A common example of a phishing kit used in social engineering is the "EvilKit" phishing kit, which enables attackers to create convincing fake login pages resembling legitimate websites. This kit provides pre-designed templates for popular platforms like Facebook, PayPal, and Gmail, capturing user credentials once victims input their information. Data collected by these kits is often sent directly to the attacker, facilitating unauthorized access to sensitive accounts. Phishing kits like EvilKit leverage social engineering by exploiting user trust in established brands and dynamically generating realistic-looking websites. The kit includes scripts that log keystrokes and capture form submissions, allowing threat actors to gather email addresses, passwords, and sometimes even credit card details. Continuous updates and user-friendly interfaces make such phishing kits efficient tools for cybercriminals targeting personal and organizational security data.
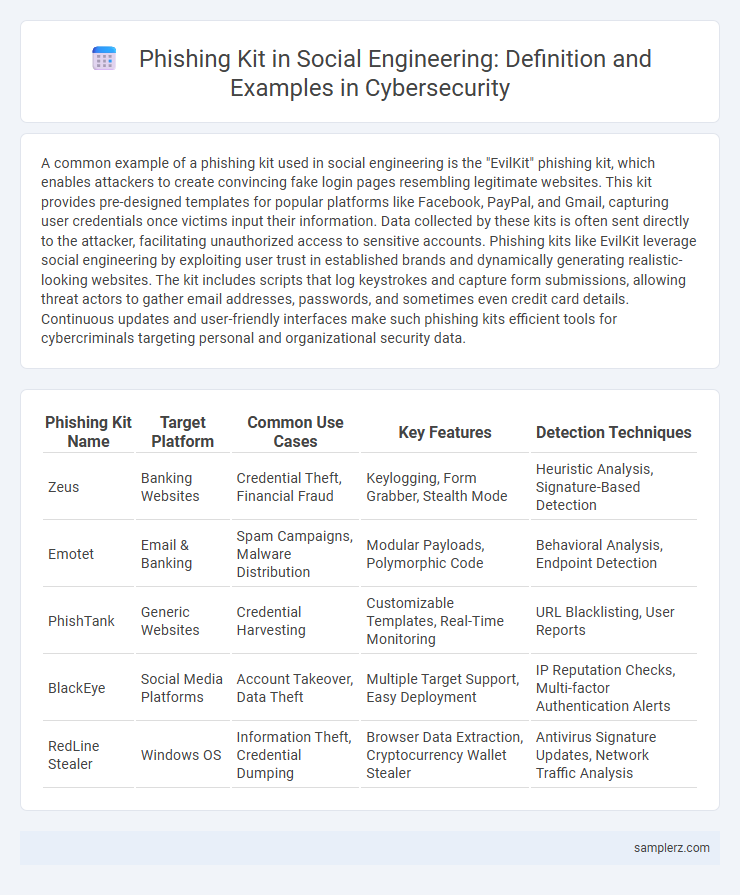
Table of Comparison
| Phishing Kit Name | Target Platform | Common Use Cases | Key Features | Detection Techniques |
|---|---|---|---|---|
| Zeus | Banking Websites | Credential Theft, Financial Fraud | Keylogging, Form Grabber, Stealth Mode | Heuristic Analysis, Signature-Based Detection |
| Emotet | Email & Banking | Spam Campaigns, Malware Distribution | Modular Payloads, Polymorphic Code | Behavioral Analysis, Endpoint Detection |
| PhishTank | Generic Websites | Credential Harvesting | Customizable Templates, Real-Time Monitoring | URL Blacklisting, User Reports |
| BlackEye | Social Media Platforms | Account Takeover, Data Theft | Multiple Target Support, Easy Deployment | IP Reputation Checks, Multi-factor Authentication Alerts |
| RedLine Stealer | Windows OS | Information Theft, Credential Dumping | Browser Data Extraction, Cryptocurrency Wallet Stealer | Antivirus Signature Updates, Network Traffic Analysis |
Introduction to Phishing Kits in Social Engineering
Phishing kits are pre-packaged tools used by cybercriminals to create convincing fake websites that steal sensitive information such as login credentials or financial data. These kits often include templates, scripts, and backend infrastructure to streamline attacks, enabling attackers of varying skill levels to deploy sophisticated social engineering campaigns. Understanding the components and operation of phishing kits is crucial for recognizing and mitigating phishing threats in cybersecurity.
