A canary in a codebase refers to a small, strategically placed piece of code designed to detect unauthorized or malicious modifications in a software system. This security measure acts as an early warning indicator, alerting developers when an unexpected change occurs, potentially pointing to a security breach or tampering. Common examples include hidden checksums, specific function calls, or sentinel variables that trigger alerts when altered. Implementing canaries enhances the integrity of the codebase by providing real-time monitoring against intrusions or code corruption. These canaries work by comparing current values against known safe states, raising flags if discrepancies arise. Data gathered from canaries assists security teams in quickly identifying compromised components, improving incident response times and overall software security posture.
Table of Comparison
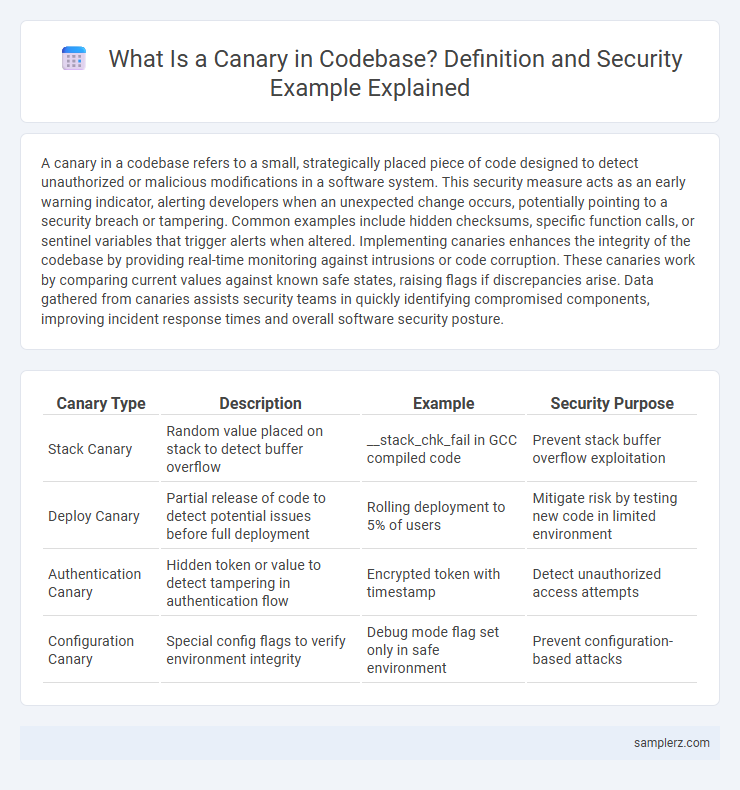
| Canary Type | Description | Example | Security Purpose |
|---|---|---|---|
| Stack Canary | Random value placed on stack to detect buffer overflow | __stack_chk_fail in GCC compiled code | Prevent stack buffer overflow exploitation |
| Deploy Canary | Partial release of code to detect potential issues before full deployment | Rolling deployment to 5% of users | Mitigate risk by testing new code in limited environment |
| Authentication Canary | Hidden token or value to detect tampering in authentication flow | Encrypted token with timestamp | Detect unauthorized access attempts |
| Configuration Canary | Special config flags to verify environment integrity | Debug mode flag set only in safe environment | Prevent configuration-based attacks |
Understanding Canary Values in Codebases
Canary values in codebases serve as early warning markers embedded in memory structures to detect buffer overflow attacks by monitoring unexpected changes during program execution. These specially crafted values, often placed between critical variables and control data like return addresses, help maintain program integrity by triggering security responses when altered. Utilizing canary values effectively mitigates exploitation risks and enhances overall software security posture through proactive detection.
Why Use Canaries for Security Detection?
Canaries in a codebase function as early warning signals by embedding secret tokens or values that trigger alerts if altered, indicating potential tampering or unauthorized access. They enable rapid detection of vulnerabilities such as buffer overflows or code injection attacks before attackers can exploit them fully. Using canaries enhances security monitoring by providing proactive identification of breaches, minimizing damage, and ensuring integrity of critical system components.
Common Types of Codebase Canaries
Common types of codebase canaries include feature flags, dead code segments, and timing checks, which help detect unauthorized or unintended code changes. Feature flags selectively enable or disable features to monitor and isolate potential security issues, while dead code segments serve as traps that trigger alerts when accessed. Timing checks detect deviations in normal execution time, indicating possible tampering or malicious activity within the codebase.
Real-World Examples of Canary Deployments
Canary deployments in security often involve releasing a new authentication module to a small user segment to monitor for vulnerabilities or performance issues before a full rollout. For instance, Google frequently employs canary releases across its infrastructure to detect security flaws early in Chrome updates by exposing a limited user base to new patches. This real-world approach minimizes widespread risk by isolating potential threats within a controlled environment, enhancing overall system resilience.
Implementing Canaries in Source Code Repositories
Implementing canaries in source code repositories involves inserting subtle markers or tokens within the code to detect unauthorized changes or breaches early. These canaries act as triggers that alert security teams if malicious actors attempt to tamper with critical files, enhancing the integrity monitoring of the codebase. Regular automated scans and version control hooks can be configured to monitor these markers, ensuring prompt detection of suspicious activities.
Detecting Unauthorized Access with Canaries
Canaries embedded in the codebase serve as traps that trigger alerts when unauthorized access attempts occur, enabling early detection of breaches. These strategically placed canaries monitor sensitive functions or data modifications to identify suspicious activity in real-time. By analyzing canary activation logs, security teams can swiftly respond to potential intrusions, minimizing damage and ensuring system integrity.
Canary Tokens: A Practical Guide
Canary tokens act as hidden tripwires within a codebase, triggering alerts when accessed by unauthorized entities, thereby enhancing security monitoring. Implementing canary tokens strategically across sensitive files, API keys, or configuration settings helps detect breaches early and limits potential damage. These tokens provide practical, low-overhead intrusion detection that integrates seamlessly with existing security workflows.
Automating Canary Placement in Codebases
Automating canary placement in codebases involves integrating scripts that systematically insert security canaries at vulnerable function entry points to detect buffer overflows and memory corruption. Tools leveraging static code analysis can identify high-risk areas and deploy canary tokens without manual intervention, enhancing detection reliability and reducing human error. Continuous integration pipelines benefit from this automation by consistently updating canary placements as the code evolves, ensuring persistent protection against exploitation attempts.
Monitoring and Alerting for Canary Triggers
Canary triggers in a codebase function as proactive security measures by continuously monitoring system behavior for anomalies and performance deviations. Effective implementation of monitoring tools like Prometheus or Datadog enables real-time alerting when predefined canary events occur, ensuring rapid detection of potential vulnerabilities or breaches. Automated alerting mechanisms integrated with incident response workflows maximize response efficiency and mitigate security risks promptly.
Best Practices for Canary Usage in Security
Canaries in codebases act as early warning signals to detect security breaches by embedding unique, unpredictable values that trigger alerts when tampered with. Best practices for canary usage include regularly rotating canary values, ensuring canaries are deeply integrated into critical code paths, and monitoring their integrity through automated tools to enable rapid incident response. Implementing encrypted and obfuscated canaries further enhances protection against attackers attempting to bypass these security measures.
example of canary in codebase Infographic
 samplerz.com
samplerz.com