A honeytoken in a database is a deliberately placed piece of false data used to detect unauthorized access or data breaches. Common examples include fake user accounts, fabricated credit card numbers, or bogus email addresses embedded within sensitive tables. These deceptive entries trigger alerts when queried or accessed, providing early warning of potential security threats. Database honeytokens can be tailored to mimic real data, making them difficult for attackers to distinguish from genuine information. Organizations deploy honeytokens to monitor insider threats, detect SQL injection attempts, or identify compromised credentials. Tracking access patterns and alerting upon interaction with these tokens enhances overall data security and incident response capabilities.
Table of Comparison
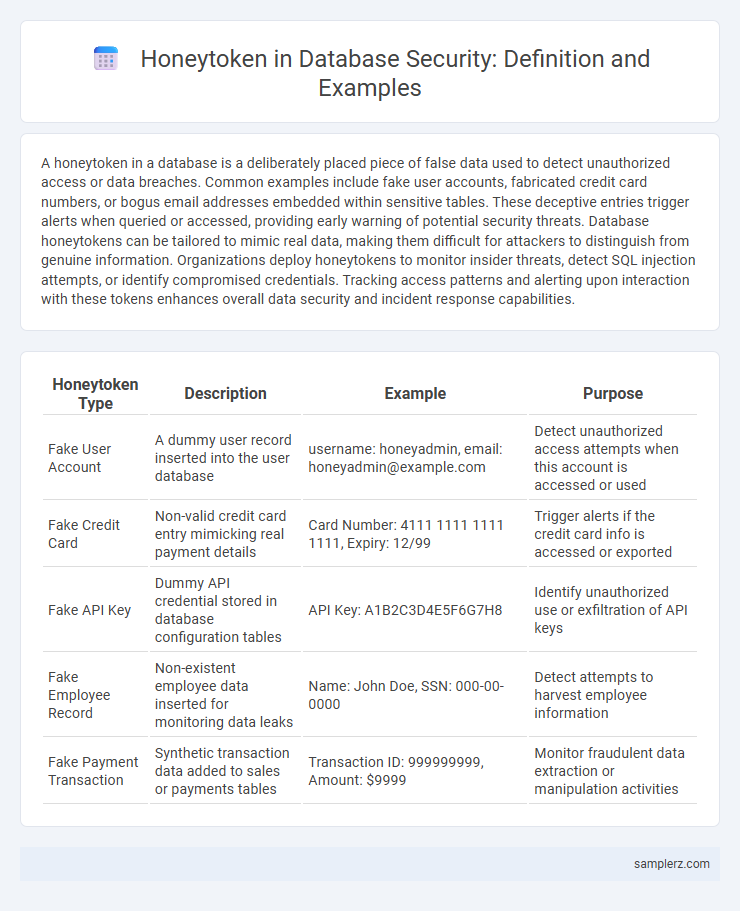
| Honeytoken Type | Description | Example | Purpose |
|---|---|---|---|
| Fake User Account | A dummy user record inserted into the user database | username: honeyadmin, email: honeyadmin@example.com | Detect unauthorized access attempts when this account is accessed or used |
| Fake Credit Card | Non-valid credit card entry mimicking real payment details | Card Number: 4111 1111 1111 1111, Expiry: 12/99 | Trigger alerts if the credit card info is accessed or exported |
| Fake API Key | Dummy API credential stored in database configuration tables | API Key: A1B2C3D4E5F6G7H8 | Identify unauthorized use or exfiltration of API keys |
| Fake Employee Record | Non-existent employee data inserted for monitoring data leaks | Name: John Doe, SSN: 000-00-0000 | Detect attempts to harvest employee information |
| Fake Payment Transaction | Synthetic transaction data added to sales or payments tables | Transaction ID: 999999999, Amount: $9999 | Monitor fraudulent data extraction or manipulation activities |
Introduction to Honeytokens in Database Security
Honeytokens in database security are deceptive data elements planted to detect unauthorized access and malicious activities. Examples include fake user credentials, bogus database records, or fabricated transaction logs that trigger alerts when accessed. These honeytokens serve as an early warning system, enabling rapid identification of breaches and insider threats within database environments.
