An air gap in network defense refers to a security measure where a computer or network is physically isolated from unsecured networks, including the internet. This isolation prevents data from being transferred electronically between the secured system and other networks, effectively minimizing the risk of cyberattacks. For example, military networks often employ air gaps to protect sensitive information by disconnecting classified systems from external access. The use of air gaps is common in critical infrastructure sectors such as energy, finance, and government agencies, where data confidentiality and integrity are paramount. Data transfer in air-gapped systems typically occurs through physical media like USB drives or external hard disks, which are strictly controlled to prevent malware introduction. This approach ensures that even if a connected network is compromised, the air-gapped system remains protected from unauthorized digital access.
Table of Comparison
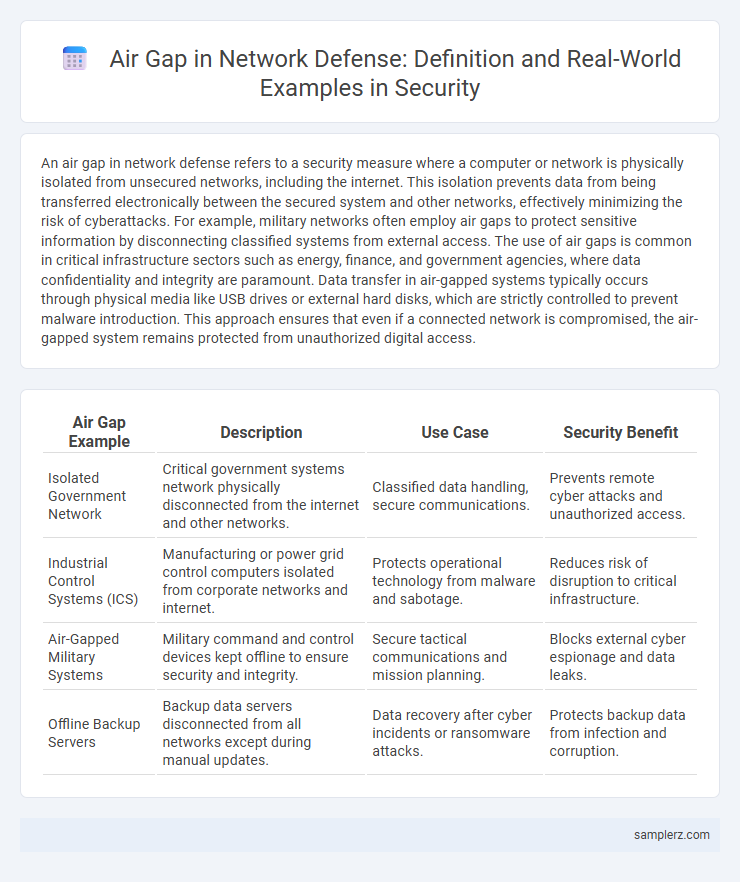
| Air Gap Example | Description | Use Case | Security Benefit |
|---|---|---|---|
| Isolated Government Network | Critical government systems network physically disconnected from the internet and other networks. | Classified data handling, secure communications. | Prevents remote cyber attacks and unauthorized access. |
| Industrial Control Systems (ICS) | Manufacturing or power grid control computers isolated from corporate networks and internet. | Protects operational technology from malware and sabotage. | Reduces risk of disruption to critical infrastructure. |
| Air-Gapped Military Systems | Military command and control devices kept offline to ensure security and integrity. | Secure tactical communications and mission planning. | Blocks external cyber espionage and data leaks. |
| Offline Backup Servers | Backup data servers disconnected from all networks except during manual updates. | Data recovery after cyber incidents or ransomware attacks. | Protects backup data from infection and corruption. |
Understanding Air Gaps in Network Defense
Air gaps in network defense physically isolate critical systems from unsecured networks, preventing unauthorized data transfer and cyberattacks. This method is commonly employed in military, government, and industrial control systems where maximum security is essential. By eliminating direct or wireless connectivity, air gaps reduce the attack surface, mitigating risk from malware and remote hacking attempts.
