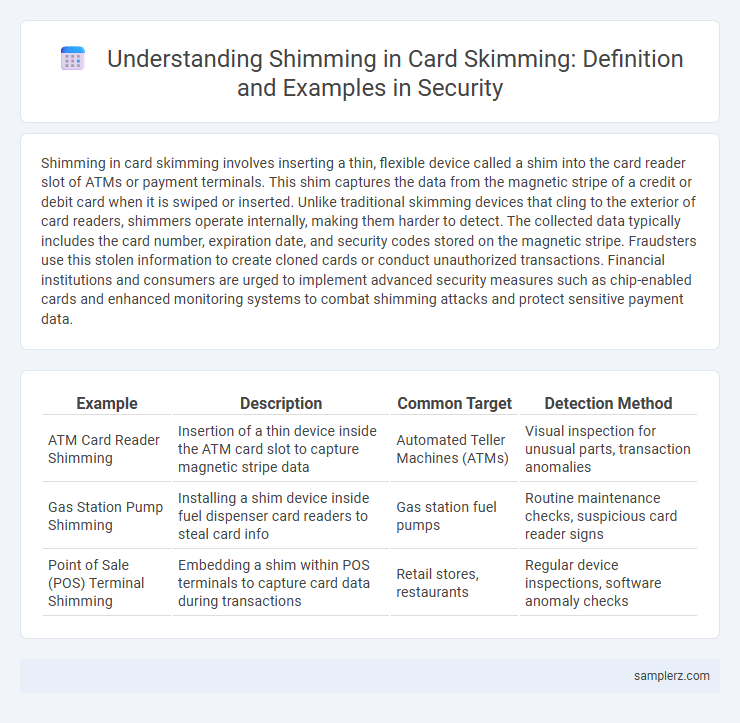
Shimming in card skimming involves inserting a thin, flexible device called a shim into the card reader slot of ATMs or payment terminals. This shim captures the data from the magnetic stripe of a credit or debit card when it is swiped or inserted. Unlike traditional skimming devices that cling to the exterior of card readers, shimmers operate internally, making them harder to detect. The collected data typically includes the card number, expiration date, and security codes stored on the magnetic stripe. Fraudsters use this stolen information to create cloned cards or conduct unauthorized transactions. Financial institutions and consumers are urged to implement advanced security measures such as chip-enabled cards and enhanced monitoring systems to combat shimming attacks and protect sensitive payment data.
Table of Comparison
| Example | Description | Common Target | Detection Method |
|---|---|---|---|
| ATM Card Reader Shimming | Insertion of a thin device inside the ATM card slot to capture magnetic stripe data | Automated Teller Machines (ATMs) | Visual inspection for unusual parts, transaction anomalies |
| Gas Station Pump Shimming | Installing a shim device inside fuel dispenser card readers to steal card info | Gas station fuel pumps | Routine maintenance checks, suspicious card reader signs |
| Point of Sale (POS) Terminal Shimming | Embedding a shim within POS terminals to capture card data during transactions | Retail stores, restaurants | Regular device inspections, software anomaly checks |
Understanding Card Shimming: A Modern Skimming Technique
Card shimming is a sophisticated skimming method where attackers insert a thin device called a shim into a card reader's slot to capture data from the magnetic stripe or chip during a legitimate transaction. This technique targets EMV chip-enabled cards by intercepting communication between the card and terminal, allowing criminals to clone cards or conduct unauthorized transactions. Understanding card shimming is crucial for enhancing security measures in payment systems and reducing fraud risks associated with contactless and chip card payments.
How Shimming Differs from Traditional Card Skimming
Shimming involves inserting a thin, flexible device inside the card reader slot to capture data directly from the card's chip, while traditional card skimming relies on external devices that read magnetic stripe information. Unlike skimmers that clone magnetic strip data, shimmers extract encrypted chip data, making them harder to detect and more dangerous. This distinction highlights the advanced techniques criminals use to bypass chip security on EMV-enabled payment cards.
Real-World Examples of Shimming Attacks
Real-world examples of shimming attacks include cybercriminals inserting thin, flexible devices into ATM card readers to capture magnetic stripe data and PINs. In 2018, multiple ATMs in the United States were compromised using shimming devices that intercepted payment card information, leading to widespread financial fraud. Banks and security experts emphasize the importance of updated chip technology and anti-shimming sensors to prevent such card skimming breaches.
Common Locations Targeted by Shimming Devices
Shimming devices are frequently installed at ATM card readers, gas station pumps, and retail point-of-sale terminals, where card inserts create an opportunity for unauthorized data capture. These compact, often nearly invisible devices extract data from magnetic stripes or chip contacts during legitimate card transactions. Retail environments with unattended card readers rank high as targeted locations due to less frequent oversight and high consumer traffic.
Anatomy of a Card Shim: What Does It Look Like?
A card shim used in skimming typically resembles a thin, flexible plastic or metal strip designed to fit discreetly between the card and the ATM or POS slot. Its surface mimics the card reader's interior to capture magnetic stripe data without detection. The shim's subtle thickness and covert placement are crucial for harvesting sensitive card information during legitimate transactions.
Step-by-Step: How Criminals Install Shimming Devices
Criminals install shimming devices by carefully removing or loosening the card reader's outer casing to access the internal card slot. They then insert the slim, flexible shim device between the card slot and the card, capturing data from the card's magnetic stripe or chip during each transaction. Finally, the casing is securely reassembled to avoid detection while the shim discreetly records sensitive payment information.
Recognizing Signs of Card Shimming at ATMs and POS Terminals
Visible damage or loose parts around the card slot at ATMs and POS terminals can indicate the presence of shimming devices used to steal card data. Unusual or sticky card reader surfaces and slow card processing times often signal tampering for card skimming. Users should remain vigilant for these signs to prevent unauthorized data capture through shimming techniques.
Notable Shimming Incidents and Case Studies
Notable shimming incidents include the 2018 case where criminals targeted ATMs in Europe using thin devices inserted into card readers to capture data from EMV chip cards, compromising thousands of users. In the 2019 US case, a shimming attack on gas station payment terminals resulted in hundreds of stolen card credentials, highlighting vulnerabilities in point-of-sale systems. These case studies demonstrate how shimming exploits the EMV chip's communication to steal sensitive payment information without physical card theft.
The Evolving Threat: Latest Trends in Shimming
Shimming in card skimming involves inserting a thin device into card readers to capture data from the card's chip, exploiting vulnerabilities in EMV technology. Recent trends show increased use of Bluetooth-enabled shims, allowing criminals to wirelessly transmit stolen card information, heightening the risk for consumers and financial institutions. Advanced shimming devices now bypass security measures by mimicking legitimate card reader signals, making detection more challenging.
Protecting Your Card: Security Tips Against Shimming
Shimming in card skimming involves inserting a thin, flexible device into the card reader, capturing data from the chip during legitimate transactions. Protecting your card requires regularly inspecting ATMs and payment terminals for unusual parts, shielding your PIN with your hand, and using contactless payments when possible. Enabling card alerts and promptly reporting suspicious activity helps mitigate the risk of unauthorized access and financial loss.
example of shimming in card skimming Infographic
 samplerz.com
samplerz.com