In digital forensics, a common example of a rabbit hole is the extensive analysis of log files that ultimately reveal irrelevant or misleading information. Investigators may spend significant time tracing IP addresses or user activities that lead to dead ends due to spoofed credentials or corrupted data. This diversion consumes valuable resources and delays the extraction of meaningful evidence from primary data sources. Another rabbit hole involves over-analyzing encrypted files without proper decryption keys, resulting in wasted efforts with no actionable insights. Forensic experts might focus heavily on metadata anomalies that turn out to be benign or unrelated to the security incident. Recognizing these rabbit holes early helps prioritize critical data, streamline investigations, and improve the overall efficiency of security responses.
Table of Comparison
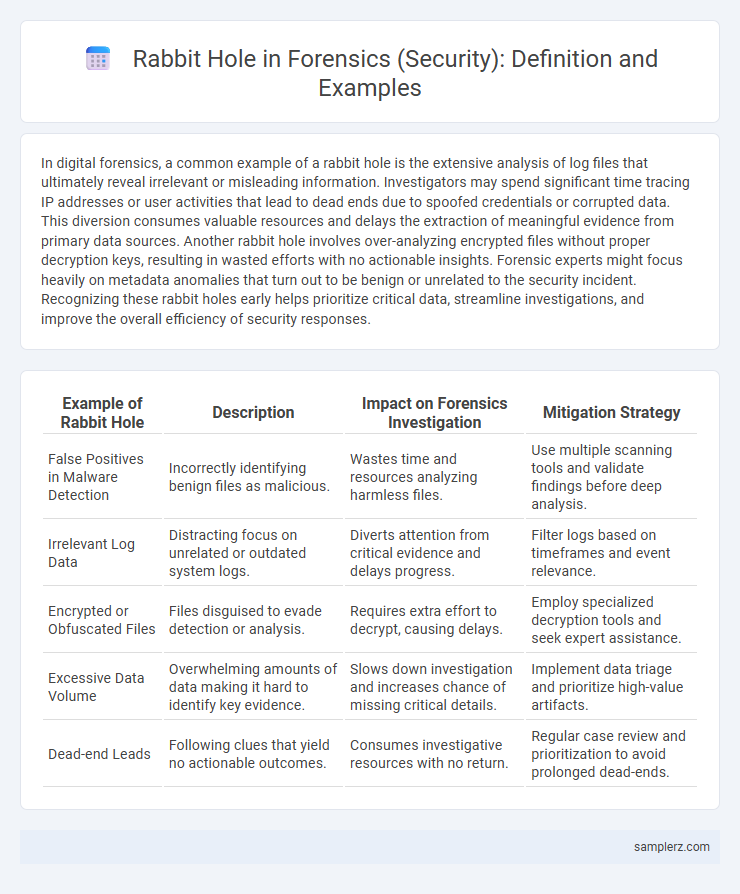
| Example of Rabbit Hole | Description | Impact on Forensics Investigation | Mitigation Strategy |
|---|---|---|---|
| False Positives in Malware Detection | Incorrectly identifying benign files as malicious. | Wastes time and resources analyzing harmless files. | Use multiple scanning tools and validate findings before deep analysis. |
| Irrelevant Log Data | Distracting focus on unrelated or outdated system logs. | Diverts attention from critical evidence and delays progress. | Filter logs based on timeframes and event relevance. |
| Encrypted or Obfuscated Files | Files disguised to evade detection or analysis. | Requires extra effort to decrypt, causing delays. | Employ specialized decryption tools and seek expert assistance. |
| Excessive Data Volume | Overwhelming amounts of data making it hard to identify key evidence. | Slows down investigation and increases chance of missing critical details. | Implement data triage and prioritize high-value artifacts. |
| Dead-end Leads | Following clues that yield no actionable outcomes. | Consumes investigative resources with no return. | Regular case review and prioritization to avoid prolonged dead-ends. |
Introduction to Rabbit Holes in Digital Forensics
Digital forensics investigators often encounter rabbit holes, which are misleading or irrelevant paths that consume significant time and resources without yielding valuable evidence. These traps commonly arise from volatile data misinterpretation, deceptive file artifacts, or intricate encryption schemes designed to obfuscate true activity. Identifying and avoiding rabbit holes is critical for maintaining investigation efficiency and ensuring accurate attribution in cybersecurity cases.
