Tailgating in physical access occurs when an unauthorized individual follows an authorized person into a secure area without proper credentials. For instance, an employee swiping their access card and holding the door open for someone behind them who does not have clearance exemplifies tailgating. This breach exploits the trust and courtesy typically extended among colleagues, compromising facility security. Security systems rely on entities such as access control panels, biometric scanners, and surveillance cameras to prevent tailgating incidents. Data from these devices can identify patterns of unauthorized entries, enabling organizations to strengthen their perimeter defenses. Monitoring tailgating events helps reduce risks of theft, espionage, and physical harm within sensitive environments.
Table of Comparison
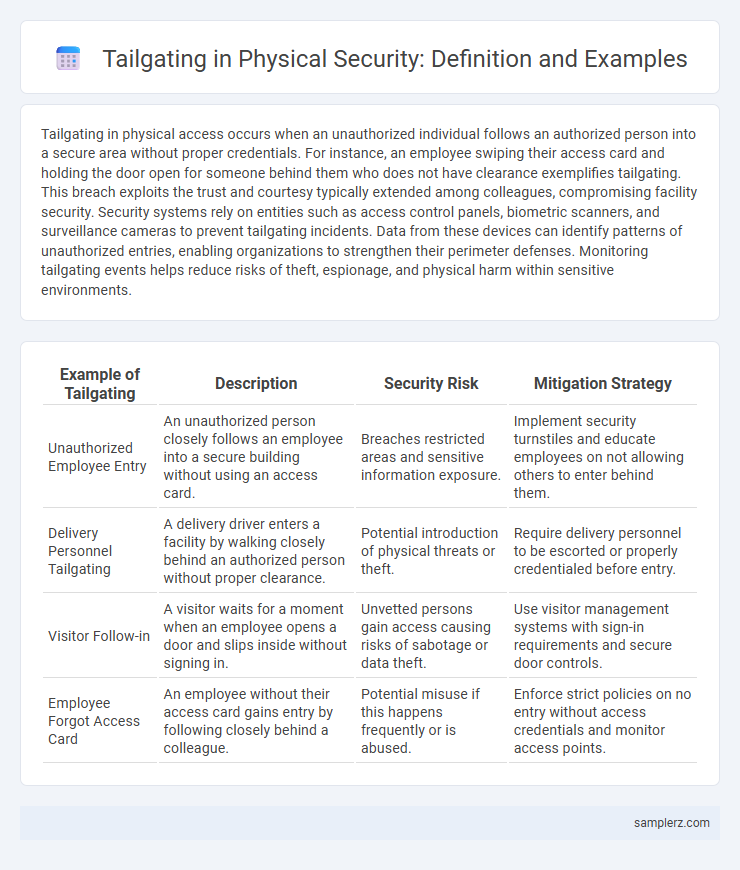
| Example of Tailgating | Description | Security Risk | Mitigation Strategy |
|---|---|---|---|
| Unauthorized Employee Entry | An unauthorized person closely follows an employee into a secure building without using an access card. | Breaches restricted areas and sensitive information exposure. | Implement security turnstiles and educate employees on not allowing others to enter behind them. |
| Delivery Personnel Tailgating | A delivery driver enters a facility by walking closely behind an authorized person without proper clearance. | Potential introduction of physical threats or theft. | Require delivery personnel to be escorted or properly credentialed before entry. |
| Visitor Follow-in | A visitor waits for a moment when an employee opens a door and slips inside without signing in. | Unvetted persons gain access causing risks of sabotage or data theft. | Use visitor management systems with sign-in requirements and secure door controls. |
| Employee Forgot Access Card | An employee without their access card gains entry by following closely behind a colleague. | Potential misuse if this happens frequently or is abused. | Enforce strict policies on no entry without access credentials and monitor access points. |
Common Real-World Tailgating Scenarios
Common real-world tailgating scenarios in physical access security include unauthorized individuals closely following employees through secured doors without using access credentials. This often occurs in busy office environments during peak hours, where employees may hold doors open for others out of courtesy. Tailgating exploits human trust and highlights the need for strict access control policies and employee awareness training.
