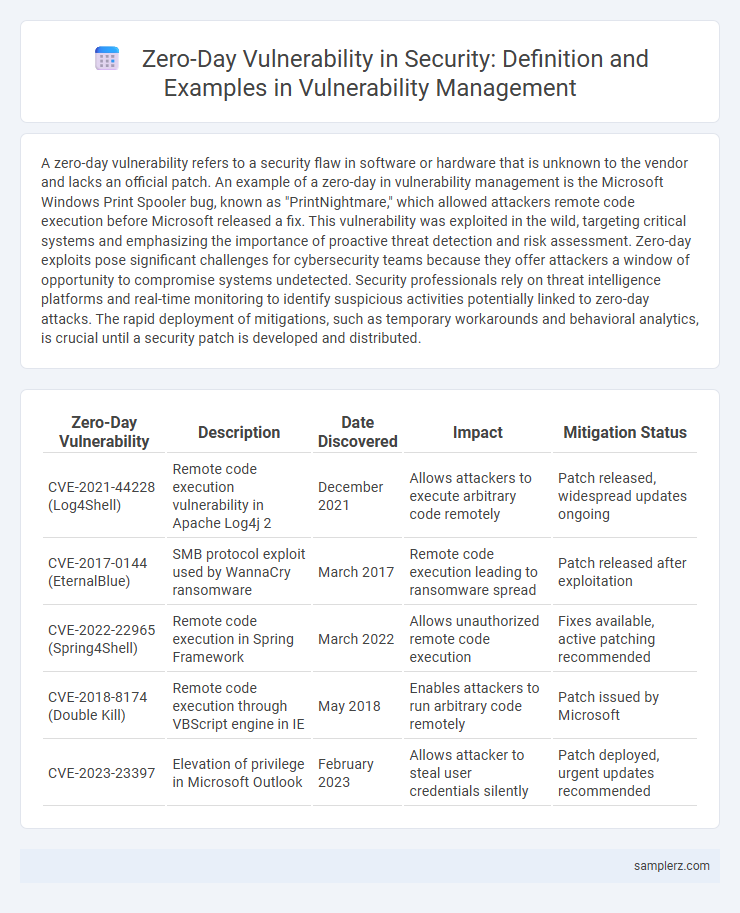
A zero-day vulnerability refers to a security flaw in software or hardware that is unknown to the vendor and lacks an official patch. An example of a zero-day in vulnerability management is the Microsoft Windows Print Spooler bug, known as "PrintNightmare," which allowed attackers remote code execution before Microsoft released a fix. This vulnerability was exploited in the wild, targeting critical systems and emphasizing the importance of proactive threat detection and risk assessment. Zero-day exploits pose significant challenges for cybersecurity teams because they offer attackers a window of opportunity to compromise systems undetected. Security professionals rely on threat intelligence platforms and real-time monitoring to identify suspicious activities potentially linked to zero-day attacks. The rapid deployment of mitigations, such as temporary workarounds and behavioral analytics, is crucial until a security patch is developed and distributed.
Table of Comparison
| Zero-Day Vulnerability | Description | Affected Software | Discovery Date | Impact |
|---|---|---|---|---|
| Stuxnet (CVE-2010-2568) | A highly sophisticated worm exploiting zero-day vulnerabilities to target Iranian nuclear facilities. | Microsoft Windows | 2010 | Critical, targeted sabotage and espionage |
| Microsoft Exchange Server Zero-Day (CVE-2021-26855) | Remote code execution vulnerability exploited by Hafnium threat group to access email servers. | Microsoft Exchange Server | 2021 | Severe, data breach and espionage |
| SolarWinds SUNBURST (CVE-2020-10148) | Supply chain attack inserting malicious code into SolarWinds Orion software updates. | SolarWinds Orion Platform | 2020 | High, widespread network compromise |
| Pegasus Spyware Exploit | Series of zero-day exploits used to deploy surveillance software on mobile devices. | iOS and Android | 2016-2021 | Critical, targeted surveillance and data theft |
| PrintNightmare (CVE-2021-34527) | Remote code execution in Windows Print Spooler service allowing privilege escalation. | Microsoft Windows | 2021 | Severe, remote code execution and privilege escalation |
Understanding Zero Day Vulnerabilities in Security
Zero day vulnerabilities represent unknown security flaws that attackers exploit before developers can issue patches, making them critical threats in vulnerability management. Exploits such as the Stuxnet worm demonstrated how zero day vulnerabilities can target industrial control systems with devastating precision. Effective security requires continuous monitoring, advanced threat intelligence, and rapid incident response to mitigate the risks posed by these undetectable exploits.
