A canary in a data breach is a security mechanism designed to detect unauthorized access early by monitoring specific indicators or decoys. One common example involves setting up decoy files or honeypots that contain fictitious yet plausible data. When an attacker accesses or attempts to exfiltrate this fake information, the system triggers an alert, enabling security teams to respond promptly to the potential breach. Canaries can also take the form of audit log entries or user accounts created solely for monitoring unusual activity. These entities remain untouched during normal operations, so any interaction signals a security incident. Organizations implement canary tokens to capture critical breach data, such as IP addresses or access timestamps, improving incident response capabilities and minimizing damage.
Table of Comparison
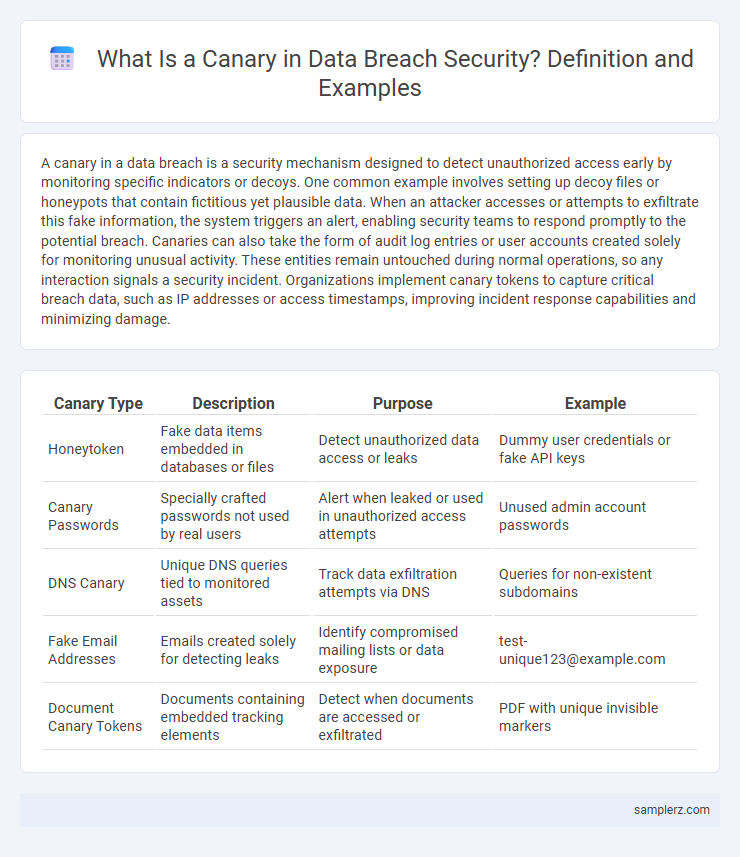
| Canary Type | Description | Purpose | Example |
|---|---|---|---|
| Honeytoken | Fake data items embedded in databases or files | Detect unauthorized data access or leaks | Dummy user credentials or fake API keys |
| Canary Passwords | Specially crafted passwords not used by real users | Alert when leaked or used in unauthorized access attempts | Unused admin account passwords |
| DNS Canary | Unique DNS queries tied to monitored assets | Track data exfiltration attempts via DNS | Queries for non-existent subdomains |
| Fake Email Addresses | Emails created solely for detecting leaks | Identify compromised mailing lists or data exposure | test-unique123@example.com |
| Document Canary Tokens | Documents containing embedded tracking elements | Detect when documents are accessed or exfiltrated | PDF with unique invisible markers |
Understanding Canary Tokens in Data Security
Canary tokens function as digital tripwires embedded within a system to detect unauthorized access or data breaches by triggering alerts when activated. These tokens can take various forms, such as fake files, URLs, or API keys, designed to appear legitimate and lure attackers. Implementing canary tokens enhances early breach detection and minimizes damage by providing real-time notifications of suspicious activity.
The Role of Canary Files in Breach Detection
Canary files serve as strategically placed decoy documents designed to trigger alerts when accessed, signaling potential unauthorized intrusions in a network environment. These files often contain embedded metadata or unique identifiers that, once opened or copied, notify security teams immediately, enabling faster breach detection and response. Implementing canary files enhances the overall cybersecurity posture by providing early warnings that help mitigate data exfiltration and limit damage from attacks.
Real-World Data Breach Incidents Exposed by Canaries
Canaries have exposed significant real-world data breaches by serving as early warning indicators within compromised systems, such as the 2017 Equifax breach where planted honeytokens alerted security teams to unauthorized data access. In the 2020 SolarWinds attack, embedded canary tokens provided critical forensic evidence that helped trace the scope of the intrusion. These examples demonstrate how canaries enhance detection capabilities by identifying breaches before extensive data exfiltration occurs.
Setting Up Effective Canary Traps for Sensitive Data
Deploying effective canary traps for sensitive data involves inserting unique, traceable decoy information that signals unauthorized access or data exfiltration attempts. These canary tokens generate alerts when triggered, allowing security teams to quickly identify and respond to breaches with minimal false positives. Ensuring that canary traps are indistinguishable from genuine data and strategically placed within critical systems enhances early threat detection and protects organizational assets.
Case Study: How a Canary Saved Corporate Data
A major financial services firm deployed canary tokens within its sensitive databases, triggering immediate alerts when unauthorized access occurred. This proactive approach allowed security teams to isolate the breach, preventing exfiltration of critical customer information. The canary's timely detection significantly minimized data loss and strengthened the company's overall cybersecurity posture.
Key Advantages of Using Canaries in Cyber Defense
Canaries in data breach detection provide early warning signals by deploying decoy files, credentials, or systems that alert security teams upon unauthorized access, significantly reducing response times. Their strategic placement across network segments enhances threat visibility, enabling precise identification of intrusion points and malicious actors. Using canaries minimizes false positives compared to traditional detection methods, improving efficiency and accuracy in cyber defense operations.
Limitations and Risks of Relying on Canary Mechanisms
Canary mechanisms in data breach detection often face limitations such as false negatives, where sophisticated attackers bypass canary triggers without detection, and false positives, causing unnecessary alerts that strain security teams. Relying solely on canaries may create a false sense of security, neglecting comprehensive monitoring and layered defense strategies critical for effective breach detection. The risk of delayed response increases when organizations depend exclusively on canaries, as attackers exploiting unknown vulnerabilities might remain undetected until significant damage occurs.
Integrating Canary Alerts into Security Operations
Integrating canary alerts into security operations enhances breach detection by providing real-time indicators of unauthorized access, enabling rapid incident response. These decoy signals generate precise alerts that help security teams isolate compromised systems without triggering widespread alarms. Utilizing automated workflows to correlate canary alert data with existing security information and event management (SIEM) platforms streamlines threat analysis and containment efforts.
Comparing Canary Tokens to Traditional Honeypots
Canary tokens provide lightweight, customizable alerts embedded in files or URLs that trigger notifications when accessed, offering precise breach detection. Traditional honeypots simulate entire systems to attract attackers, which require extensive resources and may be more conspicuous. Canary tokens excel in stealth and deployment flexibility, enabling targeted intrusion detection with minimal infrastructure overhead.
Best Practices for Deploying Canaries Against Data Breaches
Implementing canaries in data breach detection requires strategically embedding decoy data or credentials within the system to lure attackers without disrupting legitimate operations. Best practices include regularly rotating canary credentials, monitoring canary access logs in real-time, and isolating canary systems to prevent attackers from leveraging them beyond detection. Combining canaries with automated alerting and incident response workflows enhances early breach identification and minimizes potential damage.
example of canary in data breach Infographic
 samplerz.com
samplerz.com