The cyberattack kill chain outlines the sequential stages adversaries follow to breach and exploit a target network. It begins with reconnaissance, where attackers gather intelligence on the target's systems and employees, followed by weaponization, involving the creation of malware tailored to exploit identified vulnerabilities. The delivery phase moves this malicious payload to the victim through methods like phishing emails or infected USB drives. Exploitation occurs when the malware executes and exploits security weaknesses, granting initial access to the attacker. Installation establishes persistent access through backdoors or implants, allowing continued control over compromised systems. Command and control enables attackers to remotely manipulate systems while actions on objectives involve data theft, encryption, or system disruption, completing the kill chain's operational cycle.
Table of Comparison
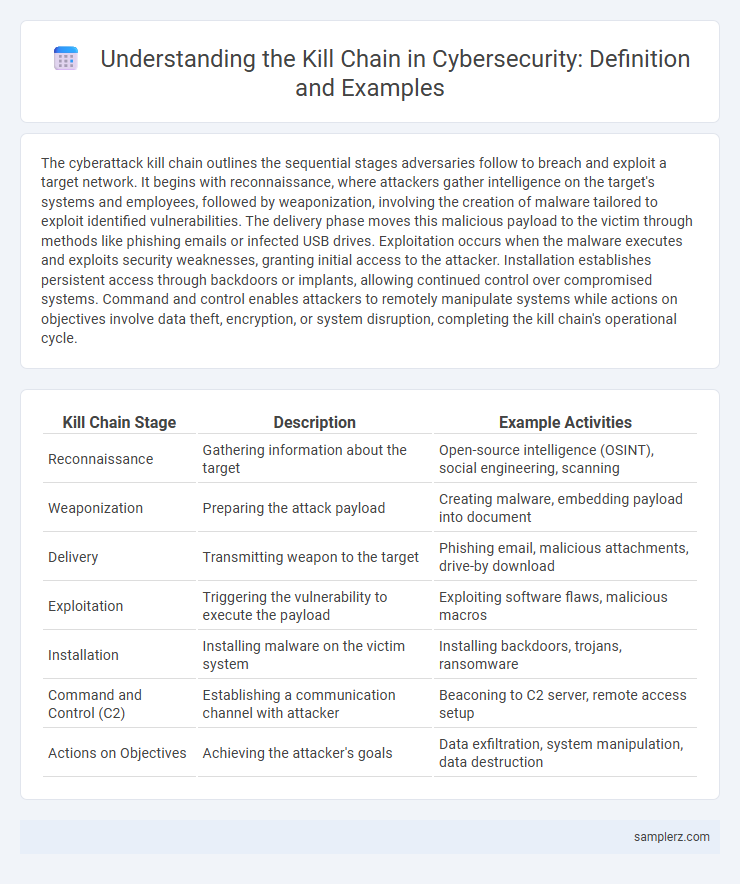
| Kill Chain Stage | Description | Example Activities |
|---|---|---|
| Reconnaissance | Gathering information about the target | Open-source intelligence (OSINT), social engineering, scanning |
| Weaponization | Preparing the attack payload | Creating malware, embedding payload into document |
| Delivery | Transmitting weapon to the target | Phishing email, malicious attachments, drive-by download |
| Exploitation | Triggering the vulnerability to execute the payload | Exploiting software flaws, malicious macros |
| Installation | Installing malware on the victim system | Installing backdoors, trojans, ransomware |
| Command and Control (C2) | Establishing a communication channel with attacker | Beaconing to C2 server, remote access setup |
| Actions on Objectives | Achieving the attacker's goals | Data exfiltration, system manipulation, data destruction |
Understanding the Cyber Kill Chain Framework
The Cyber Kill Chain framework outlines the stages of a cyberattack, including reconnaissance, weaponization, delivery, exploitation, installation, command and control, and actions on objectives. Understanding each phase helps security professionals identify attack patterns and implement targeted defenses to disrupt adversaries before data breaches occur. This model is essential for developing proactive cybersecurity strategies and enhancing incident response capabilities.
