Badge cloning in access control occurs when an unauthorized individual copies the data from a legitimate access badge to create a duplicate. This duplicated badge grants the attacker the same access privileges as the original cardholder, compromising the security of restricted areas. Common methods for cloning include RFID skimming and magnetic stripe duplication, where information is intercepted using specialized devices. Organizations face significant risks from badge cloning, including unauthorized entry, data theft, and physical asset damage. Security systems often implement multi-factor authentication and encryption of badge data to mitigate cloning threats. Regular audits and the use of advanced badge technologies, like biometric integration, enhance protection against unauthorized access through cloned credentials.
Table of Comparison
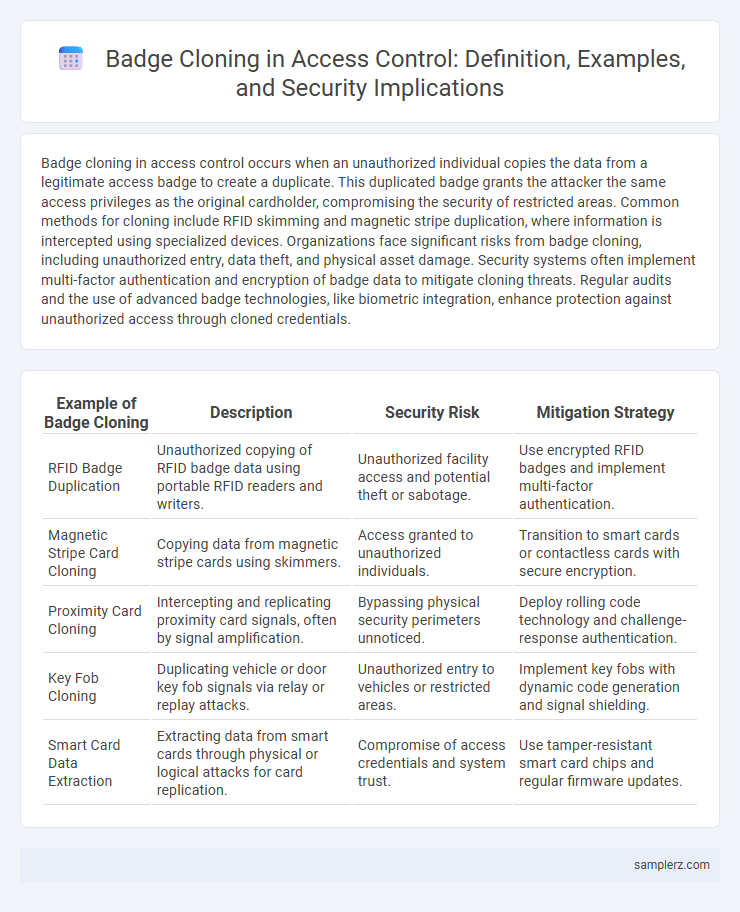
| Example of Badge Cloning | Description | Security Risk | Mitigation Strategy |
|---|---|---|---|
| RFID Badge Duplication | Unauthorized copying of RFID badge data using portable RFID readers and writers. | Unauthorized facility access and potential theft or sabotage. | Use encrypted RFID badges and implement multi-factor authentication. |
| Magnetic Stripe Card Cloning | Copying data from magnetic stripe cards using skimmers. | Access granted to unauthorized individuals. | Transition to smart cards or contactless cards with secure encryption. |
| Proximity Card Cloning | Intercepting and replicating proximity card signals, often by signal amplification. | Bypassing physical security perimeters unnoticed. | Deploy rolling code technology and challenge-response authentication. |
| Key Fob Cloning | Duplicating vehicle or door key fob signals via relay or replay attacks. | Unauthorized entry to vehicles or restricted areas. | Implement key fobs with dynamic code generation and signal shielding. |
| Smart Card Data Extraction | Extracting data from smart cards through physical or logical attacks for card replication. | Compromise of access credentials and system trust. | Use tamper-resistant smart card chips and regular firmware updates. |
Understanding Badge Cloning in Access Control
Badge cloning in access control occurs when an unauthorized individual copies the electronic or RFID data from a legitimate access badge, allowing them to bypass security measures and gain entry. This technique exploits vulnerabilities in proximity card systems by mimicking the signal of an authorized badge, posing significant risks to physical security. Implementing multi-factor authentication and encrypted communication protocols can mitigate the threat of badge cloning in secure facilities.