The Lifecycle of a Zero Day Exploit
Zero-day exploits target unknown vulnerabilities before developers can issue patches, making them critical in vulnerability management. The lifecycle begins with discovery, followed by weaponization, delivery, exploitation, and finally, detection and mitigation. Effective security strategies rely on rapid identification and patch deployment to minimize the window of exposure during this lifecycle.
Real-World Examples of Zero Day Attacks
The Stuxnet worm, discovered in 2010, exploited multiple zero-day vulnerabilities to target Iran's nuclear facilities, representing one of the most sophisticated real-world zero-day attacks. Another example is the 2021 Microsoft Exchange Server breach, where threat actors leveraged four zero-day vulnerabilities to access thousands of organizations' email systems globally. These incidents underscore the critical importance of proactive vulnerability management and rapid security patch deployment in mitigating zero-day threats.
The Role of Vulnerability Management in Zero Day Defense
Effective vulnerability management plays a crucial role in zero day defense by continuously identifying and assessing unknown security flaws before they can be exploited. Implementing real-time threat intelligence and automated patch management enhances the ability to detect and remediate zero day vulnerabilities quickly. Prioritizing asset risk and exposure ensures critical systems receive immediate protection against emerging zero day threats.
Indicators of a Potential Zero Day Vulnerability
Indicators of a potential zero-day vulnerability include unusual network traffic patterns, unexpected application behavior, and anomalies in system logs that deviate from established baselines. Monitoring for abnormal code execution or exploitation attempts in memory can reveal zero-day activities before patches become available. Leveraging threat intelligence feeds and behavioral analytics enhances detection by correlating emerging attack techniques linked to unknown vulnerabilities.
How Attackers Discover and Exploit Zero Days
Attackers discover zero-day vulnerabilities through extensive reconnaissance, fuzz testing, and reverse engineering of software code. These exploits remain undetected until actively used, allowing cybercriminals to bypass existing security defenses and execute unauthorized access or data theft. Effective zero-day vulnerability management requires continuous threat intelligence and proactive patch deployment to minimize exploitation risks.
Tools for Detecting Zero Day Vulnerabilities
Advanced tools like machine learning-based anomaly detection systems and behavior analysis platforms play a crucial role in identifying zero day vulnerabilities by recognizing unusual patterns indicative of unknown threats. Sandboxing tools execute suspicious code in isolated environments to observe malicious behavior without risking system integrity. Threat intelligence platforms aggregate global vulnerability data and real-time exploits, enhancing early detection and response to zero day attacks in enterprise security frameworks.
Mitigation Strategies for Zero Day Threats
Mitigation strategies for zero-day threats include implementing advanced endpoint detection and response (EDR) systems that monitor unusual behavior to identify potential exploits before patches are available. Employing network segmentation limits the lateral movement of attackers exploiting zero-day vulnerabilities, reducing overall risk exposure. Regular threat intelligence updates and proactive application of virtual patching through web application firewalls (WAF) help shield critical assets from unknown threats during the vulnerability window.
Zero Day Case Studies in Vulnerability Management
The 2017 WannaCry ransomware attack exploited a zero-day vulnerability in Microsoft's SMB protocol, causing widespread disruption across industries by encrypting data and demanding ransom payments. Another notable zero-day incident was the 2020 SolarWinds supply chain attack, which leveraged a backdoor vulnerability to infiltrate numerous government and enterprise networks undetected. These case studies highlight the critical importance of rapid detection and patching in zero-day vulnerability management to prevent severe security breaches.
Future Trends in Zero Day Vulnerability Management
Emerging trends in zero-day vulnerability management emphasize the integration of artificial intelligence and machine learning to predict and identify unknown exploits before they can be weaponized. Advanced threat intelligence platforms are leveraging behavioral analytics and real-time data sharing to enhance detection capabilities and reduce response times. Organizations are increasingly adopting proactive strategies such as automated patch deployment and zero-trust architectures to mitigate risks associated with zero-day vulnerabilities.
example of zero day in vulnerability management Infographic
 samplerz.com
samplerz.com