An enclave in a processor refers to a secure area within the CPU designed to protect sensitive data and code from unauthorized access. One prominent example is Intel SGX (Software Guard Extensions), which creates isolated execution environments called enclaves. These enclaves enable applications to run confidential computations even if the operating system or hypervisor is compromised. ARM TrustZone is another example of an enclave technology in processors, providing hardware isolation between secure and non-secure worlds. TrustZone divides system resources, allowing secure applications to execute safely inside the secure world. Both Intel SGX and ARM TrustZone enhance security by safeguarding critical operations and sensitive information against various attack vectors.
Table of Comparison
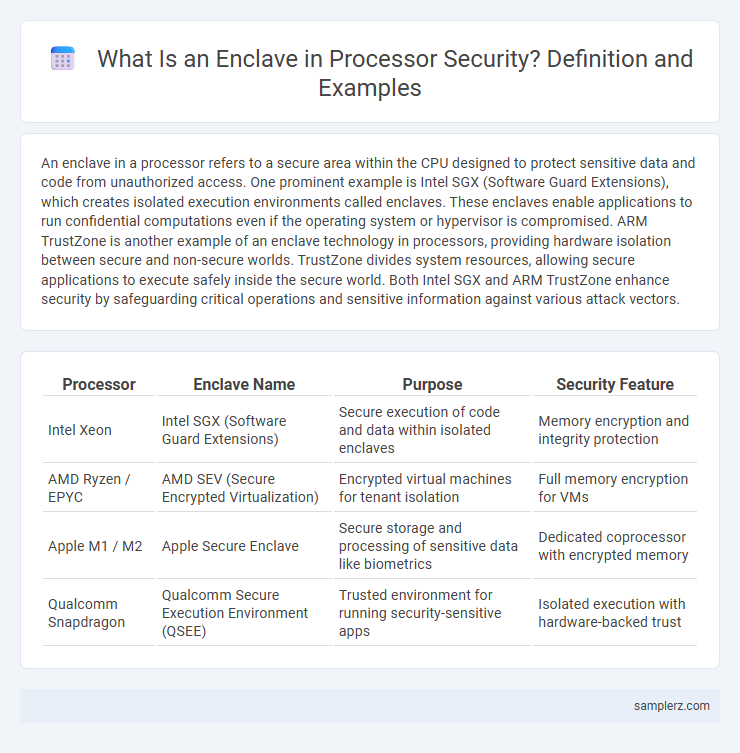
| Processor | Enclave Name | Purpose | Security Feature |
|---|---|---|---|
| Intel Xeon | Intel SGX (Software Guard Extensions) | Secure execution of code and data within isolated enclaves | Memory encryption and integrity protection |
| AMD Ryzen / EPYC | AMD SEV (Secure Encrypted Virtualization) | Encrypted virtual machines for tenant isolation | Full memory encryption for VMs |
| Apple M1 / M2 | Apple Secure Enclave | Secure storage and processing of sensitive data like biometrics | Dedicated coprocessor with encrypted memory |
| Qualcomm Snapdragon | Qualcomm Secure Execution Environment (QSEE) | Trusted environment for running security-sensitive apps | Isolated execution with hardware-backed trust |
Introduction to Processor Enclaves
Processor enclaves, such as Intel SGX (Software Guard Extensions), create isolated execution environments within a CPU that protect sensitive data and code from unauthorized access, even from privileged software like operating systems. These hardware-based secure enclaves use encryption and memory isolation to ensure confidentiality and integrity during runtime. By compartmentalizing critical operations, enclaves mitigate risks posed by malware, rootkits, and other system-level attacks, enhancing overall cybersecurity posture.
Core Principles of Enclave Technology
Enclave technology in processors, such as Intel SGX, implements hardware-based isolated execution environments that protect sensitive data even from privileged software. Core principles include memory encryption, which safeguards code and data within the enclave, and attestation, enabling remote verification of enclave integrity. These mechanisms ensure secure computation by preventing unauthorized access and maintaining confidentiality and integrity during processing.
