Bluejacking is a Bluetooth-based security attack where an attacker sends unsolicited messages to nearby Bluetooth-enabled devices. This technique exploits the Bluetooth protocol's ability to exchange contact information, allowing attackers to send text or vCards without proper authorization. Bluejacking is often used for prank messaging but can pose privacy concerns in public or crowded places like airports and cafes. Data collected from bluejacking incidents reveals that attackers typically remain anonymous since the recipient sees only the sender's Bluetooth name and not the device's actual identity. The attack requires close proximity, usually within 10 meters, due to Bluetooth's limited range. Security measures such as disabling Bluetooth visibility or using device authentication help mitigate the risks associated with bluejacking attempts.
Table of Comparison
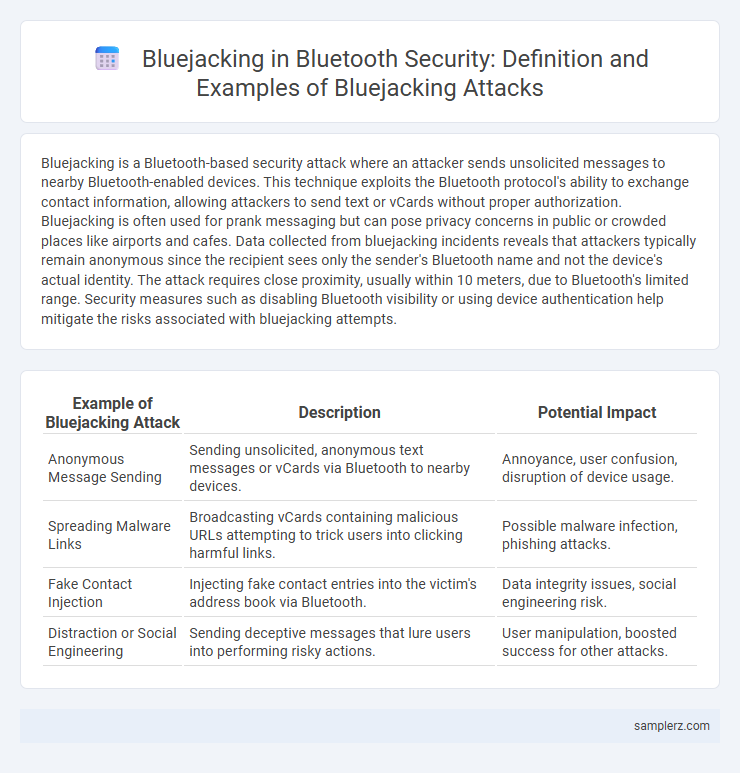
| Example of Bluejacking Attack | Description | Potential Impact |
|---|---|---|
| Anonymous Message Sending | Sending unsolicited, anonymous text messages or vCards via Bluetooth to nearby devices. | Annoyance, user confusion, disruption of device usage. |
| Spreading Malware Links | Broadcasting vCards containing malicious URLs attempting to trick users into clicking harmful links. | Possible malware infection, phishing attacks. |
| Fake Contact Injection | Injecting fake contact entries into the victim's address book via Bluetooth. | Data integrity issues, social engineering risk. |
| Distraction or Social Engineering | Sending deceptive messages that lure users into performing risky actions. | User manipulation, boosted success for other attacks. |
Understanding Bluejacking: A Bluetooth-Based Threat
Bluejacking is a Bluetooth-based security threat that involves sending unsolicited messages to nearby Bluetooth-enabled devices without the recipient's consent. This attack exploits the Bluetooth protocol's lack of authentication for message exchange, allowing attackers to transmit spam, phishing links, or malware disguised as harmless messages. Understanding bluejacking is crucial for implementing protective measures such as disabling Bluetooth visibility, using secure pairing methods, and enabling device authentication to prevent unauthorized access and potential data breaches.
How Bluejacking Works in Real-World Scenarios
Bluejacking exploits Bluetooth technology by sending unsolicited, anonymous messages to nearby devices within roughly 10 meters, often using contact cards to transmit text or images without pairing. Attackers typically scan for discoverable Bluetooth-enabled devices in public spaces like cafes or airports, then inject messages that may appear harmless but can disrupt user experience or serve as phishing prompts. This technique leverages Bluetooth's default visibility settings, emphasizing the importance of managing device discoverability to mitigate unauthorized message reception in real-world environments.
