A logic bomb in software is a malicious code designed to trigger a harmful action when specific conditions are met. One example is the infamous "CIH" virus, also known as the Chernobyl virus, which activated on April 26th, the anniversary of the Chernobyl nuclear disaster, corrupting data and rendering computer systems inoperable. This type of logic bomb demonstrates how software can be weaponized to cause widespread damage through timed or conditional triggers. Another example is the case of an insider planting a logic bomb within enterprise payroll software that deletes critical payroll files when a departing employee's ID is removed from the system. This attack exploits internal data conditions to disrupt business operations and cause financial chaos. Detecting and mitigating such logic bombs requires continuous monitoring of software behavior and the implementation of strict access controls.
Table of Comparison
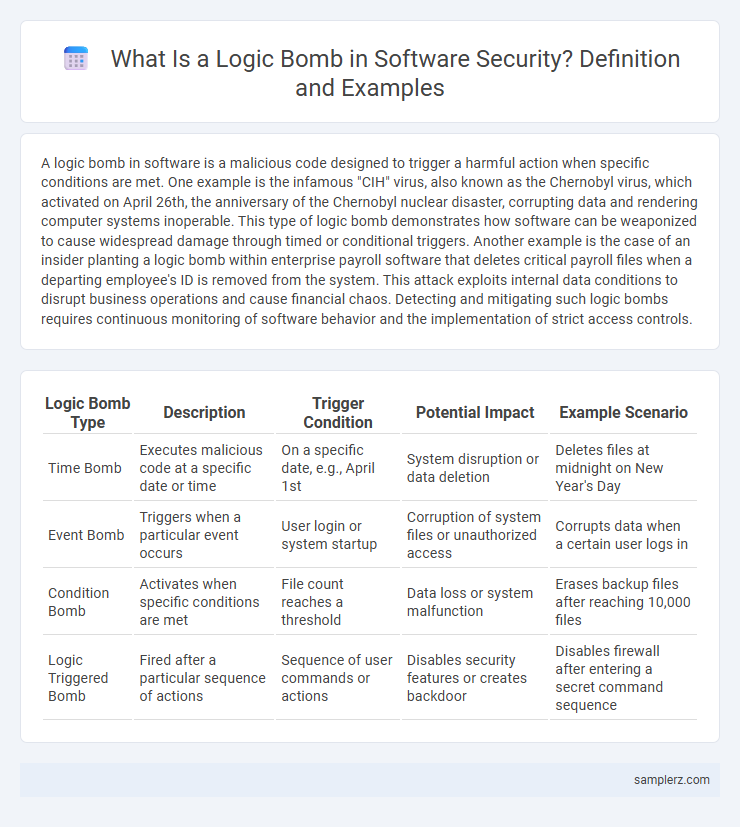
| Logic Bomb Type | Description | Trigger Condition | Potential Impact | Example Scenario |
|---|---|---|---|---|
| Time Bomb | Executes malicious code at a specific date or time | On a specific date, e.g., April 1st | System disruption or data deletion | Deletes files at midnight on New Year's Day |
| Event Bomb | Triggers when a particular event occurs | User login or system startup | Corruption of system files or unauthorized access | Corrupts data when a certain user logs in |
| Condition Bomb | Activates when specific conditions are met | File count reaches a threshold | Data loss or system malfunction | Erases backup files after reaching 10,000 files |
| Logic Triggered Bomb | Fired after a particular sequence of actions | Sequence of user commands or actions | Disables security features or creates backdoor | Disables firewall after entering a secret command sequence |
Understanding Logic Bombs: Definition and Mechanics
A logic bomb is a malicious code embedded within legitimate software that triggers harmful actions when specific conditions are met, such as a particular date or user activity. These covert attacks operate silently until activation, causing data corruption, system crashes, or unauthorized access. Understanding the mechanics of logic bombs is crucial for implementing effective detection and prevention strategies in cybersecurity frameworks.
