Tailgating in physical security occurs when an unauthorized individual gains access to a secure area by following closely behind an authorized person without their knowledge. This breach exploits human trust and the lack of stringent verification protocols at entry points such as doors or gates. Data from security audits shows that tailgating incidents often result in significant vulnerabilities in high-security environments like corporate offices and data centers. Entities involved in tailgating scenarios include security personnel, authorized employees, and intruders. Surveillance systems and access control devices provide critical data to identify and mitigate tailgating risks. Implementing measures like turnstiles, biometric scanners, and employee awareness training can significantly reduce the occurrence of this security threat.
Table of Comparison
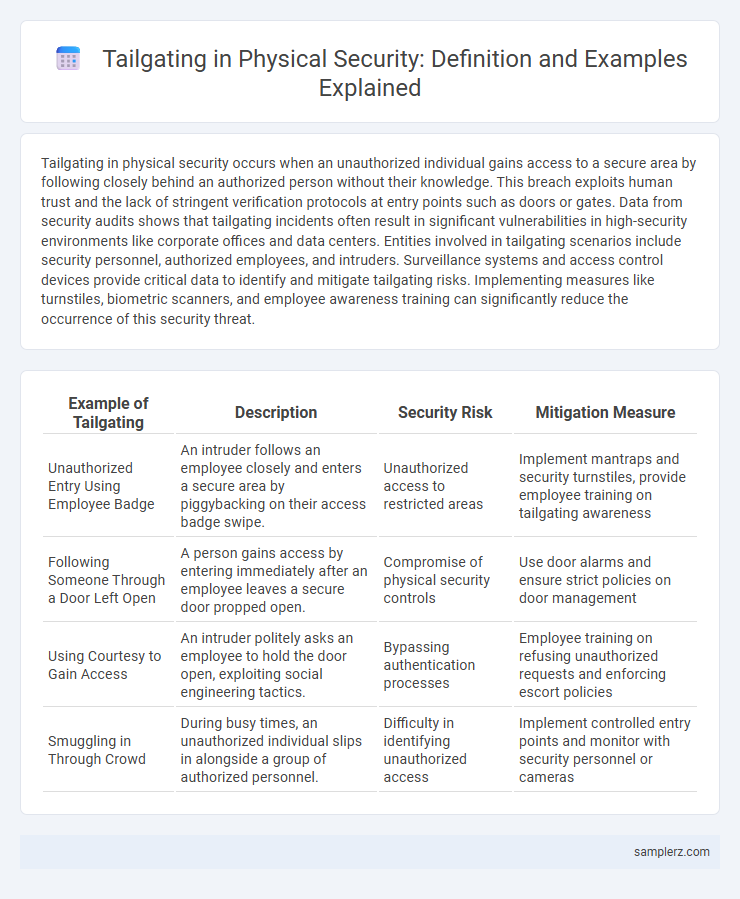
| Example of Tailgating | Description | Security Risk | Mitigation Measure |
|---|---|---|---|
| Unauthorized Entry Using Employee Badge | An intruder follows an employee closely and enters a secure area by piggybacking on their access badge swipe. | Unauthorized access to restricted areas | Implement mantraps and security turnstiles, provide employee training on tailgating awareness |
| Following Someone Through a Door Left Open | A person gains access by entering immediately after an employee leaves a secure door propped open. | Compromise of physical security controls | Use door alarms and ensure strict policies on door management |
| Using Courtesy to Gain Access | An intruder politely asks an employee to hold the door open, exploiting social engineering tactics. | Bypassing authentication processes | Employee training on refusing unauthorized requests and enforcing escort policies |
| Smuggling in Through Crowd | During busy times, an unauthorized individual slips in alongside a group of authorized personnel. | Difficulty in identifying unauthorized access | Implement controlled entry points and monitor with security personnel or cameras |
Definition of Tailgating in Physical Security
Tailgating in physical security refers to the unauthorized entry of an individual who closely follows an authorized person into a secured area without proper authentication. This security breach exploits the trust or negligence of the authorized person, allowing intruders to bypass access controls such as key cards, biometric scanners, or security checkpoints. Effective countermeasures include enforcing strict access protocols, deploying anti-tailgating sensors, and conducting employee awareness training to recognize and prevent unauthorized entry.