Real-World Examples of Enclaves in CPUs
Intel SGX (Software Guard Extensions) exemplifies a real-world enclave technology integrated into modern CPUs, enabling developers to create protected areas of execution called enclaves that safeguard sensitive data and code from unauthorized access even with system-level attacks. ARM's TrustZone is another prominent example, segmenting the processor into secure and non-secure worlds to isolate critical operations and secure key management. AMD's SEV (Secure Encrypted Virtualization) extends enclave concepts by encrypting virtual machines at the hardware level, protecting data in use from hypervisor and physical memory attacks.
Intel SGX: Secure Enclave in Modern Processors
Intel SGX (Software Guard Extensions) provides a hardware-based secure enclave within modern processors, isolating sensitive code and data from unauthorized access even if the operating system is compromised. This technology leverages memory encryption and hardware-enforced boundaries to protect enclaves against a wide range of software attacks. Intel SGX is widely used in securing applications like confidential computing, digital rights management, and secure data processing in cloud environments.
AMD SEV: Enclaves for Virtualization Security
AMD SEV (Secure Encrypted Virtualization) creates secure enclaves within a processor to protect virtual machines from unauthorized access by encrypting their memory. This technology isolates guest VMs from the hypervisor and other system components, enhancing confidentiality and integrity in cloud environments. AMD SEV leverages hardware-based encryption keys unique to each VM, ensuring robust security boundaries for sensitive workloads.
ARM TrustZone: Enclave Architecture for Mobile Chips
ARM TrustZone provides a hardware-based security architecture that creates a secure enclave within mobile processors by partitioning execution environments into Secure and Non-Secure worlds. This isolation ensures that sensitive operations, such as cryptographic key management and biometric data processing, run within the Trusted Execution Environment (TEE), protecting them from potentially compromised applications. TrustZone's secure monitor manages context switching between these worlds, enabling seamless yet robust protection against software attacks on ARM-based mobile chips.
Apple Secure Enclave: Hardware-Based Security Example
Apple Secure Enclave is a hardware-based security coprocessor integrated into Apple devices, designed to manage sensitive data like biometric information and cryptographic keys. It operates with its own secure boot process and isolated memory, ensuring that critical operations such as Face ID and Touch ID authentication are protected from software attacks. The Secure Enclave's architecture demonstrates advanced hardware encryption and secure key management techniques that enhance device security and user privacy.
Key Use Cases of Processor Enclaves in Security
Processor enclaves, such as Intel SGX and AMD SEV, provide hardware-based isolation to protect sensitive data and code from unauthorized access even in compromised systems. Key use cases include secure key management, confidential data processing, and trusted execution of cryptographic operations, ensuring that critical security tasks remain tamper-resistant. Enclaves also enable secure remote attestation, allowing verification of enclave integrity to establish trust in cloud computing and multi-tenant environments.
Comparing Popular Processor Enclave Technologies
Intel SGX (Software Guard Extensions) and AMD SEV (Secure Encrypted Virtualization) represent two prominent enclave technologies in modern processors, offering distinct approaches to secure computation. Intel SGX provides fine-grained, application-level enclaves that isolate specific code and data, while AMD SEV encrypts entire virtual machines to protect the confidentiality and integrity of memory contents. Both technologies enhance hardware-based security but differ in granularity and implementation, with SGX favoring small, isolated environments and SEV enabling broader virtualization security.
Future Trends in Processor Enclave Development
Future trends in processor enclave development emphasize enhanced hardware-based security features such as Intel SGX and AMD SEV that isolate sensitive data from the main operating system. Innovations include increased enclave memory size, improved cryptographic mechanisms, and support for confidential computing workloads in cloud environments. Advancements in trusted execution environments (TEEs) aim to strengthen data integrity and privacy while minimizing performance overhead in next-generation processors.
example of enclave in processor Infographic
 samplerz.com
samplerz.com