The kill chain in adversary emulation consists of several critical phases that simulate the tactics used by cyber attackers. Initial reconnaissance involves gathering information about the target's network and systems to identify vulnerabilities. During weaponization, attackers create malware or exploit tools tailored to the target environment. Exploitation follows when the attacker uses the crafted tools to gain unauthorized access. Establishing a foothold allows the adversary to maintain persistence within the network. Finally, actions on objectives include data exfiltration, system disruption, or further lateral movement to expand control and achieve the attack's goals.
Table of Comparison
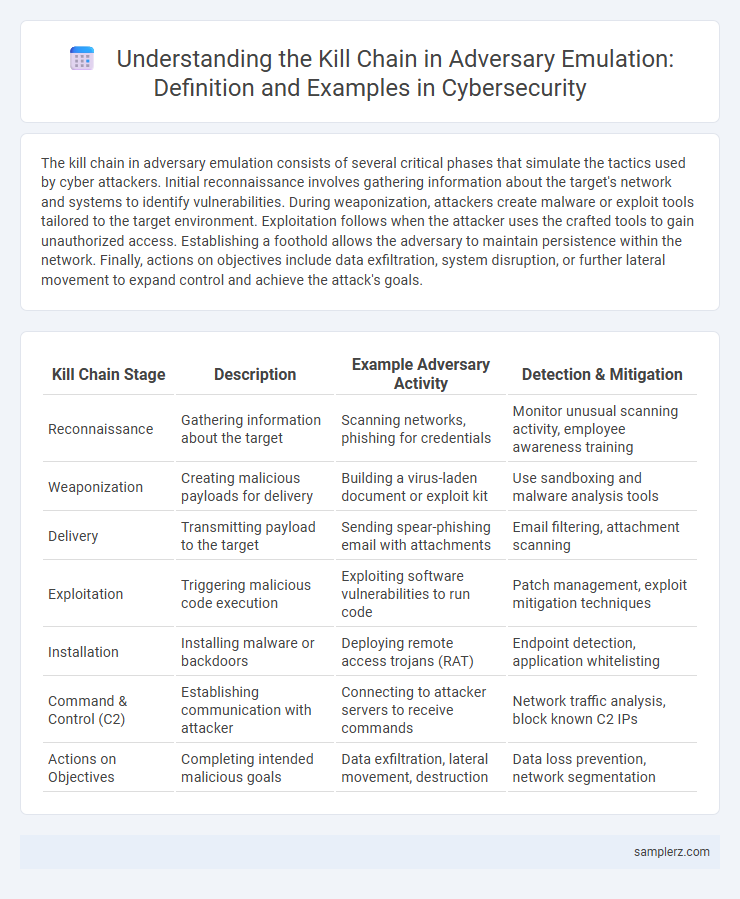
| Kill Chain Stage | Description | Example Adversary Activity | Detection & Mitigation |
|---|---|---|---|
| Reconnaissance | Gathering information about the target | Scanning networks, phishing for credentials | Monitor unusual scanning activity, employee awareness training |
| Weaponization | Creating malicious payloads for delivery | Building a virus-laden document or exploit kit | Use sandboxing and malware analysis tools |
| Delivery | Transmitting payload to the target | Sending spear-phishing email with attachments | Email filtering, attachment scanning |
| Exploitation | Triggering malicious code execution | Exploiting software vulnerabilities to run code | Patch management, exploit mitigation techniques |
| Installation | Installing malware or backdoors | Deploying remote access trojans (RAT) | Endpoint detection, application whitelisting |
| Command & Control (C2) | Establishing communication with attacker | Connecting to attacker servers to receive commands | Network traffic analysis, block known C2 IPs |
| Actions on Objectives | Completing intended malicious goals | Data exfiltration, lateral movement, destruction | Data loss prevention, network segmentation |
Introduction to the Kill Chain in Adversary Emulation
The Kill Chain in adversary emulation outlines the sequential stages attackers use to infiltrate and compromise targets, including reconnaissance, weaponization, delivery, exploitation, installation, command and control, and actions on objectives. Emulating these steps enables security teams to identify vulnerabilities and test defenses under realistic attack scenarios. Understanding this model is crucial for developing proactive threat detection and response strategies in cybersecurity operations.
