Spear phishing in email security targets specific individuals or organizations by using personalized information to appear legitimate. An example involves a cybercriminal sending an email that appears to come from a company's CEO, requesting urgent financial transactions or confidential data. These emails often include details like the recipient's name, job title, or recent projects, increasing the likelihood of successful deception. Such attacks exploit trust and familiarity, manipulating recipients into clicking malicious links or downloading infected attachments. Security teams rely on advanced threat detection systems and employee training to identify and prevent spear phishing attempts. Email security tools analyze sender information, message context, and unusual request patterns to mitigate these targeted risks effectively.
Table of Comparison
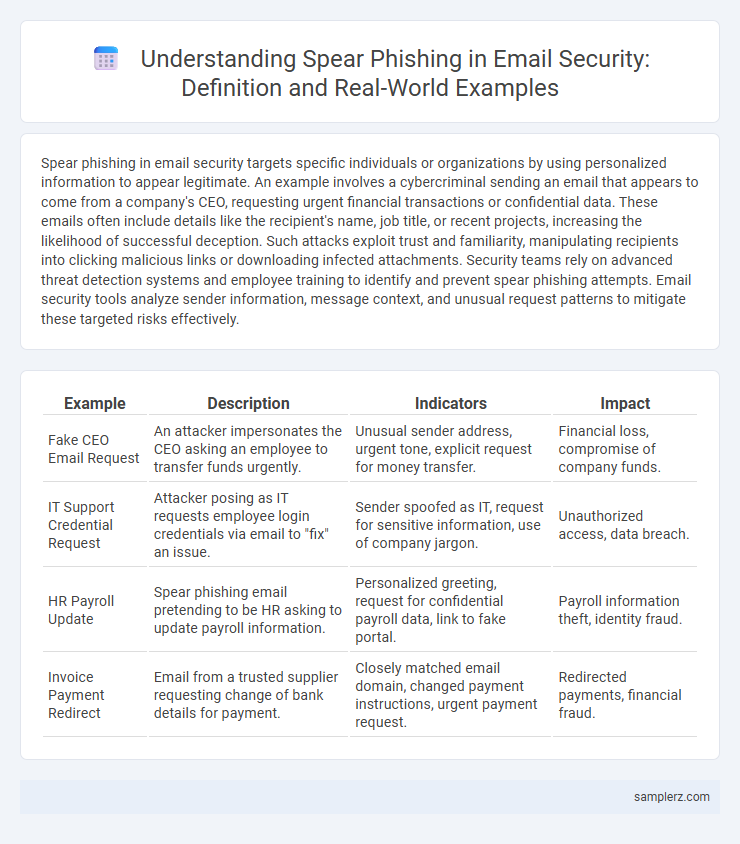
| Example | Description | Indicators | Impact |
|---|---|---|---|
| Fake CEO Email Request | An attacker impersonates the CEO asking an employee to transfer funds urgently. | Unusual sender address, urgent tone, explicit request for money transfer. | Financial loss, compromise of company funds. |
| IT Support Credential Request | Attacker posing as IT requests employee login credentials via email to "fix" an issue. | Sender spoofed as IT, request for sensitive information, use of company jargon. | Unauthorized access, data breach. |
| HR Payroll Update | Spear phishing email pretending to be HR asking to update payroll information. | Personalized greeting, request for confidential payroll data, link to fake portal. | Payroll information theft, identity fraud. |
| Invoice Payment Redirect | Email from a trusted supplier requesting change of bank details for payment. | Closely matched email domain, changed payment instructions, urgent payment request. | Redirected payments, financial fraud. |
Definition and Overview of Spear Phishing
Spear phishing is a highly targeted email attack designed to deceive specific individuals or organizations by masquerading as a trusted source. Unlike generic phishing, spear phishing uses personalized information to increase the likelihood of victims opening malicious attachments or links. This cyber threat often aims to steal sensitive data, gain unauthorized access, or deploy malware within enterprise networks.