Common Types of Database Honeytokens
Common types of database honeytokens include fake user credentials, bogus database entries, and phantom API keys designed to detect unauthorized access. These honeytokens serve as decoys, triggering alerts when accessed or manipulated, thus providing early warning of data breaches. Implementing strategically placed honeytokens enhances intrusion detection by confusing attackers and safeguarding sensitive information.
How Honeytokens Detect Unauthorized Database Access
Honeytokens embedded in a database act as deceptive markers, such as fake user records or bogus credit card entries, that trigger alerts when accessed or queried. These markers are invisible to legitimate users but highly attractive to attackers attempting to exfiltrate data, enabling rapid identification of unauthorized access patterns. By monitoring interactions with honeytokens, security teams gain early warning signs of breaches and can respond proactively to contain potential threats.
Example: Fake User Credentials as Honeytokens
Fake user credentials serve as effective honeytokens within databases by mimicking legitimate login information to lure unauthorized access attempts. These decoy credentials trigger alerts when accessed, enabling early detection of malicious insiders or external attackers targeting the database. Implementing such false user records enhances database security by providing actionable intelligence on unauthorized access patterns without compromising real user data.
Example: Decoy Financial Records in Databases
Decoy financial records in databases serve as honeytokens by mimicking legitimate transaction entries with subtle, traceable anomalies designed to flag unauthorized access. These records, embedded within critical financial tables, contain fictitious account numbers and transaction amounts that trigger alerts when queried or manipulated. Implementing such deceptive data strengthens intrusion detection by providing early warnings of database breaches without impacting real operational data.
Example: Nonexistent Table Entries as Traps
Nonexistent table entries serve as effective honeytokens in database security by acting as traps for unauthorized users attempting to access or extract data. These fictitious records are designed to trigger alerts when queried, signaling potential breaches or insider threats within the system. Implementing such deceptive entries enhances threat detection by providing early indicators of malicious activities targeting the database environment.
Example: Honeytoken API Keys in Config Tables
Honeytoken API keys embedded within configuration tables serve as deceptive credentials, triggering alerts when accessed by unauthorized actors. These fake keys mimic legitimate API credentials, allowing security teams to detect and respond to potential data breaches or insider threats early. Deploying such honeytokens enhances intrusion detection by leveraging database monitoring systems that flag unusual usage patterns linked to these planted keys.
Logging and Monitoring Honeytoken Access Events
Implementing honeytokens in databases involves embedding decoy data such as bogus user credentials or fake records that trigger alerts upon access. Logging every interaction with these honeytokens provides detailed audit trails, capturing timestamps, IP addresses, and query types, essential for forensic analysis. Continuous monitoring of honeytoken access events enables early detection of unauthorized activities and potential insider threats, strengthening database security posture.
Best Practices for Implementing Database Honeytokens
Database honeytokens should be strategically embedded within sensitive tables, such as user credentials or financial records, using realistic but fictitious data to avoid detection. Best practices recommend regular monitoring of honeytoken access patterns through alerting systems to promptly identify unauthorized or suspicious activity. Encrypting honeytokens and isolating them in decoy schemas enhances their effectiveness while minimizing risks to genuine data integrity and system performance.
Challenges and Limitations of Honeytokens in Databases
Honeytokens in databases, such as fake credentials or decoy rows, face challenges including the risk of false positives that can overwhelm security teams when legitimate users inadvertently trigger alerts. Limitations also arise from attackers identifying honeytokens through pattern analysis or irregular data entries, reducing their effectiveness as detection tools. Furthermore, maintaining and updating honeytokens requires continuous effort to ensure they remain indistinguishable from real data without compromising database performance.
example of honeytoken in database Infographic
 samplerz.com
samplerz.com