Social Engineering Tactics Used in Tailgating
Tailgating in physical security often involves attackers exploiting social engineering tactics such as pretending to be delivery personnel or employees to gain unauthorized access. They leverage human behaviors like politeness, trust, and the reluctance to challenge unfamiliar individuals to bypass access controls. Understanding these manipulative strategies is crucial for implementing effective security awareness training and access protocols.
Tailgating at Office Buildings: Case Studies
Tailgating at office buildings occurs when unauthorized individuals follow employees through secured entry points without proper credentials, often bypassing access control systems. Case studies reveal that tailgating exploits common vulnerabilities such as complacent staff and poor visitor protocols, leading to breaches that can compromise sensitive information and physical assets. Implementing strict access policies, employee training, and advanced authentication technologies significantly reduces the risk of tailgating incidents in corporate environments.
High-Risk Locations Vulnerable to Tailgating
High-risk locations vulnerable to tailgating include data centers, server rooms, and secure research facilities where unauthorized entry can lead to significant security breaches or data theft. Facilities with multiple employees entering simultaneously or areas with badge readers often face challenges in preventing tailgating due to human error or lack of advanced access controls. Implementing biometric authentication and anti-passback systems enhances security by ensuring only authorized personnel gain access without following closely behind others.
Insider vs. Outsider Tailgating Techniques
Insider tailgating often involves employees exploiting familiar routes or social norms, such as holding doors open for colleagues, to bypass security without raising suspicion. Outsider tailgating techniques typically include blending with authorized personnel during peak hours or using stolen or cloned access credentials to gain entry unnoticed. Both methods highlight vulnerabilities in physical access controls, emphasizing the need for strict authentication and employee awareness training.
Tailgating in Data Centers: Security Breaches
Tailgating in data centers occurs when unauthorized individuals follow authorized personnel through secure access points without proper authentication, bypassing biometric scanners or keycard systems. This security breach can lead to unauthorized access to sensitive hardware, data theft, or sabotage, posing significant risks to operational integrity. Implementing measures such as anti-tailgating turnstiles, multi-factor authentication, and continuous surveillance helps mitigate these vulnerabilities in physical access controls.
Notable Tailgating Incidents in Corporate Environments
Notable tailgating incidents in corporate environments often involve unauthorized individuals gaining physical access by closely following employees through secure entry points, bypassing badge or biometric verification. For instance, in 2018, a major tech company's headquarters experienced a security breach when an intruder tailgated an employee into a restricted server room, leading to data theft. These incidents highlight vulnerabilities in physical access controls and the critical need for enhanced employee training and advanced authentication systems.
Methods Used by Attackers to Tailgate
Tailgating in physical security involves attackers closely following authorized personnel to gain entry into restricted areas without proper credentials. Common methods include pretending to carry heavy objects or appearing distracted to discourage staff from challenging their unauthorized access. Attackers may also exploit crowded entryways or use social engineering tactics to manipulate employees into holding doors open.
Consequences of Successful Tailgating Attacks
Successful tailgating attacks in physical access control can lead to unauthorized entry, resulting in data breaches, theft of sensitive equipment, and disruption of business operations. These security violations often compromise employee safety and expose organizations to legal liabilities and substantial financial losses. Effective countermeasures such as multi-factor authentication and strict visitor management are critical to mitigating these risks.
Recognizing Red Flags: Spotting Tailgaters in Action
Tailgating in physical access security occurs when an unauthorized person follows closely behind an authorized individual to gain entry without proper credentials. Key red flags include individuals loitering near secure entrances, hesitating or appearing nervous, and avoiding direct contact with access control systems while slipping through doors. Vigilant employees and security personnel trained to identify these behaviors play a crucial role in preventing unauthorized access and maintaining facility integrity.
example of tailgating in physical access Infographic
 samplerz.com
samplerz.com