Onion routing is a technique used in secure communication to enhance privacy and anonymity. It involves encrypting a message multiple times and sending it through a series of network nodes called relays or onions routers. Each relay decrypts one layer of encryption, revealing the next relay, ensuring that no single node knows both the origin and destination of the data. This method is prominently used in the Tor network, which enables anonymous internet browsing by routing traffic through multiple volunteer-operated servers worldwide. Onion routing protects against surveillance and traffic analysis by obscuring the relationship between sender and receiver. Its layered encryption model ensures that data remains confidential and resistant to eavesdropping at each step of transmission.
Table of Comparison
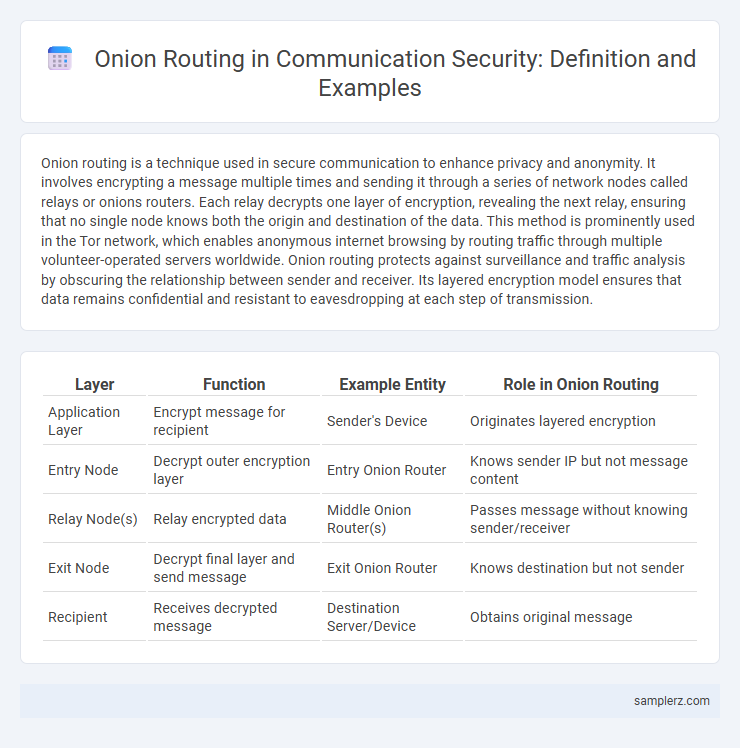
| Layer | Function | Example Entity | Role in Onion Routing |
|---|---|---|---|
| Application Layer | Encrypt message for recipient | Sender's Device | Originates layered encryption |
| Entry Node | Decrypt outer encryption layer | Entry Onion Router | Knows sender IP but not message content |
| Relay Node(s) | Relay encrypted data | Middle Onion Router(s) | Passes message without knowing sender/receiver |
| Exit Node | Decrypt final layer and send message | Exit Onion Router | Knows destination but not sender |
| Recipient | Receives decrypted message | Destination Server/Device | Obtains original message |
Understanding Onion Routing in Secure Communication
Onion routing uses multiple layers of encryption to anonymize data transmission across a distributed network, protecting user identity and communication content from surveillance. Each node in the network decrypts a single encryption layer to reveal the next relay, ensuring that no single point can trace the entire communication path. This method is fundamental in secure communication systems like Tor, enhancing privacy and thwarting traffic analysis attacks.
The Core Principles Behind Onion Routing
Onion routing secures communication by encapsulating messages in multiple layers of encryption, each decrypted by successive nodes to reveal routing instructions without exposing the original source or destination. This technique ensures anonymity through layered encryption, routing through randomly selected nodes, and hiding metadata such as IP addresses and message content. The core principles revolve around confidentiality, anonymity, and resistance to traffic analysis, making onion routing foundational in privacy-focused networks like Tor.
How Onion Routing Protects User Privacy
Onion routing protects user privacy by encrypting data in multiple layers, each decrypted by successive nodes in the network, ensuring no single node can access the full message or identify its origin and destination. This multi-layer encryption effectively conceals user IP addresses and communication content, preventing surveillance and tracking by third parties. The randomized path through several relays further obscures the communication trail, enhancing anonymity and resisting traffic analysis.
Step-by-Step Example of Onion Routing Workflow
Onion routing enhances communication security by encrypting messages in multiple layers, each peeled away by intermediate nodes to reveal routing instructions without compromising data integrity. In a typical onion routing workflow, the sender first encrypts the message with the receiver's key, then sequentially wraps it in several encryption layers corresponding to each relay node in the path. Each relay node decrypts its layer to uncover the next hop, ensuring anonymity by preventing any single node from accessing both sender identity and message content.
Role of Encryption Layers in Onion Routing
Onion routing employs multiple layers of encryption to ensure data confidentiality and anonymity during transmission, where each relay decrypts only one layer to reveal the next destination, preventing any single node from accessing the complete message or sender identity. This layered encryption methodology secures communication paths by segregating routing information and payload data across different nodes. The dynamic and decentralized structure of onion routing significantly mitigates risks such as traffic analysis and eavesdropping in secure communication networks.
Real-World Onion Routing Use Cases
Onion routing is prominently utilized in the Tor network, enabling anonymous web browsing by encrypting and routing traffic through multiple volunteer-operated nodes, thereby concealing user identities and locations. It is also implemented in secure messaging applications like Signal, which employs layered encryption techniques to ensure message confidentiality and resist traffic analysis. Additionally, government agencies use onion routing to protect sensitive communications and maintain operational security in intelligence and law enforcement activities.
Onion Routing vs. Traditional Routing Methods
Onion routing encrypts data in multiple layers, ensuring anonymity by routing messages through a series of volunteer-operated nodes that peel away one encryption layer at each hop. Traditional routing methods transmit data packets with minimal encryption and direct path visibility, making them vulnerable to interception and traffic analysis. The layered encryption of onion routing significantly enhances privacy and security compared to the straightforward, less protected nature of conventional routing protocols.
Potential Vulnerabilities in Onion Routing
Onion routing, used in secure communication networks like Tor, encrypts data in multiple layers to anonymize user identity and traffic. Potential vulnerabilities include timing attacks, where adversaries analyze packet timing to de-anonymize users, and malicious exit nodes that can intercept or alter unencrypted data upon leaving the network. Network congestion and route selection biases also expose risks of correlation attacks, undermining the intended privacy protections of onion routing protocols.
The Impact of Onion Routing on Anonymity Networks
Onion routing significantly enhances anonymity networks by encrypting data in multiple layers, each peeled away by successive nodes to obscure the origin and destination of communication. This multi-layer encryption prevents any single intermediary from accessing full user information, thereby reducing the risk of traffic analysis and surveillance. As a result, onion routing bolsters privacy and security in anonymous communication systems, facilitating safer digital interactions.
Future Developments in Onion Routing Technology
Future developments in onion routing technology are expected to enhance anonymous communication through integration with quantum-resistant encryption algorithms, improving resistance to emerging cyber threats. Advances in decentralized network protocols aim to reduce latency and increase scalability, facilitating near real-time secure messaging across global nodes. Research into machine learning-driven traffic analysis detection promises to further obscure user activity, safeguarding privacy against increasingly sophisticated surveillance techniques.
example of onion routing in communication Infographic
 samplerz.com
samplerz.com