Shimming in card security involves inserting a thin device, known as a shim, into the card reader slot to capture data from the magnetic stripe or chip of a payment card. This technique exploits vulnerabilities in card readers, especially ATM and point-of-sale terminals, by intercepting data during the transaction process without the cardholder's knowledge. Data collected through shimming includes payment card numbers, expiration dates, and sometimes sensitive personal identification numbers (PINs). Security professionals focus on detecting shimming attacks by monitoring unusual activity on card readers and employing advanced encryption protocols. The implementation of EMV chip technology reduces the risk of shimming as it generates unique transaction codes for each use, making stolen data less useful. Financial institutions and merchants invest in software updates and hardware improvements to limit data breaches caused by shimming devices and protect consumer payment information.
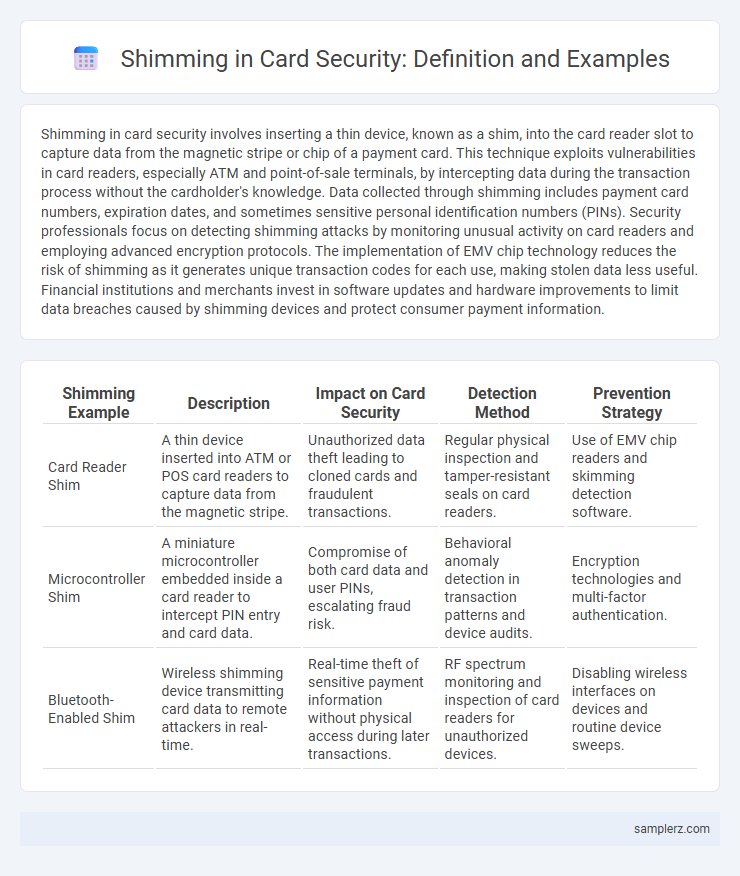
Table of Comparison
| Shimming Example | Description | Impact on Card Security | Detection Method | Prevention Strategy |
|---|---|---|---|---|
| Card Reader Shim | A thin device inserted into ATM or POS card readers to capture data from the magnetic stripe. | Unauthorized data theft leading to cloned cards and fraudulent transactions. | Regular physical inspection and tamper-resistant seals on card readers. | Use of EMV chip readers and skimming detection software. |
| Microcontroller Shim | A miniature microcontroller embedded inside a card reader to intercept PIN entry and card data. | Compromise of both card data and user PINs, escalating fraud risk. | Behavioral anomaly detection in transaction patterns and device audits. | Encryption technologies and multi-factor authentication. |
| Bluetooth-Enabled Shim | Wireless shimming device transmitting card data to remote attackers in real-time. | Real-time theft of sensitive payment information without physical access during later transactions. | RF spectrum monitoring and inspection of card readers for unauthorized devices. | Disabling wireless interfaces on devices and routine device sweeps. |
Introduction to Shimming in Card Security
Shimming in card security involves inserting a thin device, called a shim, into the card reader's chip slot to intercept and manipulate payment data during transactions. Unlike traditional skimming, shimming specifically targets EMV chip cards by capturing sensitive information such as the card's PIN and chip data in real-time. This technique poses significant risks to secure payment systems by bypassing chip security features and enabling unauthorized access to financial data.
