Pharming in website security refers to a cyberattack where attackers redirect users from legitimate websites to fraudulent ones without their knowledge. This type of attack manipulates DNS (Domain Name System) entries or exploits vulnerabilities in the victim's computer or router, causing the user to unknowingly enter sensitive information like login credentials or financial data on a fake site. Pharming poses significant risks to entities handling large amounts of personal or financial data, as it enables attackers to harvest information stealthily. One example of pharming occurred when attackers compromised DNS servers to redirect visitors from a well-known banking website to a counterfeit page mimicking the original. Users attempting to log in were unaware that their credentials were being stolen due to the similarity of the fake site's appearance and URL structure. Security measures such as DNSSEC (Domain Name System Security Extensions) and continuous monitoring of DNS records are crucial for organizations to detect and prevent pharming attacks effectively.
Table of Comparison
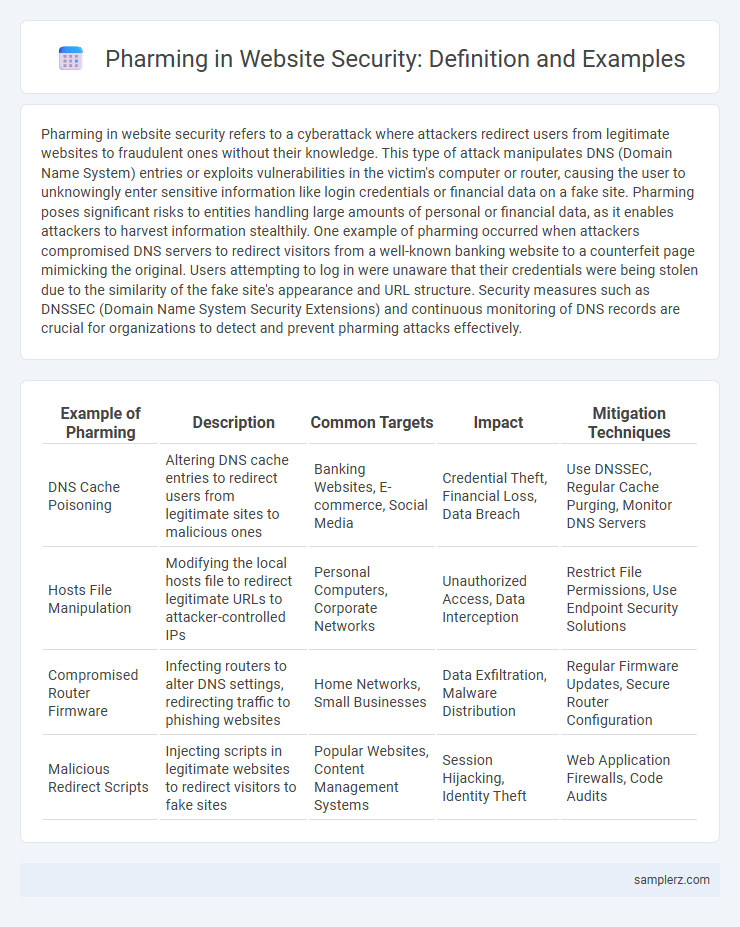
| Example of Pharming | Description | Common Targets | Impact | Mitigation Techniques |
|---|---|---|---|---|
| DNS Cache Poisoning | Altering DNS cache entries to redirect users from legitimate sites to malicious ones | Banking Websites, E-commerce, Social Media | Credential Theft, Financial Loss, Data Breach | Use DNSSEC, Regular Cache Purging, Monitor DNS Servers |
| Hosts File Manipulation | Modifying the local hosts file to redirect legitimate URLs to attacker-controlled IPs | Personal Computers, Corporate Networks | Unauthorized Access, Data Interception | Restrict File Permissions, Use Endpoint Security Solutions |
| Compromised Router Firmware | Infecting routers to alter DNS settings, redirecting traffic to phishing websites | Home Networks, Small Businesses | Data Exfiltration, Malware Distribution | Regular Firmware Updates, Secure Router Configuration |
| Malicious Redirect Scripts | Injecting scripts in legitimate websites to redirect visitors to fake sites | Popular Websites, Content Management Systems | Session Hijacking, Identity Theft | Web Application Firewalls, Code Audits |
Understanding Pharming in Website Security
Pharming is a cyberattack where malicious code redirects users from legitimate websites to fraudulent ones without their knowledge, often through DNS cache poisoning or hosts file manipulation. This technique exploits vulnerabilities in website security to capture sensitive data such as login credentials, financial information, and personal details. Understanding pharming is crucial for implementing robust DNS security measures and educating users about safe browsing habits to prevent data breaches.