Stages of the Cyber Kill Chain Explained
The Cyber Kill Chain outlines distinct stages of a cyberattack: reconnaissance, weaponization, delivery, exploitation, installation, command and control, and actions on objectives. Each phase represents a critical step where attackers gather intelligence, deploy malicious payloads, establish control, and execute their objectives, allowing defenders to identify and disrupt the attack sequence effectively. Understanding these stages enables organizations to implement targeted security measures, reducing the likelihood of successful breaches.
Real-World Examples of Kill Chain in Cyberattacks
The 2017 WannaCry ransomware attack exemplifies a cyber kill chain by exploiting the EternalBlue vulnerability to gain initial access, followed by lateral movement using SMB protocol vulnerabilities to spread rapidly across networks. The 2020 SolarWinds breach demonstrated a sophisticated kill chain involving supply chain compromise, where attackers inserted malicious code into software updates, enabling persistent access and data exfiltration. Both incidents highlight critical stages of reconnaissance, exploitation, command-and-control, and data theft within real-world cyber kill chains.
Reconnaissance: The Attackers’ First Step
Reconnaissance is the initial phase in the cyberattack kill chain where attackers gather critical information about the target's network, systems, and security defenses. Techniques like network scanning, social engineering, and open-source intelligence (OSINT) enable adversaries to identify vulnerabilities and entry points. Comprehensive reconnaissance increases the likelihood of a successful breach by allowing attackers to tailor subsequent stages of the attack with precision.
Weaponization and Delivery Methods
In the cyberattack kill chain, weaponization involves creating a malicious payload, such as a custom malware or exploit, specifically designed to target system vulnerabilities. Delivery methods typically include phishing emails with embedded links, spear-phishing attachments, infected USB drives, or compromised websites that launch drive-by downloads. These steps enable attackers to infiltrate target environments by leveraging social engineering tactics and software exploits to bypass security defenses.
Exploitation: Gaining Initial Access
Exploitation in the cyberattack kill chain involves leveraging software vulnerabilities or human errors to gain initial access to a targeted system. Attackers commonly use phishing emails, zero-day exploits, or malicious payloads embedded in web traffic to bypass security defenses. This phase is crucial as it establishes a foothold that enables further lateral movement and data exfiltration within the compromised network.
Installation: Establishing Persistence
Installation represents the critical phase in the cyber kill chain where attackers establish persistence by deploying malware, such as backdoors or rootkits, onto the compromised system. This step ensures continued access for threat actors despite system reboots or security measures, often leveraging techniques like registry modifications, scheduled tasks, or malicious services. Effective detection and mitigation during the installation phase are essential to prevent long-term unauthorized control and data exfiltration.
Command and Control Channels in Attacks
Command and Control (C2) channels play a crucial role in the cyberattack kill chain by enabling attackers to maintain communication with compromised systems. These channels often utilize encrypted protocols, such as HTTPS or custom TCP-based protocols, to evade detection and facilitate data exfiltration or remote control. Detecting anomalies in C2 traffic patterns and implementing network segmentation are critical measures for interrupting the attacker's control within the kill chain.
Actions on Objectives: Data Theft and Damage
During the Actions on Objectives phase in a cyberattack kill chain, threat actors prioritize data theft and system damage to achieve their strategic goals. Attackers often exfiltrate sensitive information such as intellectual property, financial records, or personal data while deploying malware to corrupt files or disrupt system operations. Effective detection and response mechanisms are critical to prevent irreversible damage and protect organizational assets from exploitation.
Defensive Strategies to Break the Kill Chain
Breaking the cyberattack kill chain involves disrupting key stages such as reconnaissance, weaponization, delivery, exploitation, installation, command and control, and actions on objectives. Implementing defensive strategies like network segmentation, multi-factor authentication, endpoint detection and response (EDR), and real-time threat intelligence sharing effectively prevents attackers from progressing through the kill chain. Proactive monitoring and rapid incident response further enhance the ability to neutralize threats before they cause significant damage.
example of kill chain in cyberattack Infographic
 samplerz.com
samplerz.com