Fuzzing is a critical technique in vulnerability assessment used to identify security flaws by inputting large volumes of random or malformed data into software applications. This process helps entities detect buffer overflows, memory leaks, and input validation errors that could be exploited by attackers. Leading security firms integrate fuzzing within their vulnerability assessment workflows to ensure comprehensive identification of potential exploit vectors. Automated fuzzing tools generate diverse test cases, enabling data-driven analysis of application resilience under unexpected input conditions. Security teams utilize the results to prioritize patches based on the severity and reproducibility of discovered vulnerabilities. The continuous application of fuzzing enhances the overall security posture by systematically uncovering hidden bugs before they reach production environments.
Table of Comparison
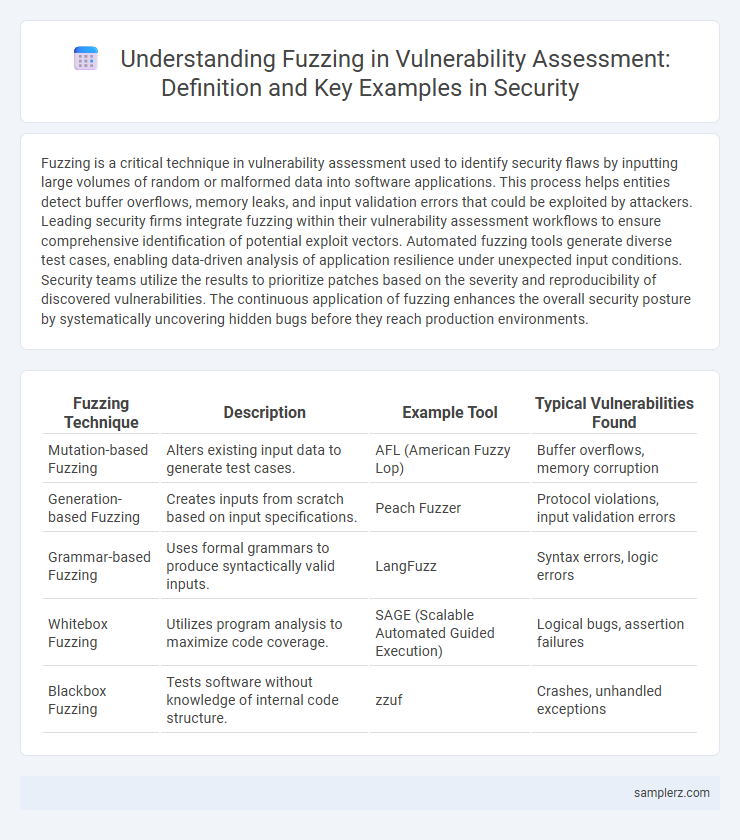
| Fuzzing Technique | Description | Example Tool | Typical Vulnerabilities Found |
|---|---|---|---|
| Mutation-based Fuzzing | Alters existing input data to generate test cases. | AFL (American Fuzzy Lop) | Buffer overflows, memory corruption |
| Generation-based Fuzzing | Creates inputs from scratch based on input specifications. | Peach Fuzzer | Protocol violations, input validation errors |
| Grammar-based Fuzzing | Uses formal grammars to produce syntactically valid inputs. | LangFuzz | Syntax errors, logic errors |
| Whitebox Fuzzing | Utilizes program analysis to maximize code coverage. | SAGE (Scalable Automated Guided Execution) | Logical bugs, assertion failures |
| Blackbox Fuzzing | Tests software without knowledge of internal code structure. | zzuf | Crashes, unhandled exceptions |
Introduction to Fuzzing in Vulnerability Assessment
Fuzzing is a dynamic software testing technique used in vulnerability assessment to identify security weaknesses by inputting large volumes of random or malformed data into a program. This method helps detect memory leaks, crashes, and unexpected behavior, which are often indicators of security vulnerabilities. Popular fuzzing tools like AFL (American Fuzzy Lop) and libFuzzer automate this process, improving the accuracy and efficiency of identifying exploitable flaws in complex software systems.
