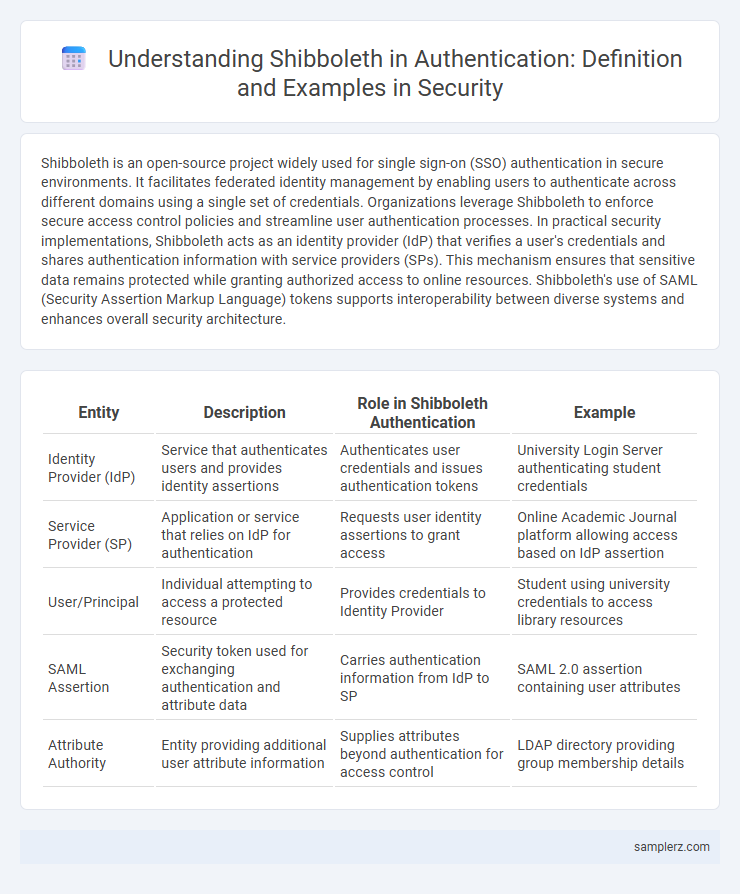
Shibboleth is an open-source project widely used for single sign-on (SSO) authentication in secure environments. It facilitates federated identity management by enabling users to authenticate across different domains using a single set of credentials. Organizations leverage Shibboleth to enforce secure access control policies and streamline user authentication processes. In practical security implementations, Shibboleth acts as an identity provider (IdP) that verifies a user's credentials and shares authentication information with service providers (SPs). This mechanism ensures that sensitive data remains protected while granting authorized access to online resources. Shibboleth's use of SAML (Security Assertion Markup Language) tokens supports interoperability between diverse systems and enhances overall security architecture.
Table of Comparison
| Entity | Description | Role in Shibboleth Authentication | Example |
|---|---|---|---|
| Identity Provider (IdP) | Service that authenticates users and provides identity assertions | Authenticates user credentials and issues authentication tokens | University Login Server authenticating student credentials |
| Service Provider (SP) | Application or service that relies on IdP for authentication | Requests user identity assertions to grant access | Online Academic Journal platform allowing access based on IdP assertion |
| User/Principal | Individual attempting to access a protected resource | Provides credentials to Identity Provider | Student using university credentials to access library resources |
| SAML Assertion | Security token used for exchanging authentication and attribute data | Carries authentication information from IdP to SP | SAML 2.0 assertion containing user attributes |
| Attribute Authority | Entity providing additional user attribute information | Supplies attributes beyond authentication for access control | LDAP directory providing group membership details |
Understanding Shibboleth: Modern Authentication Explained
Shibboleth is an open-source single sign-on (SSO) system widely used in academic and enterprise environments for federated identity management. It enables users to authenticate across multiple systems using a single set of credentials, leveraging SAML (Security Assertion Markup Language) to securely exchange authentication and authorization data. By supporting seamless access control and privacy protection, Shibboleth enhances security and user experience in distributed network environments.
