detection, application whitelisting |
| Command and Control (C2) | Attacker communicates with compromised system | Establishing remote access, beaconing | Network segmentation, intrusion detection systems |
| Actions on Objectives | Achieving attack goals | Data exfiltration, privilege escalation | Data loss prevention, privilege management |
Understanding the Kill Chain Framework in Cybersecurity
The kill chain framework in cybersecurity outlines the stages of a cyberattack, from reconnaissance to actions on objectives, enabling organizations to identify and disrupt threats efficiently. By mapping attacker behavior through phases such as weaponization, delivery, exploitation, installation, command and control, and actions on objectives, defenders can implement targeted countermeasures. Understanding each step in the cyber kill chain enhances threat detection, response times, and overall security posture against advanced persistent threats.
Stages of a Typical Cyber Attack Kill Chain
Reconnaissance involves gathering intelligence on targets through methods like phishing or network scanning to identify vulnerabilities. During the weaponization and delivery stages, attackers craft malicious payloads delivered via email attachments or compromised websites to exploit system weaknesses. Post-exploitation activities include establishing command and control channels, moving laterally across the network, and escalating privileges to maintain persistence and achieve attack objectives.
Real-World Example: Kill Chain Applied in a Phishing Attack
Phishing attacks typically follow the kill chain model, beginning with reconnaissance to gather target information, followed by weaponization where malicious emails are crafted with embedded links or attachments. Delivery occurs when these emails are sent to victims, leading to exploitation as users click on the malicious content, allowing installation of malware or credential harvesting. The adversary then establishes command and control, enabling further actions like data exfiltration or lateral movement within the compromised network.
Reconnaissance: Gathering Intelligence on the Target
Reconnaissance in a cyber kill chain involves attackers collecting detailed information about the target's network topology, software versions, and employee roles using passive and active methods such as social engineering, scanning tools, and open-source intelligence (OSINT) platforms. This intelligence gathering phase enables adversaries to identify vulnerabilities, entry points, and security gaps, setting the stage for subsequent attack phases like delivery and exploitation. Effective reconnaissance detection relies on monitoring unusual network activities, such as anomalous scanning patterns and unauthorized access requests.
Weaponization: Crafting Malicious Payloads
Weaponization in the kill chain involves creating customized malicious payloads designed to exploit specific vulnerabilities in a target system, such as embedding remote access trojans within seemingly benign documents. Attackers use tools like Metasploit to generate these payloads, ensuring they bypass antivirus detection through obfuscation and encryption techniques. This phase is critical for establishing a foothold by delivering payloads that enable subsequent phases like delivery and exploitation in a cyberattack.
Delivery: Transporting the Attack to Victims
The Delivery phase in a cyber kill chain involves transmitting malicious payloads to targeted victims through vectors such as phishing emails, infected USB drives, or malicious websites. Attackers exploit vulnerabilities in email systems or user behavior to ensure the malware reaches its destination, often leveraging social engineering tactics. Effective detection at this stage requires advanced threat intelligence and email filtering technologies to block suspicious attachments and links before execution.
Exploitation: Executing Malicious Code on Victim Systems
Exploitation in the kill chain involves executing malicious code on victim systems to gain unauthorized access or control. This phase commonly employs techniques such as buffer overflow, code injection, or exploitation of software vulnerabilities to breach system defenses. Effective detection and prevention require continuous monitoring for abnormal process execution and leveraging endpoint protection platforms.
Installation: Establishing Persistence within the Target Network
Installation in the kill chain involves deploying malware or backdoors to establish persistence within the target network, ensuring attackers maintain long-term access. This phase often uses techniques such as planting remote access trojans (RATs), creating scheduled tasks, or modifying system services to survive reboots and evade detection. Effective installation enables adversaries to execute further lateral movement, data exfiltration, or command and control (C2) communications undisturbed.
Command and Control (C2): Maintaining Attacker Communication
Command and Control (C2) in the cyber attack kill chain represents the phase where attackers establish and maintain persistent communication channels with compromised systems. This stage leverages protocols and encrypted traffic to evade detection, enabling attackers to control malware remotely and exfiltrate data. Effective C2 infrastructure is critical for attackers to adapt tactics dynamically and extend their presence within targeted networks.
Actions on Objectives: Achieving the Attacker’s End Goals
Actions on Objectives represent the final phase in the cyber kill chain where attackers achieve their desired outcomes such as data exfiltration, system disruption, or persistent access. During this stage, threat actors execute commands, deploy ransomware, or manipulate data to fulfill mission objectives. Effective detection and response at this phase are critical to minimizing damage and restoring normal operations.
example of kill chain in attack Infographic
 samplerz.com
samplerz.com