Key Concepts of Fuzz Testing
Fuzz testing, or fuzzing, is a security assessment technique that involves injecting malformed or random data into software inputs to identify vulnerabilities. Key concepts include mutation-based fuzzing, which modifies existing data samples, and generation-based fuzzing, which creates inputs based on predefined specifications or protocols. Monitoring application responses, such as crashes, memory leaks, or assertion failures, enables detection of security weaknesses exploited by malformed inputs.
Common Types of Fuzzers Used in Security
Common types of fuzzers used in security vulnerability assessment include mutation-based, generation-based, and coverage-guided fuzzers, each targeting different input variations to discover software flaws. Mutation-based fuzzers modify existing valid inputs to identify unexpected behavior, while generation-based fuzzers create inputs from scratch based on specified formats or protocols. Coverage-guided fuzzers leverage runtime feedback to explore deeper code paths, enhancing their ability to detect complex vulnerabilities in applications.
Step-by-Step Fuzzing Workflow Example
A step-by-step fuzzing workflow example begins with target identification, where the specific software or protocol to be tested is selected. Next, test case generation creates a wide range of malformed or unexpected inputs to probe potential vulnerabilities. Finally, monitoring and analysis capture program crashes or unexpected behaviors, enabling identification and remediation of security flaws.
Case Study: Fuzzing Web Applications for Vulnerabilities
Fuzzing web applications involves sending a wide range of malformed or unexpected inputs to identify security vulnerabilities such as SQL injection, cross-site scripting (XSS), and buffer overflow errors. A notable case study demonstrated how automated fuzzing tools uncovered zero-day vulnerabilities in a major e-commerce platform's input validation process, leading to the patching of critical security flaws before public exploitation. This approach enhances vulnerability assessment by systematically exploring application behavior under abnormal conditions, thereby strengthening web application security posture.
Example: Identifying Buffer Overflows Through Fuzzing
Fuzzing identifies buffer overflows by sending a wide range of malformed or unexpected inputs to a program, causing it to crash or behave unexpectedly. This process helps reveal memory corruption issues where input exceeds buffer limits, leading to potential exploitation. Tools like American Fuzzy Lop (AFL) automate fuzz testing to uncover such critical vulnerabilities efficiently.
Real-World Example: Fuzzing Network Protocols
Fuzzing network protocols involves sending malformed or unexpected data packets to network services to identify security vulnerabilities such as buffer overflows and memory leaks. A notable real-world example is the discovery of critical vulnerabilities in the OpenSSL Heartbleed bug through protocol fuzzing techniques. This approach enabled security researchers to uncover flaws in the TLS heartbeat extension, highlighting the effectiveness of automated fuzz testing in securing communication protocols.
Tools for Automated Vulnerability Fuzzing
Automated vulnerability fuzzing tools like AFL (American Fuzzy Lop), LibFuzzer, and Peach Fuzzer accelerate security testing by generating malformed inputs to detect software bugs and vulnerabilities. These tools leverage mutation-based and generation-based techniques to simulate a wide range of attack vectors, improving coverage and detection rates. Integrating fuzzers into continuous security assessments enables early identification of memory corruption, input validation errors, and logic flaws critical for safeguarding applications.
Challenges and Limitations of Fuzz Testing
Fuzz testing faces challenges such as high false positive rates and difficulty in generating inputs that effectively explore complex code paths, leading to incomplete vulnerability coverage. Limitations include the inability to detect logical flaws or vulnerabilities triggered by specific environmental conditions, reducing its effectiveness in comprehensive security assessments. Resource-intensive processing and the need for expert interpretation of results further complicate the fuzzing process.
Best Practices for Effective Fuzzing in Security Assessment
Leveraging structured input mutation and coverage-guided fuzzing techniques enhances vulnerability discovery by systematically exploring application code paths. Integrating continuous monitoring and detailed logging during fuzzing sessions allows prompt identification and analysis of crashes or anomalies. Employing diverse fuzzing tools tailored to specific protocols or file formats maximizes input variability, increasing the likelihood of uncovering hidden security flaws.
example of fuzzing in vulnerability assessment Infographic
 samplerz.com
samplerz.com