Understanding Adversary Emulation and Its Importance
Adversary emulation replicates real-world attack techniques to identify vulnerabilities in security defenses. The kill chain model breaks down these attacks into phases such as reconnaissance, weaponization, delivery, exploitation, installation, command and control, and actions on objectives, enabling targeted testing of each stage. Understanding this process helps organizations strengthen their security posture by anticipating attacker behavior and improving detection and response capabilities.
Overview of the Cyber Kill Chain Framework
The Cyber Kill Chain framework outlines key stages of a cyber attack, including reconnaissance, weaponization, delivery, exploitation, installation, command and control, and actions on objectives. Each phase helps security teams simulate adversary tactics for comprehensive threat analysis and enhanced defense strategies. Understanding this structured methodology enables organizations to preemptively identify vulnerabilities and disrupt attack progression effectively.
Reconnaissance: Gathering Intelligence
Reconnaissance in adversary emulation involves systematically collecting intelligence on the target's network infrastructure, employee profiles, and security measures using tools like WHOIS, Nmap, and social engineering techniques. Effective reconnaissance identifies vulnerabilities in firewalls, software versions, and employee awareness that adversaries can exploit. This intelligence gathering phase is critical for simulating realistic attack scenarios and strengthening defensive postures against advanced persistent threats.
Weaponization: Crafting Malicious Payloads
Weaponization in adversary emulation involves creating customized malicious payloads tailored to exploit specific vulnerabilities within a target environment. This stage includes developing malware, such as trojans or ransomware, embedded with malicious code designed to bypass security controls and execute unauthorized actions. Effective weaponization leverages threat intelligence and coding techniques to maximize payload stealth and impact during simulated attacks.
Delivery: Transmitting the Exploit
Delivery in adversary emulation involves transmitting the exploit through vectors such as phishing emails, malicious attachments, or compromised websites to target endpoints. Techniques like spear-phishing with embedded payloads or drive-by downloads deliver the exploit efficiently while evading detection. This phase sets the stage for exploitation by ensuring the malicious code reaches and executes on the intended system.
Exploitation: Initiating the Attack
Exploitation marks the critical phase where adversaries leverage software vulnerabilities, such as unpatched web applications or weak authentication protocols, to gain unauthorized access during the kill chain. Techniques like buffer overflow, SQL injection, and zero-day exploits allow attackers to execute malicious code, establishing a foothold within the target environment. Effective adversary emulation replicates this stage by simulating these exploitation methods to evaluate and strengthen an organization's security posture.
Installation: Establishing Foothold
During the Installation phase in adversary emulation, attackers deploy malware or backdoors to establish persistent access on the compromised system, enabling ongoing control and data exfiltration. Common techniques include using PowerShell scripts, scheduled tasks, or implanting remote access Trojans (RATs) to evade detection and maintain stealth. This stage is critical for securing a foothold that supports lateral movement and further exploitation within the network environment.
Command and Control: Achieving Communication
Command and Control (C2) in adversary emulation exemplifies the kill chain phase where attackers establish persistent communication channels with compromised systems, facilitating remote control and data exfiltration. Techniques include beaconing through HTTP/HTTPS, DNS tunneling, or custom protocols to evade detection by blending with normal network traffic. Effective emulation of C2 communication enables security teams to test detection, response capabilities, and the robustness of network defenses against real-world threats.
Actions on Objectives: Executing the Adversary’s Goals
Actions on Objectives represent the final phase in the cyber kill chain where adversaries execute their intended goals, such as data exfiltration, system disruption, or establishing persistent access. Techniques like credential dumping, privilege escalation, and lateral movement enable attackers to achieve control over critical assets and extract valuable information. Effective adversary emulation models this phase by replicating real-world attacker behaviors to evaluate and strengthen organizational defenses against targeted threats.
example of kill chain in adversary emulation Infographic
 samplerz.com
samplerz.com