How Card Shimming Attacks Work
Card shimming attacks exploit the interception of data between the card chip and the terminal by inserting a thin electronic device, or shim, into the card reader's slot. This device captures the card's EMV chip data, including sensitive information like the card number and PIN, without altering the physical card. The stolen data is then used to create cloned cards or commit unauthorized transactions, bypassing traditional magnetic stripe security measures.
Real-World Examples of Card Shimming Incidents
Card shimming involves inserting a thin, flexible device into an ATM or card reader to capture data from the chip card's magnetic stripe and EMV chip. In 2018, multiple incidents in Europe targeted ATMs where shimmers collected PIN codes and card details, leading to widespread fraud and unauthorized transactions. Major banks reported significant financial losses due to these shimming devices, emphasizing the need for enhanced anti-tampering technologies in card readers.
Common Devices Used in Card Shimming
Common devices used in card shimming include thin, flexible devices made to fit inside card readers such as ATMs and gas pumps, designed to capture data from RFID chips or magnetic stripes. These devices often resemble small circuit boards with microcontrollers and memory storage, capable of recording card information during normal transactions. Security measures focus on detecting irregularities in card reader mechanisms to prevent unauthorized data extraction through shimming.
Signs Your Card Reader Has Been Shimmed
Signs your card reader has been shimmed include unusual physical alterations such as thicker or loose card slots, misaligned components, or the presence of foreign objects inside the reader. Slow transaction processing and frequent declines despite correct card information can also indicate a compromised device. Monitoring for these signs is crucial in preventing data theft from skimming devices hidden within legitimate card readers.
Impact of Shimming on EMV Chip Cards
Shimming poses a significant security threat to EMV chip cards by inserting malicious devices between the card and the reader to capture sensitive data during transactions. Unlike traditional skimming, shimming can extract encrypted communication data from the chip, potentially enabling attackers to clone cards or conduct unauthorized transactions. Financial institutions face increased fraud risks and must implement advanced detection technologies and transaction monitoring to mitigate the impact of shimming on EMV card security.
Case Study: Shimming at ATMs and Gas Pumps
Shimming in card security involves inserting a thin device into ATM or gas pump card readers to capture data from the magnetic stripe without detection. A notable case study revealed that criminals installed shimming devices on ATMs and fuel stations, stealing card information and PINs to clone cards and conduct fraudulent transactions. Mitigating these attacks requires deploying EMV chip technology, upgrading card readers, and monitoring transaction anomalies to protect customer data effectively.
Preventive Measures Against Card Shimming
Preventive measures against card shimming include installing anti-skimming devices such as tamper-resistant ATM card readers and regularly inspecting card readers for unauthorized attachments. Employing EMV chip technology significantly reduces the risk by generating unique transaction codes that cannot be cloned. User vigilance, including covering keypads during PIN entry and reporting suspicious equipment, enhances overall protection against card shimming attacks.
Legal Consequences for Card Shimming Offenses
Card shimming involves inserting a thin device into a card reader to steal data from the magnetic stripe, leading to severe legal consequences under laws such as the Computer Fraud and Abuse Act (CFAA) in the United States. Perpetrators face charges ranging from identity theft and fraud to unauthorized access, with penalties including substantial fines and imprisonment. Law enforcement agencies increasingly prioritize card shimming cases to protect consumers and financial institutions from escalating cybercrimes.
Future Trends in Card Shimming and Countermeasures
Future trends in card shimming involve the integration of advanced machine learning algorithms to detect anomalous patterns and enhance real-time transaction monitoring. The development of next-generation EMV chip technologies and contactless payment systems aims to reduce physical access vulnerabilities exploited by shimming devices. Organizations are increasingly investing in multi-layered authentication protocols and advanced encryption to strengthen countermeasures against evolving card shimming attacks.
example of shimming in card security Infographic
 samplerz.com
samplerz.com