A salami attack in financial fraud involves stealing small amounts of money repeatedly from multiple transactions, making the theft less noticeable. For instance, a cybercriminal might manipulate a bank's rounding system to divert fractions of cents from numerous customer accounts into a single fraudulent account. Over time, these tiny deductions accumulate into a substantial sum without triggering immediate suspicion. Financial institutions are particularly vulnerable to salami attacks due to the high volume of microtransactions processed daily. Hackers often exploit automated systems or software bugs to execute these small-scale thefts, targeting entities such as online payment platforms, payroll systems, or ATM networks. Detecting such fraud requires advanced anomaly detection techniques and real-time transaction monitoring to identify irregular patterns in micro-amount deductions.
Table of Comparison
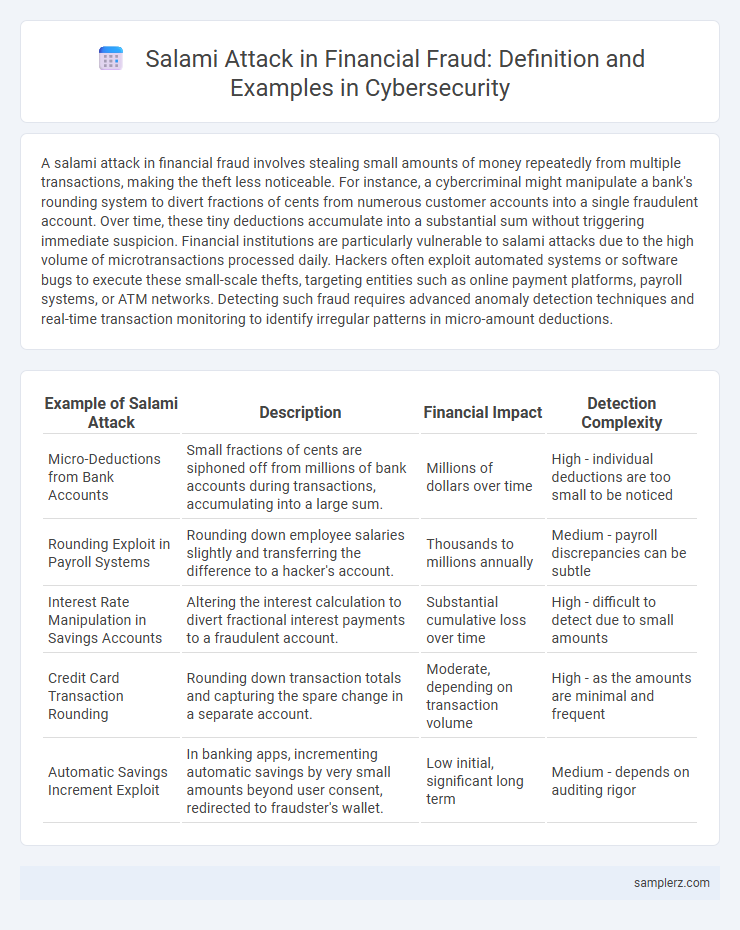
| Example of Salami Attack | Description | Financial Impact | Detection Complexity |
|---|---|---|---|
| Micro-Deductions from Bank Accounts | Small fractions of cents are siphoned off from millions of bank accounts during transactions, accumulating into a large sum. | Millions of dollars over time | High - individual deductions are too small to be noticed |
| Rounding Exploit in Payroll Systems | Rounding down employee salaries slightly and transferring the difference to a hacker's account. | Thousands to millions annually | Medium - payroll discrepancies can be subtle |
| Interest Rate Manipulation in Savings Accounts | Altering the interest calculation to divert fractional interest payments to a fraudulent account. | Substantial cumulative loss over time | High - difficult to detect due to small amounts |
| Credit Card Transaction Rounding | Rounding down transaction totals and capturing the spare change in a separate account. | Moderate, depending on transaction volume | High - as the amounts are minimal and frequent |
| Automatic Savings Increment Exploit | In banking apps, incrementing automatic savings by very small amounts beyond user consent, redirected to fraudster's wallet. | Low initial, significant long term | Medium - depends on auditing rigor |
Understanding the Salami Attack: A Brief Overview
Salami attacks in financial fraud involve extracting tiny, often imperceptible amounts of money from numerous accounts, cumulatively resulting in significant theft. Cybercriminals exploit system vulnerabilities to round down financial transactions or siphon fractions of pennies, avoiding immediate detection by masking these small deductions. This method leverages high-frequency, low-value manipulations within digital financial systems to evade traditional fraud detection mechanisms.
