A notable example of a rootkit in firmware is the LoJax malware, which specifically targets the UEFI (Unified Extensible Firmware Interface) firmware. LoJax is designed to persist on compromised computers even after operating system reinstallation, making it extremely difficult to detect and remove. This rootkit alters the firmware to inject malicious code during the boot process, thereby gaining control before the operating system loads. Firmware rootkits pose a significant security threat because they operate at a low level, below traditional antivirus detection capabilities. Since firmware controls hardware initialization, rootkits like LoJax can manipulate system security features and maintain persistence across reboots. Exploitation of firmware vulnerabilities requires advanced attack techniques, highlighting the importance of firmware integrity checking and secure boot mechanisms in modern cybersecurity strategies.
Table of Comparison
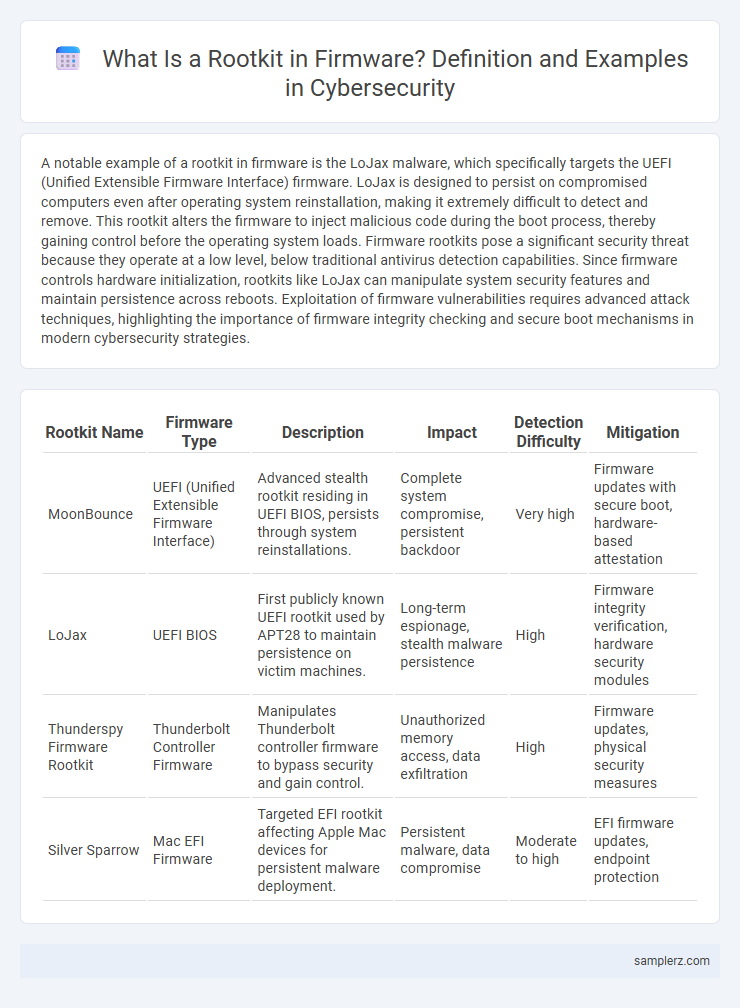
| Rootkit Name | Firmware Type | Description | Impact | Detection Difficulty | Mitigation |
|---|---|---|---|---|---|
| MoonBounce | UEFI (Unified Extensible Firmware Interface) | Advanced stealth rootkit residing in UEFI BIOS, persists through system reinstallations. | Complete system compromise, persistent backdoor | Very high | Firmware updates with secure boot, hardware-based attestation |
| LoJax | UEFI BIOS | First publicly known UEFI rootkit used by APT28 to maintain persistence on victim machines. | Long-term espionage, stealth malware persistence | High | Firmware integrity verification, hardware security modules |
| Thunderspy Firmware Rootkit | Thunderbolt Controller Firmware | Manipulates Thunderbolt controller firmware to bypass security and gain control. | Unauthorized memory access, data exfiltration | High | Firmware updates, physical security measures |
| Silver Sparrow | Mac EFI Firmware | Targeted EFI rootkit affecting Apple Mac devices for persistent malware deployment. | Persistent malware, data compromise | Moderate to high | EFI firmware updates, endpoint protection |
Notorious Firmware Rootkit Attacks in History
Notable firmware rootkit attacks include the Equation Group's use of the EquationDrug rootkit, targeting hard drive firmware to maintain persistent control over affected systems. Another infamous example is the LoJax rootkit, discovered in 2018, which infected UEFI firmware to survive OS reinstalls and provide attackers with stealthy, long-term access. These firmware-level rootkits bypass traditional antivirus detection methods, posing significant challenges for cybersecurity defenses.