Common Devices Vulnerable to Bluejacking Attacks
Common devices vulnerable to bluejacking attacks include smartphones, tablets, and laptops with Bluetooth capabilities enabled in discoverable mode. These devices often lack adequate security settings, allowing attackers to send unsolicited messages or files within the Bluetooth range. Wearable tech such as smartwatches and Bluetooth-enabled headphones also face risks due to their persistent Bluetooth connectivity and limited user interface for security management.
Notable Examples of Bluejacking Incidents
Notable examples of bluejacking incidents include the 2003 case where a prankster sent unsolicited messages to thousands of commuters on London's Underground, causing panic and confusion. Another incident occurred at the 2005 tech conference in Las Vegas, where attendees received mysterious promotional messages via Bluetooth, highlighting vulnerabilities in conference security protocols. These cases underscore the potential for bluejacking to disrupt public spaces and raise awareness about Bluetooth device security.
Step-by-Step Breakdown of a Bluejacking Attack
Bluejacking involves sending unsolicited messages via Bluetooth to discoverable devices within proximity, typically targeting mobile phones or laptops. The attacker enables Bluetooth, scans for nearby discoverable devices, composes a brief message, and transmits it using the device's contact-sharing feature, exploiting the protocol's lack of authentication for received messages. This method poses minimal risk but highlights vulnerabilities in Bluetooth security protocols that could be leveraged in more sophisticated attacks.
Bluejacking vs. Other Bluetooth Attacks: Key Differences
Bluejacking involves sending unsolicited messages to nearby Bluetooth devices, primarily as a harmless prank or social experiment, without exploiting device vulnerabilities. In contrast, other Bluetooth attacks like Bluebugging and Bluesnarfing aim to gain unauthorized access to device data or control by exploiting security flaws. Bluejacking's limited scope and lack of data breach capabilities distinguish it from more severe threats that compromise user privacy and device integrity.
Impact of Bluejacking on Personal and Enterprise Security
Bluejacking, a Bluetooth attack involving unsolicited messages sent to nearby devices, can cause significant disruptions in both personal and enterprise environments by exposing users to privacy breaches and social engineering risks. In personal security, bluejacking may lead to annoyance, confusion, and potential phishing attempts through deceptive messages. For enterprises, this vulnerability can result in compromised confidential information, decreased employee productivity, and increased vulnerability to coordinated cyber-attacks targeting Bluetooth-enabled devices.
Famous Cases of Bluejacking in Public Spaces
Famous cases of bluejacking in public spaces often involve unsolicited messages sent to strangers' Bluetooth-enabled devices, creating confusion and highlighting vulnerabilities in wireless communication. One notable incident occurred in 2004 at a busy London Tube station, where commuters received mysterious, humorous messages broadcast via Bluetooth, raising awareness of the attack method. These events emphasize the need for stronger Bluetooth security measures in public environments to prevent unauthorized access and harassment.
Preventing Bluejacking: Practical Bluetooth Security Tips
Bluejacking, a Bluetooth attack involving unsolicited messages sent to nearby devices, can be prevented by disabling Bluetooth visibility when not in use and accepting connections only from known devices. Regularly updating device firmware enhances security by patching vulnerabilities attackers might exploit during bluejacking attempts. Employing Bluetooth security settings such as authentication and encryption further mitigates the risk of unauthorized message injections and potential data breaches.
The Future of Bluejacking: Evolving Methods and Risks
Bluejacking, initially a harmless prank of sending unsolicited messages via Bluetooth, is evolving into a vector for sophisticated phishing and social engineering attacks, exploiting increased device connectivity. Emerging threats include targeted data exfiltration and malware distribution through disguised bluetooth packets, raising significant privacy and cybersecurity concerns. Continuous advancements in Bluetooth technology necessitate proactive security protocols to mitigate these evolving risks and protect future wireless communications.
example of bluejacking in Bluetooth attack Infographic
 samplerz.com
samplerz.com