An air-gap in a datacenter refers to the physical separation of secure systems from unsecured networks to prevent unauthorized data access or cyber attacks. This setup often involves isolating critical servers or storage devices by ensuring no direct or indirect network connections exist between them and external or less secure internal networks. Air-gapped datacenters utilize hardware isolation, dedicated cabling, and controlled access environments to maintain data confidentiality and integrity. In practice, air-gap implementations can be seen in government or military datacenters, where sensitive information requires protection against cyber espionage. These datacenters may rely on manual data transfers via removable media, strict physical security controls, and continuous monitoring to enforce the air-gap. The presence of an air-gap significantly reduces the risk of ransomware, malware infiltration, or external digital threats by eliminating network pathways for attack vectors.
Table of Comparison
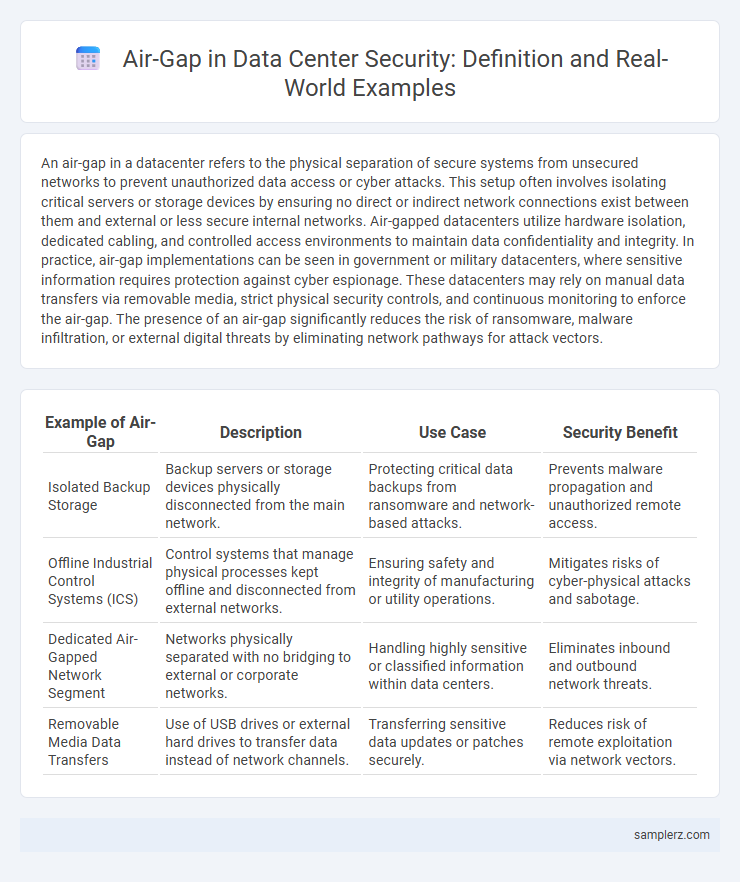
| Example of Air-Gap | Description | Use Case | Security Benefit |
|---|---|---|---|
| Isolated Backup Storage | Backup servers or storage devices physically disconnected from the main network. | Protecting critical data backups from ransomware and network-based attacks. | Prevents malware propagation and unauthorized remote access. |
| Offline Industrial Control Systems (ICS) | Control systems that manage physical processes kept offline and disconnected from external networks. | Ensuring safety and integrity of manufacturing or utility operations. | Mitigates risks of cyber-physical attacks and sabotage. |
| Dedicated Air-Gapped Network Segment | Networks physically separated with no bridging to external or corporate networks. | Handling highly sensitive or classified information within data centers. | Eliminates inbound and outbound network threats. |
| Removable Media Data Transfers | Use of USB drives or external hard drives to transfer data instead of network channels. | Transferring sensitive data updates or patches securely. | Reduces risk of remote exploitation via network vectors. |
Introduction to Air-Gap Security in Datacenters
Air-gap security in datacenters involves physically isolating critical systems from unsecured networks to prevent unauthorized access and cyber threats. This method ensures that sensitive data and operations remain disconnected from the internet or other external networks, enhancing protection against hacking and malware. Common applications include isolated backup servers, secure enclave environments, and control systems that require maximum integrity and confidentiality.