Common Scenarios of Tailgating Attacks
Common scenarios of tailgating attacks include unauthorized individuals closely following authorized employees through secure doors or entry points without proper authentication. Attackers often exploit busy office environments, piggybacking on employees holding doors open during peak hours. Another frequent situation occurs in parking garages where tailgaters slip in behind vehicles with valid access credentials, bypassing security checkpoints.
Real-World Examples of Tailgating Incidents
Tailgating incidents in physical security often occur when unauthorized individuals closely follow employees into secure areas without proper authentication, such as when a visitor slips in behind an employee using a keycard entry system. A notable example is the 2017 security breach at a major financial institution where an intruder gained access by tailgating employees into a restricted data center, leading to a compromise of sensitive client information. Corporate offices and data centers remain prime targets for tailgating attacks, highlighting the necessity for strict access control and employee vigilance.
Tailgating in Corporate Office Environments
Tailgating in corporate office environments occurs when an unauthorized person closely follows an authorized employee through secure entry points without proper credentials. This security breach often exploits momentary lapses in access control systems or employee vigilance, leading to potential data theft or workplace safety risks. Implementing multi-factor authentication and employee awareness training significantly reduces the chances of tailgating incidents.
Tailgating Risks in Data Centers and Server Rooms
Tailgating in data centers and server rooms occurs when unauthorized individuals gain access by closely following authorized personnel without proper authentication. This breach exposes critical infrastructure to risks such as data theft, hardware tampering, and service disruption. Implementing strict entry controls, biometric verification, and surveillance systems can significantly reduce tailgating vulnerabilities in these high-security environments.
Visitor Management Failures Leading to Tailgating
Visitor management failures, such as improper check-in procedures and lack of identity verification, significantly increase the risk of tailgating in physical security. When unauthorized individuals exploit unsecured entry points by closely following authorized personnel, it compromises the integrity of access control systems. Effective visitor screening and strict enforcement of access policies are critical in preventing tailgating incidents and maintaining secure premises.
Tailgating Exploits in Government Buildings
Tailgating exploits in government buildings often involve unauthorized individuals closely following authorized personnel through secure entry points without proper credentials, bypassing access control systems. This security breach can lead to significant risks including data theft, sabotage, and threats to national security due to the sensitive nature of government operations. Implementing multi-factor authentication, security guards, and anti-tailgating technologies like mantraps significantly reduces the vulnerability of government facilities to such exploits.
Social Engineering Tactics in Tailgating
Tailgating in physical security involves an unauthorized person closely following an authorized individual into a secured area without proper authentication, exploiting trust and social norms. Social engineering tactics used in tailgating include impersonating employees, delivery personnel, or maintenance staff to bypass access controls and manipulate individuals into holding doors open. This method preys on human psychology, relying on courtesy and distraction to gain entry and compromise security protocols.
Notable Tailgating Breaches and Their Impact
Notable tailgating breaches include the 2013 Target data breach, where unauthorized individuals gained physical access through employees holding doors open, leading to the theft of 40 million credit and debit card records. Another significant incident occurred at the U.S. Capitol in 2021, with unauthorized persons exploiting tailgating to enter restricted areas, highlighting vulnerabilities in access controls. These breaches underscore the critical need for strict physical security protocols and employee awareness to prevent unauthorized access and data compromise.
Lessons Learned from Tailgating Case Studies
Tailgating in physical security often involves unauthorized individuals gaining access by closely following authorized personnel through secure entry points, highlighting the critical need for robust access control protocols. Lessons learned from tailgating case studies emphasize the importance of employee training, implementation of mantraps or turnstiles, and deploying surveillance systems to detect and deter unauthorized entry. Organizations that reinforce strict visitor policies and foster a security-conscious culture significantly reduce the risk of tailgating breaches and enhance overall facility protection.
example of tailgating in physical security Infographic
 samplerz.com
samplerz.com