Key Features of Shibboleth in Security Protocols
Shibboleth employs federated identity solutions that enable single sign-on (SSO) across multiple organizations while preserving user privacy through attribute-based access control. Its key features include robust authentication mechanisms such as SAML 2.0 support, secure user attribute release, and strong encryption protocols that protect data in transit. The system's decentralized approach to identity management enhances security by reducing centralized vulnerabilities and improving compliance with data protection regulations.
Real-World Applications of Shibboleth Authentication
Shibboleth authentication is widely implemented in academic institutions for secure access to digital libraries and research databases, enabling single sign-on (SSO) across multiple services while maintaining user privacy. Many government agencies leverage Shibboleth to provide federated identity management, allowing employees to access internal applications seamlessly without repeated logins. Enterprises use Shibboleth to integrate with cloud-based services and partner organizations, enhancing cross-domain authentication and minimizing password-related security risks.
Integrating Shibboleth with Single Sign-On Systems
Integrating Shibboleth with Single Sign-On (SSO) systems enhances security by enabling seamless, federated authentication across multiple platforms while maintaining user privacy through attribute-based access control. Shibboleth supports SAML-based SSO, allowing organizations to leverage existing identity providers for unified credential management and streamlined user experience. Enterprises benefit from reduced password fatigue and centralized authentication policies, significantly lowering the risk of unauthorized access.
Step-by-Step Example: Shibboleth Authentication Workflow
Shibboleth authentication workflow begins when a user attempts to access a protected resource, triggering a redirect to the Shibboleth Identity Provider (IdP) for login. The IdP authenticates the user through credentials verification and generates a SAML assertion containing user attributes. This assertion is then sent back to the Service Provider (SP), which validates the assertion and grants access based on the user's authenticated identity and attribute-based access control policies.
Advantages of Using Shibboleth for Identity Management
Shibboleth enhances security by enabling seamless single sign-on (SSO) across multiple organizations, reducing the risk of password fatigue and credential reuse. It supports federated identity management through standards like SAML, ensuring secure and privacy-preserving authentication. The system also offers fine-grained access control, improving compliance with data protection regulations and minimizing unauthorized access.
Shibboleth vs. Traditional Authentication Methods
Shibboleth provides a federated identity solution enabling single sign-on (SSO) across multiple domains, enhancing user convenience and reducing password fatigue compared to traditional authentication methods that rely on standalone credentials. Unlike conventional username-password systems vulnerable to brute force attacks, Shibboleth leverages Security Assertion Markup Language (SAML) for secure, token-based authentication, ensuring improved privacy and reduced risk of credential theft. Enterprises adopting Shibboleth benefit from centralized identity management and seamless access control, contrasting with the fragmented and admin-intensive management of traditional authentication infrastructures.
Common Use Cases: Shibboleth in Higher Education
Shibboleth is widely implemented in higher education institutions to provide secure, single sign-on (SSO) access to multiple campus resources such as library databases, learning management systems, and research portals. It allows universities to maintain control over user identities while enabling seamless authentication across federated networks, ensuring compliance with privacy regulations like FERPA and GDPR. Common use cases include facilitating collaboration between institutions through federated identity management and granting students and faculty cross-institutional access to academic content without repeated logins.
Security Risks and Mitigations in Shibboleth Authentication
Shibboleth authentication faces security risks such as identity spoofing, session hijacking, and metadata tampering, which can undermine user credibility and data protection. Implementing strong encryption protocols like TLS, rigorous metadata validation, and multi-factor authentication mitigates these risks effectively. Continuous monitoring and timely patching of vulnerabilities further enhance the security posture of Shibboleth deployments.
Future Trends: Evolving Shibboleth in Digital Security
Shibboleth continues to evolve by integrating advanced identity federation protocols and embracing decentralized authentication models to enhance security in digital ecosystems. Future trends emphasize leveraging blockchain technology and AI-driven risk analysis to improve user verification and reduce unauthorized access. This evolution positions Shibboleth as a resilient framework supporting adaptive, scalable authentication in increasingly complex cyber environments.
example of shibboleth in authentication Infographic
 samplerz.com
samplerz.com