A zero-day malware exploit targets vulnerabilities in software that are unknown to the vendor or security community. For example, the Stuxnet worm, discovered in 2010, utilized multiple zero-day exploits to infiltrate and sabotage Iranian nuclear facilities. This malware exploited vulnerabilities in Windows operating systems that had not been previously identified or patched, allowing it to spread undetected. Zero-day attacks pose significant risks because there are no existing defenses or patches at the time of exploitation. They often leverage unknown flaws in widely used software such as Windows, Adobe Flash, or browsers. Organizations must rely on advanced threat detection systems and behavior analysis to identify and mitigate zero-day malware threats before official patches become available.
Table of Comparison
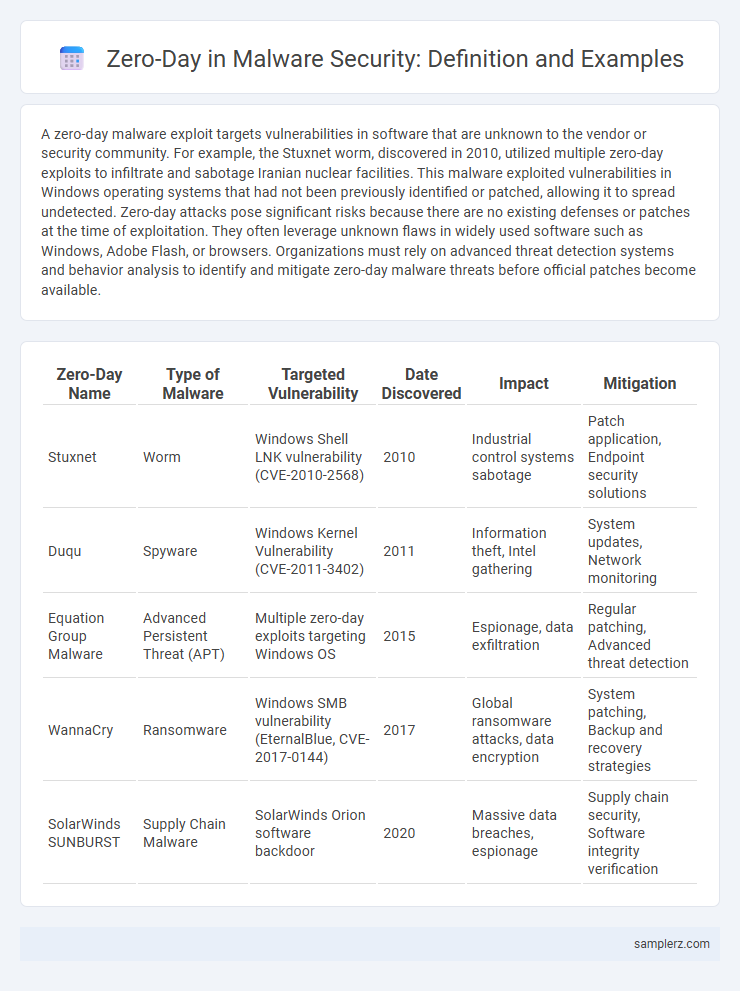
| Zero-Day Name | Type of Malware | Targeted Vulnerability | Date Discovered | Impact | Mitigation |
|---|---|---|---|---|---|
| Stuxnet | Worm | Windows Shell LNK vulnerability (CVE-2010-2568) | 2010 | Industrial control systems sabotage | Patch application, Endpoint security solutions |
| Duqu | Spyware | Windows Kernel Vulnerability (CVE-2011-3402) | 2011 | Information theft, Intel gathering | System updates, Network monitoring |
| Equation Group Malware | Advanced Persistent Threat (APT) | Multiple zero-day exploits targeting Windows OS | 2015 | Espionage, data exfiltration | Regular patching, Advanced threat detection |
| WannaCry | Ransomware | Windows SMB vulnerability (EternalBlue, CVE-2017-0144) | 2017 | Global ransomware attacks, data encryption | System patching, Backup and recovery strategies |
| SolarWinds SUNBURST | Supply Chain Malware | SolarWinds Orion software backdoor | 2020 | Massive data breaches, espionage | Supply chain security, Software integrity verification |
Introduction to Zero-Day Vulnerabilities in Malware
Zero-day vulnerabilities refer to previously unknown software flaws exploited by attackers before developers release patches, often leading to severe security breaches. Notable examples include the Stuxnet worm, which leveraged multiple zero-day exploits to target Iranian nuclear facilities, and the WannaCry ransomware that propagated through a zero-day SMB vulnerability. Understanding zero-day exploits in malware is critical for developing proactive threat detection and response strategies.
