A watering hole attack in cybersecurity involves targeting a specific group or organization by compromising websites they frequently visit. For example, in a targeted attack against a financial institution, hackers might infiltrate industry forums or trusted news sites related to banking. Once these sites are infected with malware, users from the targeted organization who access the site become vulnerable to data breaches or credential theft. The technique leverages the trust users place in legitimate websites, making detection more difficult. Attackers collect intelligence on the target's browsing habits to identify watering holes that deliver the greatest impact. This method is prevalent in espionage campaigns where attackers seek sensitive corporate or government data by exploiting familiar digital environments.
Table of Comparison
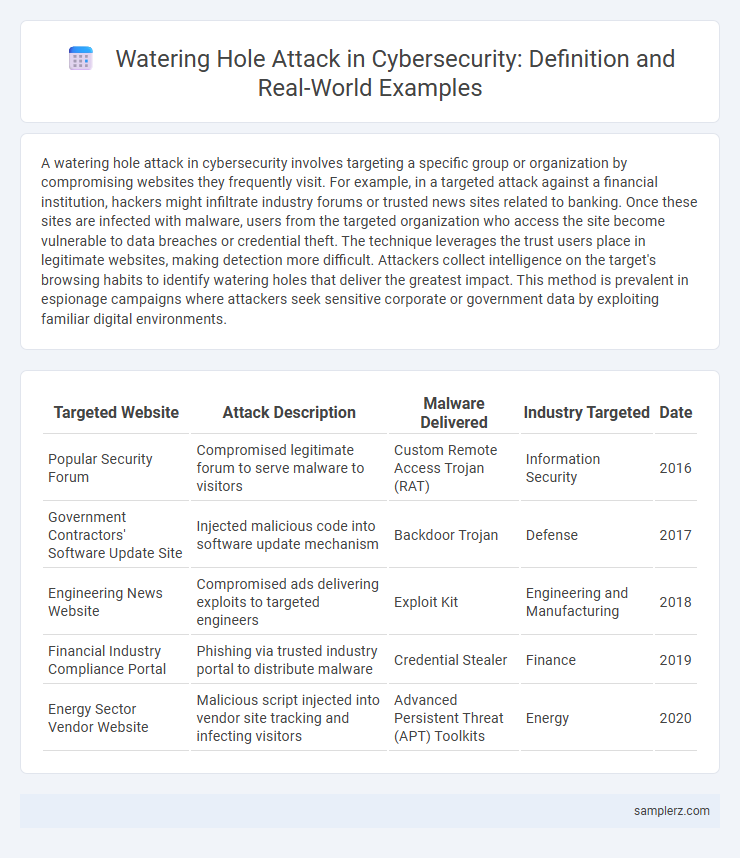
| Targeted Website | Attack Description | Malware Delivered | Industry Targeted | Date |
|---|---|---|---|---|
| Popular Security Forum | Compromised legitimate forum to serve malware to visitors | Custom Remote Access Trojan (RAT) | Information Security | 2016 |
| Government Contractors' Software Update Site | Injected malicious code into software update mechanism | Backdoor Trojan | Defense | 2017 |
| Engineering News Website | Compromised ads delivering exploits to targeted engineers | Exploit Kit | Engineering and Manufacturing | 2018 |
| Financial Industry Compliance Portal | Phishing via trusted industry portal to distribute malware | Credential Stealer | Finance | 2019 |
| Energy Sector Vendor Website | Malicious script injected into vendor site tracking and infecting visitors | Advanced Persistent Threat (APT) Toolkits | Energy | 2020 |
Understanding Watering Hole Attacks in Cybersecurity
Watering hole attacks in cybersecurity exploit websites frequently visited by targeted organizations to deliver malware or phishing schemes. Attackers compromise these trusted sites, embedding malicious code that silently infects visitors' devices, enabling data theft or network infiltration. Recognizing patterns of unusual traffic and employing threat intelligence can help organizations detect and mitigate watering hole threats effectively.
