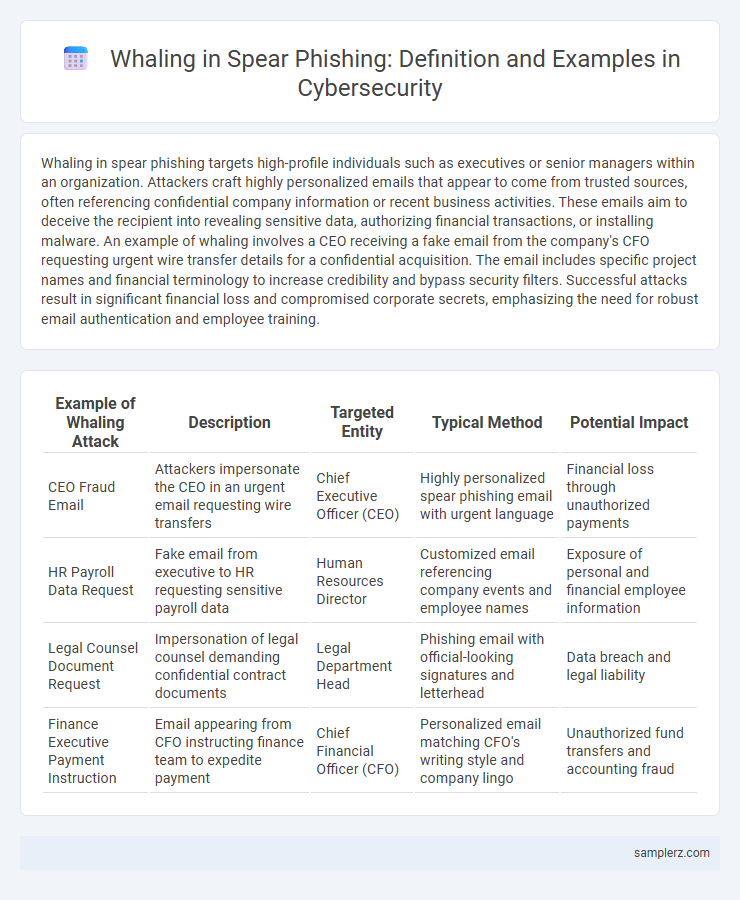
Whaling in spear phishing targets high-profile individuals such as executives or senior managers within an organization. Attackers craft highly personalized emails that appear to come from trusted sources, often referencing confidential company information or recent business activities. These emails aim to deceive the recipient into revealing sensitive data, authorizing financial transactions, or installing malware. An example of whaling involves a CEO receiving a fake email from the company's CFO requesting urgent wire transfer details for a confidential acquisition. The email includes specific project names and financial terminology to increase credibility and bypass security filters. Successful attacks result in significant financial loss and compromised corporate secrets, emphasizing the need for robust email authentication and employee training.
Table of Comparison
| Example of Whaling Attack | Description | Targeted Entity | Typical Method | Potential Impact |
|---|---|---|---|---|
| CEO Fraud Email | Attackers impersonate the CEO in an urgent email requesting wire transfers | Chief Executive Officer (CEO) | Highly personalized spear phishing email with urgent language | Financial loss through unauthorized payments |
| HR Payroll Data Request | Fake email from executive to HR requesting sensitive payroll data | Human Resources Director | Customized email referencing company events and employee names | Exposure of personal and financial employee information |
| Legal Counsel Document Request | Impersonation of legal counsel demanding confidential contract documents | Legal Department Head | Phishing email with official-looking signatures and letterhead | Data breach and legal liability |
| Finance Executive Payment Instruction | Email appearing from CFO instructing finance team to expedite payment | Chief Financial Officer (CFO) | Personalized email matching CFO's writing style and company lingo | Unauthorized fund transfers and accounting fraud |
Real-World Whaling Attacks: Notable Incidents in History
Real-world whaling attacks include the 2016 breach of the Panama Papers, where attackers spoofed a law firm's CEO email to extract sensitive documents. In 2011, RSA Security fell victim to a whaling attack targeting executives, leading to a major data breach that compromised their SecurID tokens. These incidents highlight the high stakes and precision tactics used in whaling campaigns exploiting executive-level trust.