Defining Zero-Day Exploits and Their Impact
Zero-day exploits are cyber attacks that target previously unknown vulnerabilities in software, leaving no time for developers to release patches or defenses. A prominent example is the Stuxnet worm, which exploited multiple zero-day vulnerabilities to disrupt Iran's nuclear program, highlighting the extensive damage such attacks can inflict. These exploits pose significant risks to organizations by enabling unauthorized access, data breaches, and operational disruptions before detection or mitigation is possible.
Real-World Zero-Day Malware Attack Cases
Notable real-world zero-day malware attacks include the Stuxnet worm, which exploited multiple zero-day vulnerabilities to target Iranian nuclear facilities, causing physical damage to centrifuges. Another example is the WannaCry ransomware outbreak that utilized a leaked Windows SMB zero-day exploit, backdooring thousands of systems globally and causing widespread disruption. These incidents highlight the critical importance of timely patch management and advanced threat detection in cybersecurity defenses.
Notorious Zero-Day Malware: Recent Examples
Notorious zero-day malware such as Stuxnet exploited unknown vulnerabilities to launch highly sophisticated attacks on industrial control systems, causing physical damage and widespread disruption. Recent examples include the SolarWinds supply chain attack, where attackers leveraged zero-day vulnerabilities to infiltrate government networks, compromising sensitive data on an unprecedented scale. These zero-day exploits highlight the urgent need for proactive threat detection and comprehensive patch management strategies.
How Attackers Deploy Zero-Day Malware
Attackers deploy zero-day malware by exploiting undisclosed software vulnerabilities before developers release patches, allowing unauthorized access or control over target systems. They often leverage sophisticated delivery methods such as spear-phishing emails, drive-by downloads, or malicious attachments to infiltrate networks stealthily. Once inside, zero-day malware can execute payloads that compromise data integrity, evade detection, and establish persistent access for ongoing cyberattacks.
Zero-Day Vulnerabilities Exploited in Ransomware
Zero-day vulnerabilities are critical security flaws unknown to software vendors and are frequently exploited in ransomware attacks to gain unauthorized access and deploy malicious payloads. Notable examples include the EternalBlue exploit, which targeted a Windows SMB protocol vulnerability, enabling the spread of WannaCry ransomware in 2017, causing widespread disruption. Exploiting zero-day vulnerabilities allows ransomware operators to bypass security measures, encrypt victim data, and demand ransom payments before patches are developed or deployed.
Indicators of Zero-Day Malware Infections
Indicators of zero-day malware infections include unusual network traffic patterns, unexpected system behavior, and anomalies in application performance. Security logs may reveal unexplained privilege escalations or unauthorized access attempts, while endpoint detection tools often detect unknown file hashes or suspicious code executions. Monitoring behavior-based indicators and leveraging threat intelligence can help identify zero-day exploits before signature-based detection methods are effective.
Security Gaps Exposed by Zero-Day Threats
Zero-day threats expose critical security gaps by targeting undisclosed vulnerabilities in software before patches are available, allowing attackers to exploit systems undetected. Notable examples include the WannaCry ransomware, which leveraged a zero-day exploit in Windows SMB protocol, causing widespread disruption across global networks. These threats highlight the urgent need for proactive vulnerability management and robust intrusion detection systems to mitigate risks associated with unknown malware attacks.
Zero-Day Malware Detection Techniques
Zero-day malware exploits unknown vulnerabilities, making its detection critical for cybersecurity defense. Techniques such as behavior-based analysis monitor suspicious activities and anomalies in system operations to identify zero-day threats early. Machine learning algorithms enhance detection accuracy by analyzing vast data sets to uncover novel malware patterns without relying on existing signatures.
Mitigating Risks from Zero-Day Malware
Zero-day malware exploits previously unknown vulnerabilities, making traditional signature-based defenses ineffective. Employing behavior-based detection systems and sandboxing techniques enables early identification and containment of suspicious activities before widespread impact occurs. Continuous threat intelligence sharing and timely patch management further reduce exposure to zero-day risks by closing attack vectors proactively.
example of zero-day in malware Infographic
 samplerz.com
samplerz.com