Key Characteristics of Watering Hole Techniques
Watering hole attacks exploit specific websites frequented by a target group, compromising them to deliver malware tailored to those visitors. These attacks uniquely combine reconnaissance on victim habits, precise timing to maximize exposure, and stealthy infection methods that avoid detection. Key characteristics include selective targeting of high-traffic sites relevant to the victim, minimal footprint infection on legitimate websites, and use of advanced persistent threats (APT) to maintain long-term access.
Real-World Watering Hole Attack Case Studies
The 2013 attack targeting visiting professionals on the Council on Foreign Relations website exemplifies a sophisticated watering hole attack, where hackers compromised a trusted site to deliver malware. Another notable case involved the U.S. Department of Labor website being infected to target visitors from specific industries, illustrating how attackers exploit sector-specific sites to infiltrate high-value targets. These real-world examples highlight the effectiveness of watering hole attacks in breaching defensive perimeters by leveraging trust in frequently accessed web resources.
How Attackers Choose Targeted Websites
Attackers select targeted watering hole websites by analyzing the online behavior and preferences of their intended victims, often focusing on industry-specific forums, professional associations, or frequently visited community sites. They leverage threat intelligence and reconnaissance tools to identify websites with lower security defenses where vulnerable code or outdated plugins can be exploited easily. By compromising these carefully chosen sites, attackers increase the likelihood of infecting the target group with malware while minimizing exposure.
Steps in the Watering Hole Attack Lifecycle
The watering hole attack lifecycle begins with attackers identifying websites frequented by their target group and compromising these sites by injecting malicious code. Once infected, the targeted victims unknowingly visit these trusted sites, leading to the silent installation of malware or exploitation of browser vulnerabilities. The final step involves attackers leveraging the gained access to escalate privileges, maintain persistence, and exfiltrate sensitive data from compromised systems.
Common Malware Used in Watering Hole Campaigns
Common malware used in watering hole campaigns includes Remote Access Trojans (RATs) like Poison Ivy and PlugX, which enable attackers to maintain persistent control over compromised systems. Exploit kits such as Angler and Neutrino are frequently deployed to exploit software vulnerabilities and deliver payloads stealthily. Additionally, credential stealers like Zeus Panda and keyloggers are commonly utilized to harvest sensitive information from targeted victims.
Impact of Watering Hole Attacks on Organizations
Watering hole attacks compromise websites frequently visited by target organizations, leading to malware infiltration and unauthorized access. These attacks cause significant data breaches, operational disruption, and reputation damage, costing organizations millions in recovery and regulatory fines. Detecting watering hole threats remains challenging due to their targeted nature and the use of legitimate websites to deliver payloads.
Detection Methods for Watering Hole Threats
Watering hole attacks exploit legitimate websites frequently visited by targeted users, injecting malicious code to compromise systems. Detection methods include monitoring unusual web traffic patterns, analyzing browser behavior anomalies, and utilizing sandbox environments to identify malicious payloads embedded in trusted sites. Employing threat intelligence feeds and continuous endpoint monitoring enhances the identification of watering hole threats in enterprise networks.
Preventative Measures Against Watering Hole Attacks
Watering hole attacks exploit frequently visited websites to infect target systems with malware, making detection challenging. Implementing strict browser security policies, regularly updating software, and employing advanced threat intelligence for real-time monitoring can significantly reduce the risk. Network segmentation and user education on phishing awareness further enhance defense against these targeted compromises.
Lessons Learned from Notable Watering Hole Incidents
Notable watering hole attacks, such as the 2013 compromise of the National Democratic Institute's website, highlight the effectiveness of targeting trusted sites frequented by specific groups. These incidents underscore the necessity of rigorous website security audits, timely patch management, and comprehensive user education on detecting unusual site behavior. Proactive monitoring and collaboration between organizations and security researchers significantly reduce the risks associated with watering hole threats.
example of watering hole in targeted attack Infographic
 samplerz.com
samplerz.com