Notorious Real-World Logic Bomb Incidents
The 1991 CIH virus, also known as Chernobyl, is a notorious example of a logic bomb that triggered on April 26, corrupting system BIOS and rendering computers unbootable. Another infamous incident involved the Toshiba hard drive logic bomb in 2002, where a scheduled event caused data corruption in some laptop hard drives. These logic bombs exploit specific triggers to execute malicious payloads, often causing severe data loss and system damage.
Famous Logic Bombs Embedded in Corporate Software
The infamous CIH virus, also known as Chernobyl, is a notorious example of a logic bomb embedded in corporate software that activated on a specific date, corrupting system BIOS and causing irreparable damage. Another significant case involved the Time bomb inserted into the Microsoft Windows operating system, which delayed system processes and crippled functionality on a targeted future date. These logic bombs serve as powerful reminders of the vulnerabilities within corporate software, highlighting the necessity of robust security protocols and constant vigilance against malicious code hidden in legitimate programs.
Insider Threats: Employees Planting Logic Bombs
Employees posing insider threats often plant logic bombs within software to execute malicious code at specific triggers, compromising system integrity and data security. These hidden payloads remain dormant until activated by certain conditions, such as date, user action, or system event, making detection challenging for traditional security measures. Notable incidents reveal that insider logic bombs can cause significant operational disruptions and data breaches, emphasizing the need for advanced monitoring and behavior-based threat detection systems.
Logic Bombs Hidden in Third-Party Software
Logic bombs hidden in third-party software pose significant cybersecurity risks by activating malicious code under specific conditions, such as dates or user actions. These threats often evade detection during standard software testing and can disrupt operations, steal data, or damage systems once triggered. Vigilant code reviews and continuous monitoring of third-party components are essential to prevent and mitigate logic bomb attacks.
Logic Bomb Attack on Financial Institutions
Logic bomb attacks on financial institutions often involve malicious code embedded within software that triggers unauthorized transactions or data corruption when specific conditions are met. These attacks can result in severe financial losses, compromise sensitive customer information, and disrupt critical banking operations. Detecting and preventing logic bombs requires rigorous code auditing, real-time monitoring, and implementation of advanced intrusion detection systems specific to financial software environments.
Case Study: Logic Bomb in Government Networks
A notable case study of a logic bomb in government networks involved a disgruntled insider who embedded malicious code within critical system software, triggering data destruction after a specific date. This logic bomb caused widespread disruption by corrupting sensitive files and disabling network access, highlighting vulnerabilities in insider threat detection protocols. The incident underscores the importance of rigorous code audits, behavioral monitoring, and layered security controls to prevent similar attacks in government infrastructures.
Logic Bombs in Industrial Control Systems
Logic bombs in industrial control systems (ICS) pose severe risks by triggering malicious actions when specific conditions are met, such as shutting down critical infrastructure or altering control parameters. A notorious example is the 2017 Triton malware attack targeting safety instrumented systems in petrochemical plants, which aimed to cause physical damage by disabling safety mechanisms. These embedded logic bombs exploit the deterministic nature of ICS environments, making early detection and tailored cybersecurity measures essential to prevent catastrophic consequences.
Detecting and Preventing Logic Bombs in Code
Logic bombs, malicious code segments triggered by specific conditions, can be detected by monitoring atypical system behavior and performing thorough code reviews using automated static analysis tools. Implementing behavioral analytics and real-time monitoring helps identify unauthorized changes or access patterns that precede logic bomb activation. Preventing logic bombs involves enforcing strict access controls, segregating duties in development environments, and using version control systems to track and audit code modifications.
Lessons Learned from Historic Logic Bomb Cases
Historic logic bomb cases like the 2006 Sony BMG rootkit exposed critical vulnerabilities in software security by demonstrating how concealed malicious code can trigger system damage under specific conditions. Lessons learned emphasize the importance of rigorous code audits, continuous monitoring, and implementing fail-safes to detect and prevent unauthorized or harmful logic embedded within applications. Strengthening software development lifecycle protocols and educating developers on secure coding practices remain essential to mitigate risks associated with logic bombs.
example of logic bomb in software Infographic
 samplerz.com
samplerz.com