Escrow in key management involves securely storing cryptographic keys with a trusted third party to prevent data loss or unauthorized access. This method ensures that encrypted data can be recovered if the primary key holder becomes unavailable or loses their key. Organizations use key escrow to maintain access continuity while upholding security protocols. A common example of escrow in key management is in enterprise environments where encryption keys are stored with a key escrow service. These services enable system administrators to retrieve keys during critical incidents, such as data recovery or legal compliance checks. Key escrow balances the need for strong encryption with practical access requirements in secure data management.
Table of Comparison
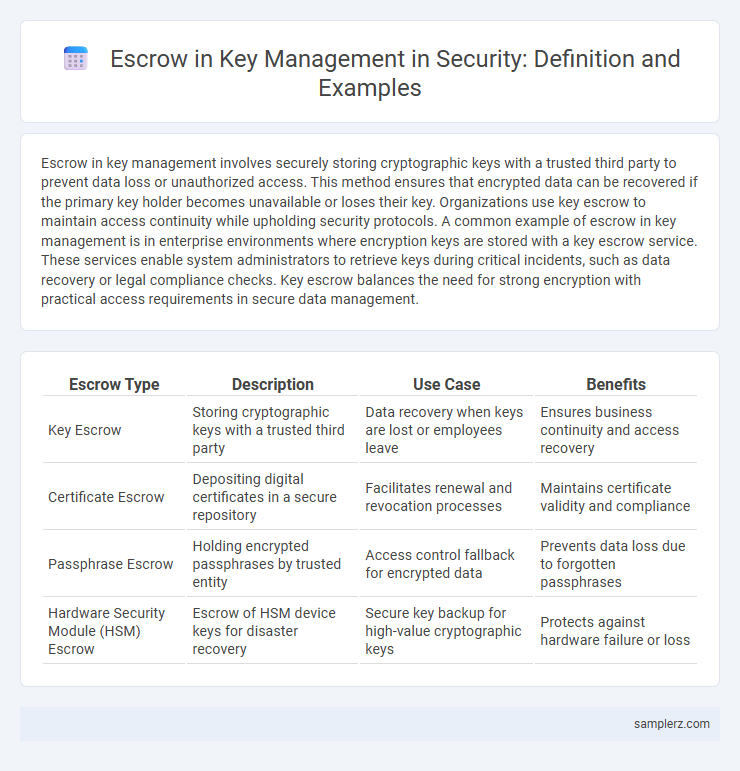
| Escrow Type | Description | Use Case | Benefits |
|---|---|---|---|
| Key Escrow | Storing cryptographic keys with a trusted third party | Data recovery when keys are lost or employees leave | Ensures business continuity and access recovery |
| Certificate Escrow | Depositing digital certificates in a secure repository | Facilitates renewal and revocation processes | Maintains certificate validity and compliance |
| Passphrase Escrow | Holding encrypted passphrases by trusted entity | Access control fallback for encrypted data | Prevents data loss due to forgotten passphrases |
| Hardware Security Module (HSM) Escrow | Escrow of HSM device keys for disaster recovery | Secure key backup for high-value cryptographic keys | Protects against hardware failure or loss |
Introduction to Escrow in Key Management
Escrow in key management involves securely storing cryptographic keys with a trusted third party to ensure access recovery when necessary. This practice is essential for organizations requiring robust data protection, enabling authorized retrieval of keys during emergencies or legal requirements. Implementing key escrow balances security with accessibility, mitigating risks of permanent data loss while maintaining strict control over access permissions.
The Role of Escrow in Cryptographic Security
Escrow in key management involves securely storing cryptographic keys with a trusted third party to ensure data recovery and continuity in case of key loss or compromise. This process enhances cryptographic security by providing a controlled mechanism for key retrieval, reducing the risk of permanent data inaccessibility. Organizations implement escrow protocols to balance security with operational resilience, enabling secure access while mitigating unauthorized key disclosure.
How Escrow Works in Key Custody
In key custody, escrow involves securely storing encryption keys with a trusted third party to ensure authorized access during recovery situations. The escrow agent maintains encrypted copies of the keys, releasing them only when predefined conditions, such as legal authorization or key loss, are met. This process enhances security by balancing key availability with strict access controls and audit mechanisms.
Real-World Examples of Key Escrow Implementations
Key escrow is implemented in secure corporate environments where encryption keys are stored with a trusted third party, allowing authorized recovery in case of loss or employee turnover. Governments also utilize key escrow systems to maintain lawful access to encrypted communications for national security purposes, exemplified by initiatives like the US government's Clipper Chip project. Financial institutions rely on escrowed keys to ensure data integrity and compliance, enabling swift access during audits or investigations while maintaining robust encryption standards.
Legal and Compliance Scenarios Involving Key Escrow
Key escrow in security plays a crucial role in legal and compliance scenarios where organizations must provide access to encrypted data under regulatory mandates or court orders. In regulated industries like finance and healthcare, escrowed cryptographic keys enable authorized parties to decrypt sensitive information while ensuring adherence to data privacy laws such as GDPR or HIPAA. Proper implementation of key escrow mechanisms helps maintain audit trails and enforces strict access controls, mitigating risks of unauthorized data exposure during compliance reviews.
Escrow in Enterprise Encryption Management
Escrow in enterprise encryption management involves securely storing encryption keys with a trusted third party to ensure data recoverability and compliance with regulatory requirements. This practice mitigates the risk of data loss due to key mismanagement or employee turnover while maintaining strict access controls and audit trails. Organizations implement key escrow to balance data protection with operational continuity, particularly in cloud and hybrid IT environments.
Government Use Cases for Key Escrow
Government agencies implement key escrow systems to securely manage cryptographic keys used in classified communications and sensitive data encryption. These escrow mechanisms enable authorized law enforcement and intelligence personnel to access encrypted information during investigations or national security operations, ensuring compliance with legal protocols. Deploying key escrow in government environments enhances oversight while maintaining robust protection against unauthorized access.
Mitigating Insider Threats through Escrow Solutions
Escrow solutions in key management enable secure storage of cryptographic keys with controlled access, significantly mitigating insider threats by preventing unauthorized key usage or data manipulation. By implementing multi-party escrow protocols and strict access controls, organizations ensure that critical keys are released only under predefined conditions, reducing risks of malicious insiders exploiting key access. This layered security approach enhances accountability and trust while maintaining business continuity in sensitive environments.
Challenges and Risks in Key Escrow Systems
Key escrow systems in cryptographic key management face significant challenges such as safeguarding against unauthorized access to escrowed keys, which can lead to potential data breaches and insider threats. The risk of single points of failure arises when escrow agents are compromised, posing threats to the confidentiality and integrity of encrypted communications. Ensuring strong access controls, secure key storage, and regular audits is critical to mitigate risks associated with key escrow vulnerabilities.
Best Practices for Secure Key Escrow Management
Implement secure key escrow management by using hardware security modules (HSMs) to store encryption keys, ensuring physical and logical access controls are strictly enforced. Employ multi-factor authentication and role-based access policies to limit key retrieval and avoid unauthorized access. Regularly audit and monitor escrow activities to detect anomalies and maintain compliance with cybersecurity standards such as NIST SP 800-57.
example of escrow in key management Infographic
 samplerz.com
samplerz.com