Piggybacking in entry control refers to an unauthorized person gaining access to a restricted area by closely following an authorized individual without proper credentials. This security breach occurs when an authorized employee holds the door open, unaware that an intruder is slipping in behind them. In physical security systems, piggybacking exploits human behavior and lapses in vigilance at controlled entry points. To prevent piggybacking, organizations implement measures such as turnstiles, mantraps, and card readers that require individual authentication. Security personnel are trained to observe tailgating attempts and enforce strict access protocols. Data from access logs can help identify patterns of unauthorized entry related to piggybacking incidents, enabling targeted security improvements.
Table of Comparison
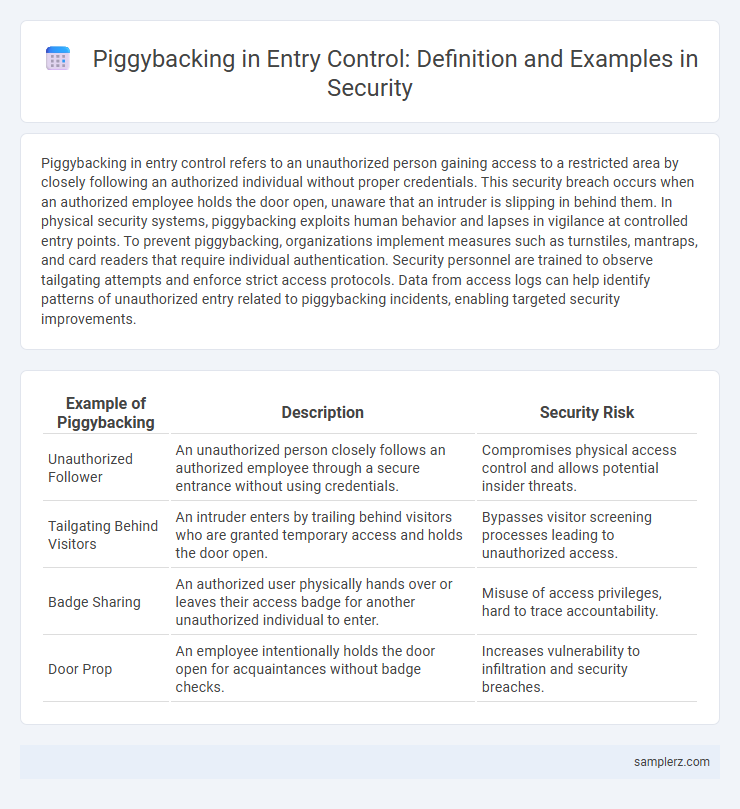
| Example of Piggybacking | Description | Security Risk |
|---|---|---|
| Unauthorized Follower | An unauthorized person closely follows an authorized employee through a secure entrance without using credentials. | Compromises physical access control and allows potential insider threats. |
| Tailgating Behind Visitors | An intruder enters by trailing behind visitors who are granted temporary access and holds the door open. | Bypasses visitor screening processes leading to unauthorized access. |
| Badge Sharing | An authorized user physically hands over or leaves their access badge for another unauthorized individual to enter. | Misuse of access privileges, hard to trace accountability. |
| Door Prop | An employee intentionally holds the door open for acquaintances without badge checks. | Increases vulnerability to infiltration and security breaches. |
Understanding Piggybacking in Entry Control
Piggybacking in entry control occurs when an unauthorized individual gains access to a secure area by closely following an authorized person, exploiting the moment before the door or gate closes. This security breach highlights the importance of implementing strict access control measures such as turnstiles, mantraps, and vigilant personnel to identify and prevent unauthorized tailgating. Understanding piggybacking helps organizations enhance physical security by ensuring only authenticated personnel enter restricted zones, reducing the risk of theft, sabotage, or data breaches.
Common Real-World Piggybacking Scenarios
Common real-world piggybacking scenarios in entry control include unauthorized individuals following authorized personnel through secure doors without using credentials, often seen in office buildings or data centers. Tailgating occurs when an employee holds the door open for someone they assume has access, creating a security breach. Security measures like access control systems with turnstiles or mantraps help mitigate these risks by enforcing individual authentication.
Case Study: Office Building Access Breach
Piggybacking in entry control occurred when an unauthorized individual gained access to a secured office building by following closely behind an employee using their access badge. The breach was identified after security footage revealed the imposter exploiting the trust of staff members during peak entry times, bypassing biometric verification systems. This case underscores the critical need for stricter turnstile controls and employee awareness training to prevent unauthorized physical access.
Piggybacking in Secure Data Centers
Piggybacking in secure data centers occurs when an unauthorized individual follows an authorized employee through controlled entry points, bypassing security protocols. This breach exploits human error or distraction, allowing potential access to sensitive information and critical infrastructure. Employing multi-factor authentication and implementing mantrap systems significantly reduce the risk of such unauthorized access.
Examples of Tailgating vs. Piggybacking
Tailgating occurs when an unauthorized person follows an authorized individual through a secured entry without consent, such as slipping in behind someone carrying a key card through a door. Piggybacking involves the authorized individual knowingly allowing the unauthorized person to enter, like holding the door open for a colleague without verifying their credentials. Both tactics exploit human behavior to bypass access controls but differ in the level of complicity from authorized personnel.
Insider Threats: Employees Allowing Unauthorized Entry
Piggybacking in entry control often involves employees intentionally or unknowingly allowing unauthorized individuals to enter secure areas by holding doors open or bypassing authentication protocols. This insider threat exploits trust within the organization, compromising physical security and increasing vulnerability to theft, espionage, or sabotage. Implementing strict access policies and continuous employee training reduces the risk of piggybacking and enhances overall security posture.
Technologies Exploited in Piggybacking Attacks
Piggybacking in entry control often exploits technologies such as RFID access cards, which can be easily copied or intercepted through signal amplification and relay attacks. Biometric systems may also be vulnerable when attackers use fake fingerprints or facial masks to bypass authentication. Tailgating sensors and access control systems lacking multi-factor verification can be manipulated, allowing unauthorized individuals to follow authorized personnel into secure areas undetected.
Piggybacking at Educational Institutions
Piggybacking in educational institutions occurs when unauthorized individuals gain entry by following closely behind authorized personnel through secured access points, exploiting the trust and vigilance of staff or students. This security breach compromises campus safety, potentially allowing threats such as theft, vandalism, or violence to go undetected. Implementing strict access protocols, such as electronic turnstiles or biometric verification, significantly reduces the risk of piggybacking and enhances overall entry control effectiveness.
Preventing Piggybacking in Entry Systems
Effective prevention of piggybacking in entry control systems involves implementing advanced access technologies such as turnstiles, mantraps, and biometric scanners that ensure only one individual enters per authorized credential. Security personnel training on vigilance and strict enforcement of access protocols significantly reduces unauthorized tailgating attempts. Integrating video surveillance with real-time monitoring further enhances the detection and deterrence of piggybacking incidents in sensitive facilities.
Security Policy Failures Leading to Piggybacking
Security policy failures leading to piggybacking often stem from inadequate enforcement of access control measures, such as tailgating detection and lack of employee training on security protocols. When access policies do not mandate strict verification or fail to educate personnel on the risks of unauthorized entry, individuals can exploit these gaps to gain entry by closely following authorized personnel. Organizations face increased vulnerability to data breaches and physical theft when entry control systems lack robust authentication methods like biometric scanning or multi-factor access badges.
example of piggybacking in entry control Infographic
 samplerz.com
samplerz.com