Rubber-hose cryptanalysis refers to extracting cryptographic secrets through coercion or physical force rather than technical attacks. An example of this technique occurs when an attacker forcibly interrogates a key holder to reveal encryption keys or passphrases. This method bypasses mathematical or algorithmic cryptanalysis by exploiting human vulnerability as the weak link in security. In practical security scenarios, rubber-hose attacks can target employees, executives, or system administrators with access to sensitive cryptographic material. Such attacks highlight the importance of protecting physical access and implementing multi-factor authentication to mitigate risks. Understanding this threat is crucial for developing comprehensive security policies that include both technical defenses and human factors.
Table of Comparison
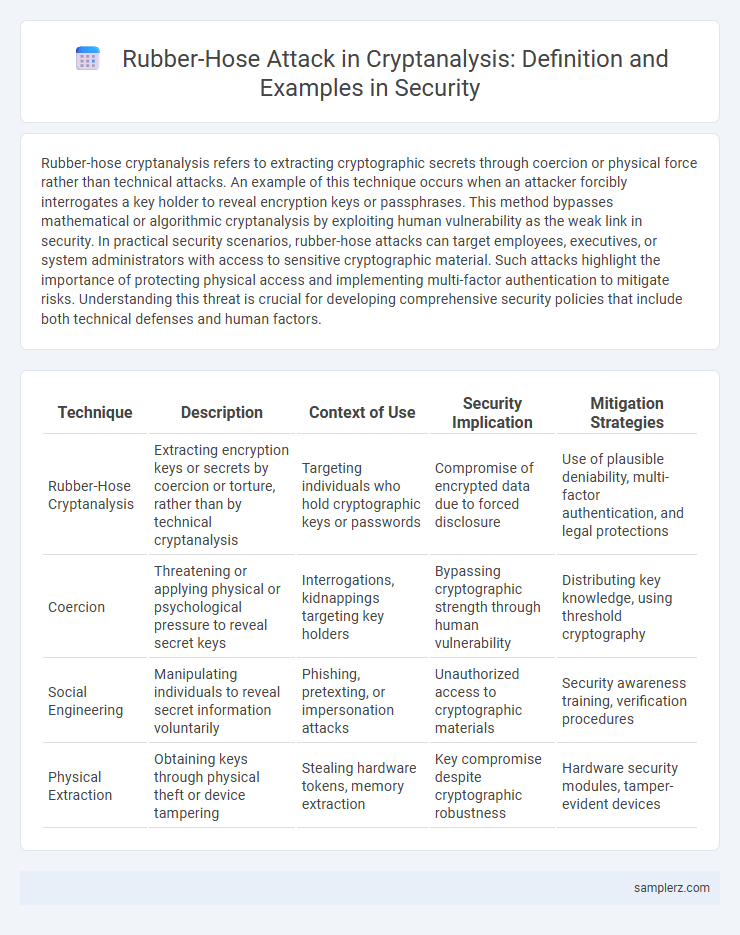
| Technique | Description | Context of Use | Security Implication | Mitigation Strategies |
|---|---|---|---|---|
| Rubber-Hose Cryptanalysis | Extracting encryption keys or secrets by coercion or torture, rather than by technical cryptanalysis | Targeting individuals who hold cryptographic keys or passwords | Compromise of encrypted data due to forced disclosure | Use of plausible deniability, multi-factor authentication, and legal protections |
| Coercion | Threatening or applying physical or psychological pressure to reveal secret keys | Interrogations, kidnappings targeting key holders | Bypassing cryptographic strength through human vulnerability | Distributing key knowledge, using threshold cryptography |
| Social Engineering | Manipulating individuals to reveal secret information voluntarily | Phishing, pretexting, or impersonation attacks | Unauthorized access to cryptographic materials | Security awareness training, verification procedures |
| Physical Extraction | Obtaining keys through physical theft or device tampering | Stealing hardware tokens, memory extraction | Key compromise despite cryptographic robustness | Hardware security modules, tamper-evident devices |
Understanding Rubber-Hose Attacks in Cryptanalysis
Rubber-hose attacks in cryptanalysis involve coercive methods such as physical intimidation or torture to extract cryptographic keys or sensitive information directly from individuals, bypassing traditional algorithmic defenses. This form of attack targets the human element of security, exploiting vulnerabilities in key management and personal security practices rather than weaknesses in cryptographic algorithms. Understanding rubber-hose attacks underscores the critical importance of secure key storage, robust access controls, and minimizing reliance on human memory for cryptographic keys to mitigate social engineering and coercion risks.