Real-World Badge Cloning Incidents
Real-world badge cloning incidents reveal significant vulnerabilities in access control systems, such as the 2019 case at a major financial institution where attackers duplicated RFID badges to infiltrate secured server rooms undetected. These breaches often exploit weak encryption protocols in low-frequency badges, enabling unauthorized personnel to gain physical access to restricted areas. Addressing such incidents requires upgrading to encrypted smart cards with multifactor authentication to mitigate the risk of cloning attacks.
Common Techniques Used for Badge Cloning
Common techniques used for badge cloning in access control include RFID skimming, where attackers use RFID readers to capture data from proximity cards without physical contact. Another method involves the use of magnetic stripe duplicators to copy information from traditional badges onto counterfeit cards. Additionally, hackers may exploit vulnerabilities in poorly encrypted card data to recreate digital credentials, enabling unauthorized access to secure facilities.
Case Study: Badge Cloning in Corporate Environments
Badge cloning in corporate environments has led to significant security breaches by allowing unauthorized individuals to gain access to restricted areas. In a notable case study, cloned RFID badges were used to bypass multi-factor authentication systems, highlighting vulnerabilities in physical access controls. This incident prompted companies to implement advanced encryption and biometric verification to enhance security protocols against badge cloning attacks.
High-Profile Security Breaches via Cloned Badges
High-profile security breaches often involve cloned access control badges that replicate legitimate credentials, allowing unauthorized individuals to bypass physical security measures undetected. Attackers use advanced RFID skimming technology to copy badge data, facilitating entry into restricted areas of corporate headquarters, government facilities, and data centers. These incidents result in significant data theft, espionage, and disruption, highlighting vulnerabilities in traditional badge access systems and the critical need for multi-factor authentication and enhanced encryption protocols.
Detection Methods for Cloned Access Badges
Detection methods for cloned access badges include the implementation of multi-factor authentication systems that require biometric verification alongside badge scans, rendering cloned badges ineffective alone. Real-time monitoring of access logs using machine learning algorithms can identify anomalies such as duplicate entries from different locations or unusual access times. Advanced RFID technology with encrypted communication protocols and rolling codes significantly reduces the risk of successful badge cloning by preventing static data replication.
Badge Cloning: Insider Threats and Social Engineering
Badge cloning poses significant risks in access control systems, often exploited through insider threats where employees misuse legitimate credentials to replicate access badges. Social engineering tactics, such as phishing or pretexting, enable attackers to obtain badge information covertly, facilitating unauthorized entry. Implementing multifactor authentication and continuous monitoring can mitigate vulnerabilities associated with badge cloning incidents.
Consequences of Badge Cloning in Critical Infrastructure
Badge cloning in access control systems can lead to unauthorized entry into critical infrastructure, posing severe security breaches and operational disruptions. Attackers exploiting cloned badges may gain access to sensitive areas, resulting in theft, sabotage, or manipulation of essential services. The consequences include compromised safety protocols, financial loss, and potential threats to national security.
Lessons Learned from Badge Cloning Cases
Badge cloning incidents reveal critical vulnerabilities in RFID access control systems, emphasizing the importance of multi-factor authentication and encrypted communication protocols. Organizations must implement regular security audits and employee training to detect and prevent unauthorized badge replication effectively. Continuous monitoring and rapid response to anomalies significantly reduce the risk of security breaches from cloned access badges.
Preventing and Mitigating Badge Cloning Threats
Implementing multi-factor authentication combined with encrypted RFID badges significantly reduces the risk of badge cloning in access control systems. Regularly updating encryption protocols and conducting security audits help identify vulnerabilities before attackers exploit them. Deploying anti-cloning technologies such as dynamic credential generation and biometric verification further strengthens defenses against unauthorized entry.
example of badge cloning in access control Infographic
 samplerz.com
samplerz.com