Historical Cases of Salami Attacks in Banking
Historical cases of salami attacks in banking reveal how cybercriminals exploited small, incremental deductions from numerous accounts to accumulate significant amounts without immediate detection. One notable example is the 1990s attack on an unnamed Eastern European bank, where hackers manipulated transaction rounding errors to siphon micro-amounts over months, eventually amassing substantial illicit funds. These attacks leveraged automated scripts to exploit vulnerabilities in batch processing systems, highlighting the need for enhanced fraud detection algorithms in financial institutions.
How Salami Attacks Exploit Transaction Rounding
Salami attacks in financial fraud exploit transaction rounding by extracting minuscule fractions of currency from numerous accounts, often just pennies, which cumulatively amount to significant unauthorized gains. These tiny, often unnoticed deductions occur during the rounding process in electronic transactions or interest calculations, bypassing standard fraud detection systems due to their minimal individual impact. Financial institutions face challenges detecting these exploits as the aggregated theft appears as legitimate rounding errors, necessitating advanced anomaly detection techniques to uncover salami attack patterns.
Digital Banking Vulnerabilities to Salami Attacks
Salami attacks exploit micro-transaction vulnerabilities in digital banking systems, where tiny unauthorized deductions from numerous accounts accumulate into significant fraudulent gains. These attacks often target poorly monitored APIs or automated transaction processes lacking anomaly detection, allowing cybercriminals to remain undetected. Financial institutions must strengthen endpoint security and implement real-time transaction analytics to mitigate risks associated with salami slicing fraud.
Salami Attack Schemes in Online Payment Systems
Salami attack schemes in online payment systems involve cybercriminals siphoning off minute fractions of transactions, which accumulate into significant unauthorized gains over time without raising immediate suspicion. These attacks exploit vulnerabilities in payment gateways and rounding functionalities, enabling attackers to deduct tiny amounts from each transaction processed through digital wallets or credit card systems. Continuous monitoring and anomaly detection algorithms are essential to identify these fractional thefts and protect financial platforms from cumulative losses caused by salami attacks.
Famous Salami Attack Incidents in Financial Firms
Famous salami attack incidents in financial firms include the 1982 Citibank case where hackers exploited rounding errors to siphon off small amounts from thousands of accounts, collectively amassing significant funds. Another notable example occurred in 2010 when an insider at a major European bank manipulated transaction logs to divert microscopic fractions of millions in client assets unnoticed. These attacks demonstrate how minuscule, incremental fraud can bypass traditional security systems and cause substantial financial damage over time.
Step-by-Step Breakdown: Executing a Financial Salami Attack
A financial salami attack begins by infiltrating a banking or payment system to access microtransaction processing. The attacker programs automated scripts to shave minuscule fractions of cents from millions of transactions, accumulating significant amounts without detection. Continuous monitoring and incremental adjustments ensure that the stolen sums remain below thresholds that would trigger fraud alerts or audits.
Detecting Salami Attacks: Key Indicators in Financial Fraud
Unusual patterns of numerous small, unauthorized transactions targeting multiple accounts often signal a salami attack in financial fraud. Monitoring for repetitive, fractional deductions just below authorization thresholds helps detect these subtle schemes early. Advanced analytics leveraging anomaly detection algorithms significantly enhance identification of incremental fund siphoning across financial platforms.
Legal Consequences of Financial Salami Attacks
Financial salami attacks, where attackers systematically skim tiny amounts from numerous transactions, frequently result in severe legal consequences including charges of fraud, embezzlement, and money laundering. Regulatory bodies enforce stringent penalties and sanctions, often leading to lengthy prison sentences and substantial fines for perpetrators. Organizations must implement robust security measures to detect such breaches early and avoid extensive legal liabilities and reputational damage.
Preventative Measures Against Salami Attacks in Finance
Implementing advanced transaction monitoring systems and real-time anomaly detection helps identify suspicious fractional deductions characteristic of salami attacks in financial institutions. Enforcing strict access controls and multi-factor authentication reduces insider threats by limiting unauthorized manipulation of account balances. Regular audits combined with employee training on fraud detection further strengthen defenses against incremental financial fraud schemes.
example of salami attack in financial fraud Infographic
 samplerz.com
samplerz.com