Real-World Examples of Pharming Attacks
Pharming attacks redirect users from legitimate websites to fraudulent ones by exploiting DNS vulnerabilities or altering local hosts files, commonly seen in cases such as the 2017 DNSChanger malware campaign that infected millions of devices worldwide. Another notable example occurred in 2010 when hackers targeted banking customers by poisoning DNS servers to redirect traffic to fake banking sites, leading to significant financial losses. These real-world pharming attacks underscore the importance of robust DNS security protocols and continuous monitoring to prevent unauthorized DNS modifications.
DNS Spoofing: A Common Pharming Technique
DNS spoofing, a prevalent pharming technique, manipulates Domain Name System records to redirect users from legitimate websites to malicious ones without their knowledge. Attackers exploit vulnerabilities in DNS servers or caches, altering IP address mappings to intercept sensitive data such as login credentials and financial information. This form of DNS cache poisoning compromises website security by undermining trust in domain name resolutions and enabling widespread credential theft.
High-Profile Pharming Incidents in E-Commerce
High-profile pharming incidents in e-commerce often involve attackers redirecting users from legitimate online retail websites to fraudulent platforms designed to steal sensitive data such as credit card information and login credentials. Notable cases include the 2018 attack on a major international retailer where hackers manipulated DNS settings to reroute traffic, resulting in significant financial losses and compromised customer trust. These attacks emphasize the critical need for robust DNS security measures like DNSSEC and continuous monitoring to protect e-commerce platforms from pharming threats.
Banking Websites Targeted by Pharming Attacks
Pharming attacks on banking websites manipulate DNS settings or exploit vulnerabilities to redirect users to fraudulent sites designed to steal login credentials. Cybercriminals often target major financial institutions such as Bank of America, Wells Fargo, and Chase, causing significant financial loss and data breaches. Effective countermeasures include DNSSEC implementation, multi-factor authentication, and continuous monitoring of DNS traffic for anomalies.
Social Media Platforms and Pharming Threats
Pharming attacks on social media platforms manipulate DNS entries to redirect users from legitimate websites to fraudulent ones, aiming to steal login credentials and personal information. Cybercriminals exploit popular social media sites like Facebook and Instagram to spread malicious links that lead to fake login pages indistinguishable from authentic ones. These threats highlight the critical need for robust DNS security measures and user awareness to prevent unauthorized access and data breaches.
Pharming via Malicious Browser Extensions
Pharming in website security often occurs through malicious browser extensions that redirect users to fraudulent websites without their knowledge. These extensions manipulate DNS settings or inject malicious scripts, compromising sensitive data and credentials. Users should regularly audit browser extensions and install only those from trusted sources to mitigate pharming risks.
Case Study: Corporate Website Compromise through Pharming
A major pharmaceutical company experienced a corporate website compromise through pharming when attackers redirected legitimate domain traffic to a malicious server, capturing sensitive employee login credentials. The incident highlighted vulnerabilities in DNS infrastructure and exposed the need for robust DNSSEC implementation to prevent unauthorized DNS cache poisoning. Post-attack analysis revealed that timely monitoring and incident response protocols significantly reduced data exfiltration during the breach.
Impact of Pharming on User Trust and Data Security
Pharming attacks redirect users from legitimate websites to fraudulent ones, compromising sensitive data such as login credentials and financial information. This breach significantly erodes user trust, as victims may unknowingly disclose private information, leading to identity theft and financial loss. The resulting damage to brand reputation and user confidence can cause long-term harm to organizations, making robust anti-pharming measures essential for website security.
Prevention Strategies Against Pharming in Web Security
Implementing DNS Security Extensions (DNSSEC) effectively prevents pharming attacks by authenticating DNS responses and ensuring users reach legitimate websites. Regularly updating and patching web server software mitigates vulnerabilities exploited by attackers to redirect traffic. Employing multi-factor authentication (MFA) and continuous monitoring of DNS traffic patterns enhances detection and response to pharming attempts in enterprise environments.
example of pharming in website security Infographic
 samplerz.com
samplerz.com