A cold boot attack exploits vulnerabilities in a computer's memory to extract sensitive data after a system restart. Attackers physically access a device and perform a hard reboot to quickly capture residual data stored in the RAM before it is erased. This technique targets encryption keys, passwords, and other confidential information that remain temporarily accessible following the cold boot. The cold boot attack demonstrates significant risks to data security, especially in environments lacking full-disk encryption or memory protection mechanisms. Researchers have shown that recovered information can compromise entire systems, making this attack relevant to both desktops and laptops. Defense measures include using volatile memory encryption and enforcing strict physical access controls to mitigate the attack vector.
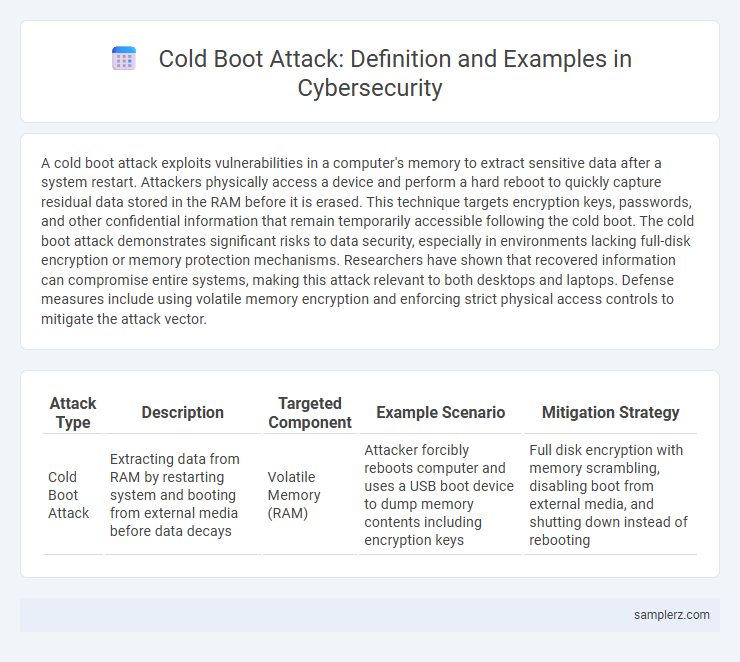
Table of Comparison
| Attack Type | Description | Targeted Component | Example Scenario | Mitigation Strategy |
|---|---|---|---|---|
| Cold Boot Attack | Extracting data from RAM by restarting system and booting from external media before data decays | Volatile Memory (RAM) | Attacker forcibly reboots computer and uses a USB boot device to dump memory contents including encryption keys | Full disk encryption with memory scrambling, disabling boot from external media, and shutting down instead of rebooting |
Understanding Cold Boot Attacks in Cybersecurity
Cold boot attacks exploit the residual data retained in a computer's RAM after a sudden power loss, allowing attackers to retrieve sensitive information such as encryption keys or passwords. This attack method leverages the physical memory's slower decay rate at low temperatures, enabling forensic recovery using tools like memory dumping techniques. Understanding cold boot attacks highlights the importance of securing volatile memory and implementing proper system shutdown procedures to prevent unauthorized data extraction.
The Mechanics Behind Cold Boot Attacks
Cold boot attacks exploit the remanence effect in DRAM, where data persists briefly after power is cut, allowing attackers to recover sensitive information by rapidly rebooting or physically transferring memory modules. By bypassing operating system protections, adversaries extract encryption keys or passwords directly from volatile memory. The attack's effectiveness depends on memory cooling techniques to prolong data retention and specialized tools for memory data extraction.
Real-World Examples of Cold Boot Attacks
Real-world examples of cold boot attacks include the 2008 demonstration by Princeton researchers who extracted encryption keys from a laptop's RAM seconds after a reboot, highlighting vulnerabilities in full-disk encryption. In 2011, Cold Boot Attacks were successfully used to retrieve sensitive data from encryption keys stored in volatile memory of mobile devices, emphasizing risks in mobile security. These incidents underscore the critical need for hardware-level encryption and memory protection techniques to prevent unauthorized data recovery through cold boot exploits.
Cold Boot Attack Techniques and Tactics
Cold boot attack techniques exploit residual data in a computer's RAM by quickly rebooting or physically transferring memory modules to capture sensitive information such as encryption keys. Attackers use tactics like cooling the memory chips with refrigerants to slow data decay, enabling data extraction before it fades completely. This method bypasses typical encryption safeguards by targeting volatile memory immediately after a system shutdown or crash.
Cold Boot Attacks on Laptops: Case Studies
Cold boot attacks on laptops exploit residual data in DRAM by rapidly rebooting or physically transferring memory modules to extract encryption keys and sensitive credentials. Notable case studies highlight successful attacks on BitLocker and FileVault encryption, revealing vulnerabilities in full-disk encryption implementations when systems are left in sleep or hibernation modes. These incidents emphasize the importance of comprehensive memory encryption and hardware-level security features to mitigate risks in portable computing environments.
Data Recovery During Cold Boot Attacks
Cold boot attacks exploit the data remanence property of DRAM by rapidly rebooting a machine and accessing residual data stored in memory before it fades. Attackers can recover encryption keys, passwords, and other sensitive information by freezing memory modules to slow data decay, enabling extraction using specialized tools. This vulnerability highlights the critical need for full memory encryption and limiting physical access to prevent unauthorized data recovery during cold boot scenarios.
Memory Vulnerabilities Exploited by Cold Boot
Cold boot attacks exploit memory vulnerabilities by rapidly rebooting a system and accessing residual data left in RAM, which retains information for several seconds to minutes after power loss. Attackers can extract encryption keys, passwords, or other sensitive data from this remnant memory before it completely decays. This technique highlights critical weaknesses in memory management and encryption key storage that expose systems to post-shutdown data breaches.
Cold Boot Attacks Against Encryption Keys
Cold boot attacks exploit the residual data retained in RAM after a system shutdown or reboot, allowing attackers to extract encryption keys stored in memory. These attacks involve quickly cooling the memory chips to prolong data retention, then transferring the content to another device for analysis. Effective countermeasures include using full-disk encryption with hardware-based key storage and implementing memory scrubbing techniques to erase sensitive data during shutdown.
High-Profile Breaches Involving Cold Boot Attacks
High-profile breaches involving cold boot attacks demonstrate the severity of this threat, with attackers exploiting residual data in RAM to extract encryption keys and sensitive credentials from compromised systems. Notably, the 2008 University of California attack exposed vulnerabilities in full disk encryption by successfully retrieving cryptographic keys through cold boot techniques. These incidents highlight the critical need for robust memory protection and hardware-level encryption to defend against cold boot exploits in securing sensitive data assets.
Preventing and Mitigating Cold Boot Attacks
Cold boot attacks exploit residual data in RAM after a system is powered off, posing significant security risks. Implementing full disk encryption and utilizing memory scrambling techniques help prevent unauthorized data retrieval. Regularly clearing memory on shutdown and employing hardware with built-in encryption modules further mitigate the threat of cold boot attacks.
example of cold boot in attack Infographic
 samplerz.com
samplerz.com