Real-World Scenarios Utilizing Air Gaps
Air gaps are effectively utilized in high-security environments such as military defense systems, where isolated networks prevent unauthorized access and data breaches. Industrial control systems (ICS) for critical infrastructure like power grids often employ air gaps to mitigate cyber threats by physically separating operational technology from external networks. Financial institutions also use air-gapped devices to securely manage sensitive information, ensuring a hardened defense against cyberattacks and data exfiltration.
Physical Isolation: Classic Air Gap Implementations
Classic air gap implementations in network defense rely on physical isolation by completely disconnecting critical systems from unsecured networks, ensuring no direct or indirect digital communication channels exist. These air-gapped environments are commonly used in military, industrial control systems, and high-security government installations to prevent remote cyber intrusions. Physical isolation involves dedicated hardware, separate data transfer protocols, and strict access controls to maintain the integrity of sensitive data and critical operations.
Air Gap Strategies in Critical Infrastructure
Air gap strategies in critical infrastructure involve physically isolating sensitive systems from unsecured networks to prevent cyber threats and unauthorized access. Critical sectors like power grids, water treatment facilities, and nuclear plants implement air gaps by disconnecting control systems from the internet and external networks, ensuring data cannot be exfiltrated remotely. These measures strengthen cybersecurity by creating an isolated environment that significantly lowers the risk of malware infiltration and cyberattacks.
Air Gaps for Industrial Control Systems Security
Air gaps are a critical security measure in industrial control systems (ICS), physically isolating networks to prevent remote access and cyber threats. By disconnecting critical ICS components from the internet and unsecured networks, air gaps mitigate risks from ransomware, malware, and espionage targeting operational technology (OT) environments. This isolation enhances security by ensuring sensitive industrial processes remain unaffected by external cyberattacks and unauthorized data exfiltration.
Financial Sector: Protecting Assets with Air Gaps
Financial institutions implement air gaps by isolating critical systems such as payment processing and customer data storage from corporate networks to prevent cyber intrusions. This physical separation ensures sensitive financial assets remain unreachable from external threats and malware propagation. Air gaps are essential in mitigating ransomware risks and maintaining regulatory compliance in protecting financial sector infrastructure.
Military and Government Applications of Air Gaps
Military and government networks employ air gaps to isolate critical systems from external internet access, preventing cyber intrusions and data breaches. These isolated environments ensure that classified information remains secure by physically separating operational technology from unsecured networks. Air gaps are crucial for safeguarding defense communications, command and control systems, and intelligence databases against sophisticated cyber threats.
Preventing Data Exfiltration with Air Gaps
Air gaps in network defense create physically isolated systems, ensuring no direct or wireless connection exists between secure and less secure networks. This physical separation effectively prevents data exfiltration by eliminating pathways for unauthorized data transfer or cyberattacks. Critical infrastructures like military networks and industrial control systems frequently use air gaps to maintain maximum security against external breaches.
Limitations and Risks of Air Gap Solutions
Air gap solutions isolate critical systems from unsecured networks by physically separating devices, reducing exposure to cyber threats. However, limitations include difficulties in transferring data securely, increased operational complexity, and vulnerabilities through insider threats or compromised removable media. Despite strong isolation, air gaps cannot fully prevent breaches caused by sophisticated attacks exploiting human error or covert channels.
Emerging Threats Targeting Air Gapped Networks
Emerging threats targeting air-gapped networks include advanced cyber espionage techniques leveraging electromagnetic, acoustic, and optical covert channels to exfiltrate sensitive data without direct network connections. Malicious actors exploit vulnerabilities in hardware components such as graphics cards, USB devices, and compromised firmware to bridge isolated systems covertly. Continuous monitoring of air-gap breaches requires specialized countermeasures like anomaly detection in emanations and strict physical security protocols to maintain the integrity of isolated networks.
example of air gap in network defense Infographic
 samplerz.com
samplerz.com