How Phishing Kits Facilitate Cyber Attacks
Phishing kits streamline cyber attacks by providing ready-made templates and malicious infrastructure that enable attackers to mimic legitimate websites effortlessly. These kits automate the deployment of fake login pages, capture user credentials in real-time, and often include back-end scripts for harvesting sensitive data. By lowering technical barriers, phishing kits exponentially increase the scale and speed of social engineering attacks targeting individuals and organizations.
Common Features Found in Phishing Kits
Phishing kits commonly include ready-made templates, spoofed login pages, and automated data collection scripts designed to capture sensitive information like usernames and passwords. They often feature obfuscated code and incorporate email or website cloning techniques to enhance deception and evade detection by security systems. These kits may also provide backend access dashboards for attackers to manage captured credentials and monitor victim activity in real time.
Example 1: Email Credential Harvesting Kits
Email Credential Harvesting Kits are common phishing tools designed to collect usernames and passwords by mimicking legitimate login pages. These kits often include ready-made templates that replicate popular email providers, enabling attackers to capture sensitive information effortlessly. Cybersecurity measures such as multi-factor authentication and email filtering are essential to mitigate the risks posed by these phishing kits.
Example 2: SMS Phishing (Smishing) Kits
SMS phishing (smishing) kits enable attackers to craft convincing fraudulent text messages that deceive recipients into revealing personal information or clicking malicious links. These kits often include customizable templates, spoofed sender IDs, and tracking tools to monitor victim interactions, making it easier to launch targeted social engineering campaigns via mobile devices. The widespread use of smartphones and the immediacy of SMS communication increase the effectiveness of smishing attacks in compromising sensitive security data.
Example 3: Clone Website Phishing Kits
Example 3: Clone Website Phishing Kits replicate legitimate websites with high accuracy, harvesting user credentials through deceptive login pages. These kits often include pre-built templates mimicking banking, e-commerce, or social media platforms, enabling attackers to target a wide user base effectively. Deploying such kits increases the success rate of phishing attacks by exploiting brand trust and user familiarity.
Example 4: Brand Imitation Phishing Kits
Brand Imitation Phishing Kits exploit trusted company logos and website designs to deceive victims into revealing sensitive information such as login credentials and financial data. These kits often include fake login pages that mimic popular brands like Microsoft, PayPal, or Amazon, increasing the likelihood of successful credential theft. Cybersecurity solutions should prioritize detecting these kits by analyzing suspicious domain registrations and monitoring for copied brand assets used in phishing campaigns.
Detection Methods for Identifying Phishing Kits
Phishing kits often bundle malicious code and ready-made templates that mimic legitimate websites to steal user credentials, making web traffic analysis and URL reputation services essential for detection. Behavioral analytics can identify anomalies in user interaction patterns and unexpected form submissions indicative of phishing activity. Machine learning algorithms trained on large datasets of phishing URLs enhance real-time identification by recognizing subtle variations in website structure and content common to phishing kits.
Real-World Phishing Kit Case Studies
The Emotet phishing kit exemplifies real-world social engineering attacks by distributing sophisticated email templates that mimic legitimate organizations to steal credentials. This kit uses dynamic URL generation and obfuscation techniques to evade detection by security filters. Analysis of Emotet campaigns reveals the growing complexity of phishing tools targeting corporate environments and personal user data.
Preventive Measures Against Phishing Kit Attacks
Phishing kits, such as the popular WonderPack, facilitate social engineering attacks by streamlining the creation of fake login pages to harvest credentials. Preventive measures include deploying advanced email filtering systems that detect and block phishing attempts, implementing multi-factor authentication (MFA) to reduce the risk of account compromise, and conducting regular security awareness training to educate users on identifying suspicious emails and links. Continuous monitoring of network traffic and timely patching of software vulnerabilities also play crucial roles in mitigating the impact of phishing kit attacks.
example of phishing kit in social engineering Infographic
 samplerz.com
samplerz.com