Real-World Cases of Firmware-Level Rootkits
The LoJax rootkit, discovered in 2018, is a notable real-world example of a firmware-level rootkit targeting UEFI firmware to maintain persistence and evade detection on infected systems. This malware was used by the Fancy Bear group to compromise victim machines by embedding itself in the system's SPI flash memory, illustrating the growing threat of firmware attacks. The complexity of detecting and removing LoJax highlights the critical security risks posed by firmware rootkits in modern cybersecurity landscapes.
Notable UEFI BIOS Rootkit Examples
Notable UEFI BIOS rootkit examples include LoJax, which targets the Unified Extensible Firmware Interface to maintain persistent control over infected systems, and MosaicRegressor, a highly sophisticated threat capable of stealthily modifying firmware to evade detection. These rootkits exploit vulnerabilities in UEFI firmware, allowing attackers to persist beyond traditional operating system defenses and undermine system integrity at the hardware level. Understanding these examples highlights the critical importance of robust firmware security measures and regular UEFI updates to prevent persistent, low-level malware infections.
Infamous Router Firmware Rootkit Incidents
The VPNFilter malware is a notorious example of a router firmware rootkit that targeted over 500,000 devices globally, exploiting vulnerabilities in home and small business routers. Another infamous incident involved the "LoJax" rootkit, which infected UEFI firmware to maintain persistence beyond operating system reinstallation, primarily used in state-sponsored espionage campaigns. These firmware rootkits compromise network security by embedding themselves at a low level, making detection and removal exceptionally difficult.
Exploited Network Device Firmware Rootkits
Exploited network device firmware rootkits, such as the VPNFilter malware, infiltrate routers and network hardware to maintain persistent control and evade detection. These rootkits manipulate low-level firmware components, allowing attackers to intercept, modify, or reroute network traffic while remaining hidden from conventional security tools. The sophisticated nature of these firmware-level exploits poses significant risks to enterprise and personal network security by enabling prolonged surveillance and data exfiltration.
Malicious Hard Drive Firmware Rootkit Cases
Malicious hard drive firmware rootkits, such as the one discovered in 2015 targeting Seagate and Western Digital drives, manipulate low-level firmware to maintain persistence and evade detection by operating system security measures. These rootkits reside outside the scope of traditional antivirus programs, allowing attackers to exfiltrate data or execute commands stealthily. The challenge of identifying firmware-based rootkits in hard drives highlights the need for specialized forensic tools and hardware-level security protocols.
IoT Device Firmware Rootkit Breaches
IoT device firmware rootkit breaches exploit low-level system access to remain undetected while compromising device integrity and data confidentiality. Notable examples include LoJax, a persistent UEFI rootkit targeting IoT and endpoint devices to maintain stealthy control through firmware manipulation. These breaches enable attackers to bypass traditional security measures, leading to long-lasting infiltration and unauthorized data exfiltration in interconnected environments.
Rootkit-Infected Mobile Firmware Examples
Rootkit-infected mobile firmware examples highlight the increasing threat of persistent firmware-level attacks, such as the LoJax rootkit that infiltrated the UEFI firmware of certain laptops and mobile devices, enabling attackers to maintain stealthy control. Another notable case involves the HackingTeam rootkit embedded in Android device firmware, which allowed covert surveillance and data exfiltration without detection by traditional antivirus solutions. These rootkits demonstrate how compromised firmware can bypass operating system security layers, making detection and removal exceptionally challenging.
Security Cameras Compromised by Firmware Rootkits
Firmware rootkits targeting security cameras manipulate the device's bootloader or firmware to maintain persistent, stealthy access and evade detection by traditional security measures. Exploits such as the Mirai botnet have leveraged vulnerabilities in camera firmware to hijack devices, creating expansive botnets for DDoS attacks. Compromised cameras with rootkits pose severe risks, enabling attackers to intercept video feeds, launch further network intrusions, and undermine physical security systems.
Lessons Learned from Firmware Rootkit Discoveries
Firmware rootkits such as LoJax and MoonBounce highlight the critical importance of securing low-level system components against sophisticated persistent threats. These rootkits exploit firmware vulnerabilities to maintain stealth and survive OS reinstallation or hard drive replacement, emphasizing the need for comprehensive firmware integrity validation and regular security updates. Implementing hardware-based trusted platform modules (TPMs) and conducting continuous firmware monitoring serve as essential countermeasures learned from these advanced firmware rootkit cases.
example of rootkit in firmware Infographic
 samplerz.com
samplerz.com