How Spear Phishing Differs from Regular Phishing
Spear phishing targets specific individuals or organizations by using personalized information to increase the likelihood of success, unlike regular phishing which relies on mass distribution of generic messages. Attackers often research their targets thoroughly, exploiting tailored content such as names, job titles, or company projects to create convincing emails. This precision makes spear phishing more difficult to detect and more dangerous than traditional phishing attacks.
Notable Real-World Spear Phishing Incidents
The 2016 Democratic National Committee email breach remains one of the most notable spear phishing incidents, where attackers used highly targeted emails to deceive staff into revealing login credentials, leading to significant political and cybersecurity consequences. Another prominent case occurred with the CEO fraud attack on FACC GmbH in 2016, where spear phishing emails impersonated executives and resulted in a fraudulent transfer of EUR50 million. These attacks highlight the critical need for advanced email security protocols and continuous user awareness training to defend against sophisticated spear phishing strategies.
Anatomy of a Spear Phishing Email
A spear phishing email typically includes personalized information such as the recipient's name, job title, or recent activities to appear legitimate and increase trust. The email often contains a convincing call to action, such as clicking a malicious link or downloading an infected attachment masquerading as a business document. Headers may be spoofed to mimic trusted sources, and the message tone is urgent or authoritative to prompt immediate response without scrutiny.
Common Tactics Used in Spear Phishing Attacks
Spear phishing attacks commonly use personalized information and social engineering tactics to deceive targets, such as referencing recent transactions or mimicking trusted contacts to establish legitimacy. Attackers often embed malicious links or attachments designed to install malware or steal credentials upon interaction. These highly targeted emails leverage detailed knowledge about the victim's role, relationships, and interests to increase the likelihood of success.
Indicators of Spear Phishing in Email Communication
Spear phishing in email security can be identified by several indicators such as personalized greetings using the recipient's name, urgent or threatening language prompting immediate action, and suspicious sender addresses that mimic legitimate sources. Emails often contain unexpected attachments or embedded links that lead to fraudulent websites designed to steal credentials or install malware. Detailed analysis of metadata, including IP addresses and email headers, can reveal discrepancies pointing to targeted cyberattacks aimed at specific individuals or organizations.
Case Study: High-Profile Spear Phishing Example
A high-profile spear phishing case involved a 2016 attack on a major US political organization where attackers crafted personalized emails mimicking trusted contacts, leading to unauthorized access to sensitive emails. The attackers used detailed information from social media and previous breaches to enhance the email's credibility, bypassing typical spam filters. This attack highlighted the critical need for multi-factor authentication and employee training to recognize targeted phishing attempts in email security protocols.
Impact of Spear Phishing on Organizations
Spear phishing attacks target specific employees by using personalized information to deceive recipients, often resulting in unauthorized access to sensitive data or financial loss. These attacks can lead to significant operational disruptions, reputational damage, and costly regulatory fines for organizations. Effective email security measures and employee training are crucial to mitigate the impact of spear phishing on corporate networks.
Prevention Strategies Against Spear Phishing
Implementing multi-factor authentication (MFA) significantly reduces the risk of unauthorized access in spear phishing attacks by adding an extra verification layer beyond passwords. Employee training programs emphasizing the recognition of suspicious email indicators, such as unexpected sender addresses and urgent action requests, enhance organizational defense against targeted phishing attempts. Utilizing advanced email filtering solutions with machine learning capabilities helps identify and block spear phishing emails before reaching end-users, effectively minimizing potential breaches.
Steps to Take After a Spear Phishing Attack
After a spear phishing attack, immediately isolate affected devices to prevent malware spread and conduct a thorough system scan using updated antivirus tools. Notify the IT security team and change all compromised passwords, prioritizing multi-factor authentication to strengthen account defenses. Document the incident details and report the attack to relevant authorities such as the Cybersecurity and Infrastructure Security Agency (CISA) for further guidance and threat intelligence sharing.
example of spear phishing in email security Infographic
 samplerz.com
samplerz.com