Real-World Examples of Rubber-Hose Cryptanalysis
Rubber-hose cryptanalysis involves extracting cryptographic keys or sensitive information through coercion or torture rather than technical attacks. Real-world examples include law enforcement or authoritarian regimes forcing individuals to reveal encryption passwords under duress, such as the FBI's attempts to access encrypted iPhones by compelling suspects or their associates. This method bypasses cryptographic strength by targeting human vulnerabilities, highlighting the critical importance of plausible deniability and secure key management in security protocols.
How Physical Coercion Threatens Cryptographic Security
Physical coercion, such as rubber-hose cryptanalysis, directly threatens cryptographic security by bypassing mathematical defenses and forcing individuals to reveal sensitive cryptographic keys through intimidation or violence. This attack exploits human vulnerabilities rather than algorithmic weaknesses, making even the strongest encryption susceptible when the key holders are physically compromised. Effective security protocols must incorporate safeguards against coercion, emphasizing secure key management and resistance to physical threats.
Notable Cases of Rubber-Hose Attack Techniques
Notable cases of rubber-hose attacks include instances where adversaries have extracted cryptographic keys through physical coercion or torture, bypassing complex encryption algorithms altogether. One prominent example is the 1990s case involving the Russian hacker group "DarkSide," where law enforcement reportedly used force to compel password disclosure. These techniques highlight vulnerabilities in key management, emphasizing the need for secure key storage and tamper-resistant hardware in cryptographic systems.
Comparing Rubber-Hose Attacks to Technical Cryptanalysis
Rubber-hose attacks exploit human vulnerabilities by coercing individuals to disclose cryptographic keys through force or intimidation, differing fundamentally from technical cryptanalysis that relies on mathematical algorithms and computational power. While cryptanalysis targets weaknesses in encryption algorithms, rubber-hose attacks bypass technical defenses by compromising the key holder directly, making them a critical concern in information security. Understanding the human-factor risk highlights the importance of combining strong cryptographic techniques with comprehensive security policies to mitigate coercion threats.
Psychological Tactics in Rubber-Hose Cryptanalysis
Rubber-hose cryptanalysis leverages intense psychological tactics such as coercion, intimidation, and manipulation to extract cryptographic keys or sensitive information from individuals. Techniques often involve exploiting fear, stress, and cognitive overload to force compliance without directly attacking the cryptographic system. These human-centric attacks highlight vulnerabilities in security that go beyond algorithmic weaknesses, emphasizing the importance of safeguarding not just data but also the individuals holding the secrets.
Legal and Ethical Implications of Rubber-Hose Methods
Rubber-hose cryptanalysis involves coercive techniques, such as physical intimidation or threats, to extract cryptographic keys or sensitive information, raising significant legal concerns under laws prohibiting torture and unlawful detention. Ethical implications include violations of human rights, undermining trust in security systems, and potential misuse by authoritarian regimes to suppress dissent. Organizations must navigate these challenges by enforcing strict compliance with international legal standards and promoting ethical cryptographic practices to protect individual privacy and integrity.
Preventing Rubber-Hose Attacks: Security Best Practices
Implementing strong physical security measures and secure key management protocols significantly reduces the risk of rubber-hose attacks in cryptanalysis. Utilizing hardware security modules (HSMs) and multi-factor authentication ensures that cryptographic keys remain inaccessible under coercion. Regular training on secure handling of sensitive information and legal protections for whistleblowers further enhance resistance against forced key disclosure.
Human Factor Vulnerabilities in Cryptography
Rubber-hose cryptanalysis exemplifies human factor vulnerabilities in cryptography by exploiting physical coercion to extract cryptographic keys from individuals. This attack targets the weakest link in security systems: human operators, bypassing mathematical complexity through intimidation or violence. Understanding and mitigating such vulnerabilities require integrating robust security policies and psychological resilience measures alongside technical safeguards.
Lessons Learned from Rubber-Hose Incident Case Studies
Rubber-hose cryptanalysis demonstrates that physical coercion can undermine even the strongest encryption by forcing users to reveal keys. Case studies reveal the critical need for secure hardware designs and plausible deniability features to protect sensitive data under duress. Implementing multi-layered security protocols and employee training on handling coercion significantly reduces risks exposed by rubber-hose attacks.
example of rubber-hose in cryptanalysis Infographic
 samplerz.com
samplerz.com