Common Triggers of Investigative Rabbit Holes
Common triggers of investigative rabbit holes in forensics include ambiguous evidence, conflicting witness statements, and overly broad search parameters. Forensic teams may also get sidetracked by false positives in data analysis tools or unverified digital artifacts. These factors divert resources and delay accurate conclusions in cybersecurity incident response.
Case Study: Misleading Artifacts and Their Impact
Misleading artifacts in forensic investigations often create rabbit holes that divert efforts from uncovering the true source of a security breach. In one case study, investigators were misled by fabricated logs designed to implicate an innocent insider, causing a significant delay in identifying the actual attacker. These deceptive artifacts not only waste crucial time but also risk compromising the integrity of the entire incident response process.
Time Sink: How Irrelevant Evidence Distracts Analysts
Examining irrelevant evidence in digital forensics creates significant time sinks that hinder effective incident response. Analysts may become trapped following inconsequential leads, delaying critical threat identification and remediation. Prioritizing high-value data sources and leveraging automated triage tools mitigates these distractors and accelerates forensic investigations.
Social Engineering: Forensic Investigators as Targets
Social engineering attacks in forensics often involve deceptive tactics to manipulate forensic investigators into revealing sensitive information or altering evidence. Attackers exploit human vulnerabilities through phishing, pretexting, or impersonation to gain unauthorized access to forensic tools and data. This rabbit hole can lead to compromised investigations, data breaches, and the corruption of digital evidence integrity.
False Positives: Red Herrings in Log Analysis
False positives in log analysis represent a common rabbit hole in security forensics, often leading investigators to chase misleading data that appears suspicious but is benign. These red herrings consume valuable time and resources by diverting attention from genuine threats, complicating incident response efforts. Effective use of anomaly detection algorithms and correlation with threat intelligence can minimize false positives and enhance the accuracy of forensic investigations.
Rabbit Holes in Malware Analysis
Rabbit holes in malware analysis occur when investigators follow irrelevant or misleading code paths that consume valuable time without yielding actionable insights. Complex obfuscation techniques and decoy code fragments often divert analysts away from the core malicious functionality. Detecting and avoiding these rabbit holes requires expertise in code behavior patterns and malware family characteristics.
Confirming or Disproving Investigative Assumptions
Investigators often encounter rabbit holes when initial assumptions lead them down irrelevant paths, wasting valuable time and resources. Confirming or disproving these assumptions through rigorous evidence analysis and cross-validation is critical for maintaining the integrity of forensic investigations. Leveraging automated tools and comprehensive data correlation helps prevent fixation on false leads and ensures a more accurate and efficient resolution.
Best Practices to Avoid Forensic Rabbit Holes
Thorough documentation and maintaining clear chain-of-custody protocols prevent forensic investigators from pursuing misleading evidence that leads to rabbit holes. Utilizing validated tools and standardized procedures minimizes the risk of misinterpretation and ensures accurate data analysis. Regular training on recognizing and avoiding common distractions in forensic data preserves investigative focus and integrity.
Lessons Learned: Improving Forensic Methodologies
In forensic investigations, a common rabbit hole involves over-reliance on unverified digital evidence that leads to misinterpretation of the attack timeline. Lessons learned emphasize the integration of cross-validation techniques, such as correlating network logs with endpoint data, to enhance accuracy and avoid misleading conclusions. Developing standardized workflows that prioritize evidence integrity and chain-of-custody protocols significantly improves forensic methodologies and case outcomes.
example of rabbit hole in forensics Infographic
 samplerz.com
samplerz.com