Shibboleth is an open-source software project that provides Single Sign-On (SSO) and federated identity-based access control. It allows organizations to securely share web resources across multiple domains while authenticating users through their home institution's identity provider. Shibboleth uses Security Assertion Markup Language (SAML) to exchange authentication and authorization data between identity providers and service providers. In access control scenarios, Shibboleth enables users to access protected applications without needing multiple logins by leveraging their existing credentials. It facilitates attribute-based access control by passing user attributes, such as group membership or role, to the service provider for authorization decisions. This system enhances security by centralizing identity management and reducing password proliferation across services.
Table of Comparison
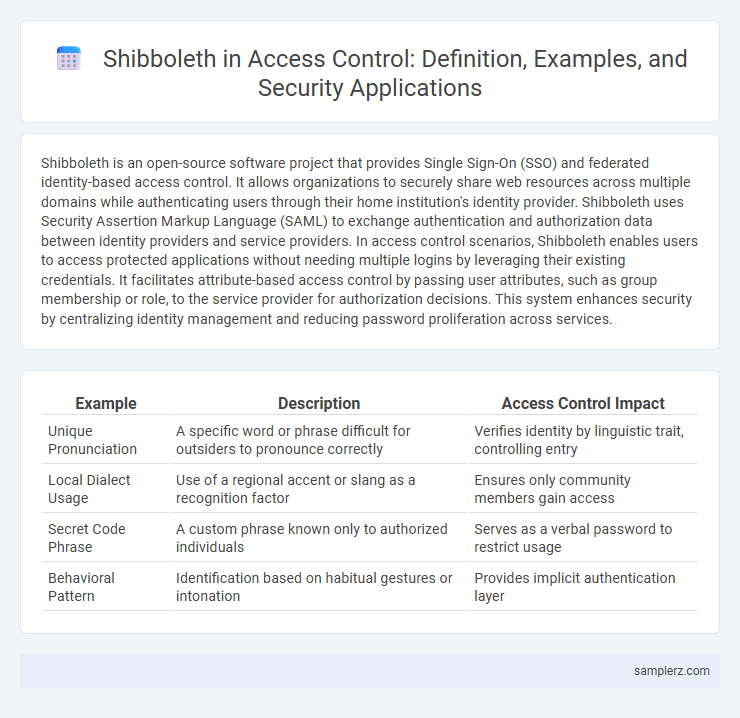
| Example | Description | Access Control Impact |
|---|---|---|
| Unique Pronunciation | A specific word or phrase difficult for outsiders to pronounce correctly | Verifies identity by linguistic trait, controlling entry |
| Local Dialect Usage | Use of a regional accent or slang as a recognition factor | Ensures only community members gain access |
| Secret Code Phrase | A custom phrase known only to authorized individuals | Serves as a verbal password to restrict usage |
| Behavioral Pattern | Identification based on habitual gestures or intonation | Provides implicit authentication layer |
Understanding Shibboleth in Modern Access Control
Shibboleth is a prominent open-source identity federation system widely adopted for single sign-on (SSO) and attribute-based access control in academic and enterprise environments. By enabling secure, privacy-preserving user authentication across multiple domains, Shibboleth integrates seamlessly with federated identity providers to enforce access policies based on user attributes. This approach enhances security by minimizing password exposure and streamlining access management for distributed resources.
Historical Origins of Shibboleth as a Security Mechanism
Shibboleth originated as a linguistic security mechanism in the Hebrew Bible, used to distinguish members of two groups based on pronunciation during wartime, preventing unauthorized access to secure areas. This concept evolved into a modern identity federation system, enabling secure single sign-on (SSO) and attribute-based access control in distributed environments. Its historical roots emphasize the importance of unique identifiers in verifying user authenticity and controlling resource access.
Real-World Examples of Shibboleth in Digital Authentication
Shibboleth is widely used in academic institutions for single sign-on (SSO), enabling secure access to multiple university resources with one authentication, exemplified by its deployment in the InCommon Federation across U.S. higher education. Major research networks implement Shibboleth to facilitate federated identity management, ensuring seamless, privacy-preserving access to restricted digital libraries and databases. Healthcare organizations leverage Shibboleth for controlled user access to patient records, complying with strict security and regulatory standards like HIPAA.
Shibboleth vs. Traditional Password-Based Access
Shibboleth leverages federated identity management to enable secure, single sign-on (SSO) access across multiple organizations without sharing passwords, significantly reducing the risk of credential theft common in traditional password-based access systems. Instead of relying on user-managed passwords, Shibboleth uses SAML (Security Assertion Markup Language) to authenticate users through trusted identity providers, enhancing both security and user experience. This approach eliminates the vulnerabilities of password reuse and phishing attacks, making it a robust solution for secure access control in distributed environments.
Use Cases: Shibboleth in Higher Education Access Control
Shibboleth is widely implemented in higher education institutions to facilitate secure, federated access control across multiple campus services and external academic resources. It enables single sign-on (SSO) capabilities, allowing students and faculty to use one set of credentials to access diverse platforms such as learning management systems, research databases, and library services. This federated identity management enhances privacy and security by minimizing password exposure and supporting attribute-based access policies tailored to user roles within the academic environment.
Benefits of Shibboleth for Federated Identity Management
Shibboleth enhances federated identity management by enabling seamless single sign-on (SSO) across multiple organizations, streamlining user access without compromising security. Its use of secure, standards-based protocols like SAML ensures robust authentication and fine-grained access control while maintaining user privacy through attribute-based access decisions. Organizations benefit from reduced administrative overhead, improved user experience, and strengthened trust relationships in distributed environments.
Implementing Shibboleth in Enterprise Systems
Implementing Shibboleth in enterprise systems enhances access control by enabling secure single sign-on (SSO) across multiple applications and domains using SAML (Security Assertion Markup Language) protocols. This federated identity solution facilitates seamless user authentication and attribute exchange between identity providers (IdP) and service providers (SP), ensuring strict authorization based on user roles and policies. By integrating Shibboleth, organizations achieve scalable, centralized access management that reduces security risks and improves compliance with industry standards such as GDPR and HIPAA.
Security Challenges Associated with Shibboleth
Shibboleth, a widely used single sign-on (SSO) system, faces security challenges including the risk of identity federation vulnerabilities that can expose sensitive user data across multiple platforms. Its reliance on metadata exchange and trust relationships between identity providers and service providers presents attack surfaces susceptible to spoofing or man-in-the-middle attacks. Ensuring robust encryption, strict policy enforcement, and continual monitoring is critical to mitigate potential unauthorized access and maintain the integrity of the authentication process.
Best Practices for Deploying Shibboleth Solutions
Implementing Shibboleth for access control requires rigorous adherence to security best practices such as ensuring robust metadata management, enforcing strict attribute release policies, and regularly updating federation configurations to mitigate vulnerabilities. Integrating multi-factor authentication (MFA) enhances identity assurance, while conducting comprehensive testing in staging environments prevents misconfigurations in production. Consistent monitoring and auditing of Shibboleth logs facilitate quick detection of unauthorized access attempts and strengthen overall security posture.
Future Trends: Shibboleth in Evolving Access Control Frameworks
Shibboleth is advancing access control frameworks by integrating adaptive authentication methods and supporting decentralized identity models. Its future trends emphasize enhanced interoperability with emerging zero trust architectures and identity federation standards to ensure secure, seamless user access across diverse platforms. Continued adoption of AI-driven risk assessment within Shibboleth promises dynamic, context-aware authorization for next-generation security environments.
example of shibboleth in access control Infographic
 samplerz.com
samplerz.com