Key Principles of Air-Gapped Datacenter Architecture
Air-gapped datacenter architecture enforces physical and logical isolation by disconnecting critical systems from external networks, preventing unauthorized access and cyber threats. This architecture employs stringent access controls, including dedicated authentication mechanisms and controlled data transfer protocols, to maintain the integrity and confidentiality of sensitive information. Redundant power supplies and environmental controls ensure operational resilience, enhancing the datacenter's security posture against both digital and physical vulnerabilities.
Real-World Air-Gap Deployment Scenarios
Real-world air-gap deployment scenarios in datacenters involve physically isolating critical network segments to prevent cyberattacks and data breaches. Examples include secure government facilities where classified information is stored on disconnected servers and financial institutions using air-gapped systems for transaction processing to ensure maximum data integrity. This physical separation enhances security by eliminating any direct network connection, significantly reducing the attack surface.
Physical Isolation: Air-Gap Implementation Methods
Physical isolation in datacenters is achieved through air-gap implementation methods, which involve completely separating critical systems from external networks to prevent unauthorized access. Common techniques include physically disconnecting network cables, using standalone hardware without any network interfaces, and placing systems within secured, access-controlled environments. This air-gap approach effectively mitigates cyber threats by eliminating digital communication channels between sensitive infrastructure and external devices.
Case Study: Air-Gapped Datacenter for Critical Infrastructure
A prime example of air-gap implementation is the datacenter supporting critical infrastructure at a major utility provider, where isolated network architecture ensures complete physical and logical separation from external internet connections. This design leverages dedicated hardware security modules (HSMs), multi-factor authentication, and rigorous access control policies to safeguard sensitive operational technology (OT) systems against cyber threats. Real-time monitoring and periodic manual data transfers through encrypted removable media maintain operational continuity while preserving the air-gap integrity.
Data Transfer Techniques in Air-Gapped Environments
Air-gapped datacenters utilize secure data transfer techniques such as using removable media like encrypted USB drives, optical discs, or secure transfer stations to physically move data between isolated networks. Optical data transfer systems, including QR codes or optical fibers, are implemented to minimize electronic bridging risks. Strict protocols, including multi-layer encryption and manual inspection, ensure data integrity and prevent unauthorized access during transfers in air-gapped environments.
Preventing Insider Threats in Air-Gapped Datacenters
Air-gapped datacenters physically isolate critical servers from external networks, significantly reducing the risk of insider threats by eliminating remote access vectors. Strict access controls, biometric authentication, and segmented zones further prevent unauthorized personnel from interacting with sensitive systems. Regular audits and monitoring protocols ensure compliance and detect any anomalous activities within these secured environments.
Compliance Requirements for Air-Gap Security
Air-gap security in data centers enforces strict physical and network isolation to comply with regulatory standards such as NIST SP 800-53 and ISO/IEC 27001, ensuring that sensitive data remains uncompromised. This isolation mitigates risks associated with cyber threats by eliminating connections to unsecured networks, fulfilling compliance mandates for protecting classified information and critical infrastructure. Regular audits and documented evidence of air-gap integrity are essential for maintaining certification and meeting legal obligations.
Common Challenges of Maintaining Air-Gapped Datacenters
Maintaining air-gapped datacenters often faces challenges such as ensuring strict physical isolation to prevent unauthorized data leakage and managing secure data transfer methods between isolated networks. The lack of real-time updates and automated monitoring increases the risk of outdated security patches and potential undetected vulnerabilities. Additionally, balancing operational efficiency with stringent security controls requires specialized protocols and trained personnel to maintain the integrity of the air-gap environment.
Future Trends in Air-Gap Security Technologies
Future trends in air-gap security technologies emphasize the integration of advanced machine learning algorithms for anomaly detection and the adoption of quantum encryption methods to enhance data isolation. Innovations in hardware-level security, such as physically unclonable functions (PUFs), are expected to fortify air-gapped environments against sophisticated cyber threats. Enhanced sensor networks designed to detect electromagnetic emissions and unauthorized physical access will also play a critical role in next-generation data center air-gap implementations.
example of air-gap in datacenter Infographic
 samplerz.com
samplerz.com