High-Profile CEOs Targeted by Spear Phishing Whaling
High-profile CEOs are prime targets in spear phishing whaling attacks, where cybercriminals craft personalized emails mimicking trusted sources to deceive executives into divulging sensitive information. These attacks often exploit public data found on social media and company websites to increase credibility and success rates. Major incidents targeting CEOs of Fortune 500 companies demonstrate how attackers leverage whaling to gain unauthorized access to corporate networks and financial assets.
Financial Sector Whaling: Breaches and Consequences
Financial sector whaling attacks specifically target high-level executives such as CFOs to steal sensitive fiscal data or authorize fraudulent wire transfers. Successful breaches often lead to significant financial losses, regulatory penalties, and erosion of client trust. For example, the 2016 attack on a major investment bank resulted in a $81 million fraudulent transfer, highlighting the severe consequences of whaling in spear phishing within the financial industry.
Whaling in Government: Senior Officials Under Attack
Whaling in government targets senior officials through highly personalized spear phishing attacks designed to deceive high-ranking personnel into revealing sensitive information or approving fraudulent transactions. These attacks often leverage detailed knowledge of government operations and official communications to gain trust and bypass traditional security measures. Successful whaling exploits can lead to data breaches, national security threats, and significant financial losses within public sector institutions.
Email Fraud Against Executives: Recent Whaling Examples
Recent whaling attacks target high-level executives through sophisticated spear phishing emails that mimic trusted internal communications or vendors. For instance, a 2023 incident involved CFOs receiving fraudulent wire transfer requests disguised as urgent CEO instructions, resulting in multi-million dollar losses. These email fraud schemes exploit executives' authority and access, making whaling a critical threat in enterprise cybersecurity defenses.
Cybercriminal Tactics: Constructing Convincing Whaling Emails
Cybercriminals employ whaling in spear phishing by meticulously crafting emails that impersonate high-level executives or trusted partners, leveraging specific organizational knowledge to enhance credibility. These targeted emails often contain urgent requests for sensitive information or financial transfers, exploiting the victim's authority and trust within the company. Advanced tactics include using personalized language, mimicking corporate email formats, and embedding malicious links or attachments to bypass security filters and maximize response likelihood.
Data Breach Scenarios: Spear Phishing Whaling in Corporations
Whaling attacks in spear phishing specifically target high-profile corporate executives to steal sensitive information and deploy malicious payloads, often resulting in significant data breaches. Attackers craft highly personalized emails that mimic legitimate communications, exploiting executive roles to gain access to confidential financial records or strategic plans. These breaches frequently lead to severe financial losses, regulatory penalties, and compromised intellectual property in major corporations.
Case Studies: Whaling Attacks on Global Enterprises
Whaling attacks on global enterprises often target high-level executives through highly personalized spear phishing campaigns that exploit business communication channels. For example, in 2016, the FACC AG case involved attackers impersonating the CEO in emails, resulting in a fraudulent transfer of $50 million. These incidents highlight the critical need for advanced email authentication protocols and executive cybersecurity training to mitigate whaling risks effectively.
Social Engineering in Whaling: Manipulating Executive Trust
Whaling in spear phishing targets high-level executives by exploiting social engineering techniques that manipulate their trust and sense of authority. Attackers craft personalized emails that appear legitimate, often mimicking trusted business contacts or urgent company matters to deceive executives into revealing sensitive information. This sophisticated manipulation leverages psychological tactics, making whaling a potent threat to corporate security and confidential data.
Lessons Learned from Famous Whaling Events
The whaling attack on the FACC CEO in 2016 highlighted the critical importance of multi-factor authentication and employee training in preventing spear phishing scams targeting high-level executives. The Ubiquiti Networks incident, which resulted in a $46.7 million loss, emphasized the need for rigorous verification protocols for wire transfer requests. These high-profile cases demonstrate that comprehensive cybersecurity policies and awareness programs are essential to defend against sophisticated whaling threats.
example of whaling in spear phishing Infographic
 samplerz.com
samplerz.com