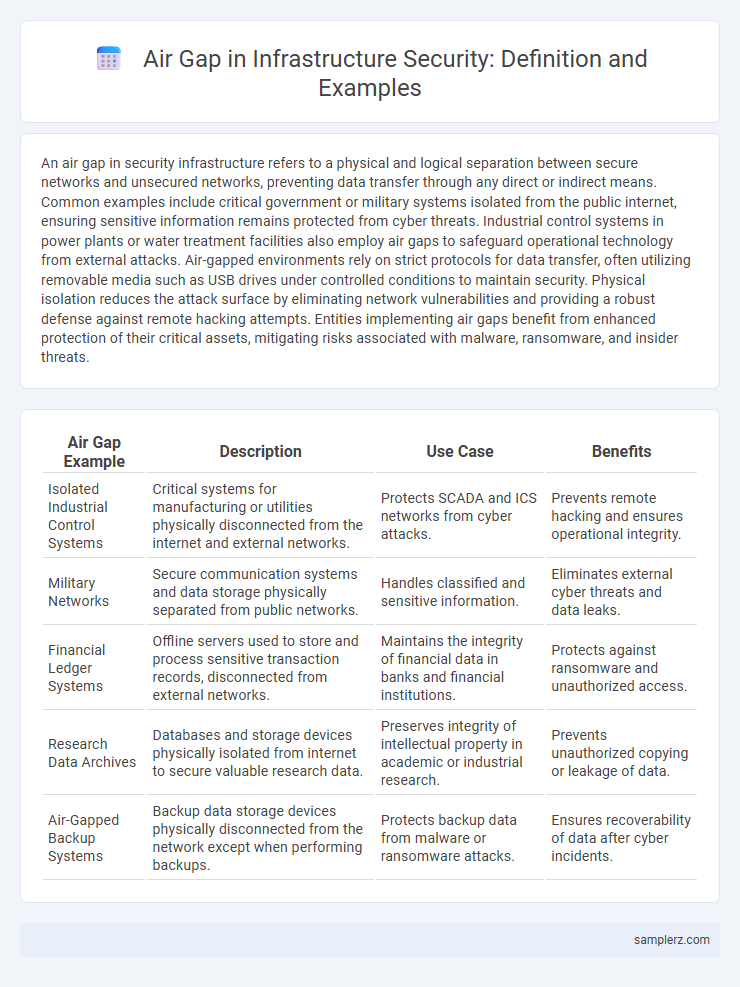
An air gap in security infrastructure refers to a physical and logical separation between secure networks and unsecured networks, preventing data transfer through any direct or indirect means. Common examples include critical government or military systems isolated from the public internet, ensuring sensitive information remains protected from cyber threats. Industrial control systems in power plants or water treatment facilities also employ air gaps to safeguard operational technology from external attacks. Air-gapped environments rely on strict protocols for data transfer, often utilizing removable media such as USB drives under controlled conditions to maintain security. Physical isolation reduces the attack surface by eliminating network vulnerabilities and providing a robust defense against remote hacking attempts. Entities implementing air gaps benefit from enhanced protection of their critical assets, mitigating risks associated with malware, ransomware, and insider threats.
Table of Comparison
| Air Gap Example | Description | Use Case | Benefits |
|---|---|---|---|
| Isolated Industrial Control Systems | Critical systems for manufacturing or utilities physically disconnected from the internet and external networks. | Protects SCADA and ICS networks from cyber attacks. | Prevents remote hacking and ensures operational integrity. |
| Military Networks | Secure communication systems and data storage physically separated from public networks. | Handles classified and sensitive information. | Eliminates external cyber threats and data leaks. |
| Financial Ledger Systems | Offline servers used to store and process sensitive transaction records, disconnected from external networks. | Maintains the integrity of financial data in banks and financial institutions. | Protects against ransomware and unauthorized access. |
| Research Data Archives | Databases and storage devices physically isolated from internet to secure valuable research data. | Preserves integrity of intellectual property in academic or industrial research. | Prevents unauthorized copying or leakage of data. |
| Air-Gapped Backup Systems | Backup data storage devices physically disconnected from the network except when performing backups. | Protects backup data from malware or ransomware attacks. | Ensures recoverability of data after cyber incidents. |
Understanding Air Gap in Infrastructure Security
Air gap in infrastructure security refers to the physical isolation of a computer or network from unsecured networks, especially the internet, to prevent unauthorized access and cyber threats. This method is commonly used in critical environments like government agencies, military systems, and industrial control systems where sensitive data integrity and confidentiality are paramount. Implementing an air gap involves disconnecting systems from wireless and wired networks, ensuring data transfer occurs only through controlled, manual processes to mitigate risks of remote exploitation.
Key Principles Behind Air-Gapped Systems
Air-gapped systems isolate critical infrastructure by physically separating networks, preventing unauthorized data flow and cyber intrusions. This isolation ensures that sensitive information remains inaccessible from external threats, relying on strict access controls and manual data transfer methods such as removable media. The core principles emphasize strong physical security, rigorous authentication processes, and controlled data pathways to maintain integrity and confidentiality.
Classic Examples of Air-Gapped Military Networks
Classic examples of air-gapped military networks include the U.S. Department of Defense's Global Command and Control System (GCCS) and the UK's Strategic Command Network (SCN), both designed to operate independently from public internet connections to prevent unauthorized access. These networks utilize physical isolation techniques, such as standalone servers and dedicated communication lines, to ensure sensitive military data remains secure from cyber threats. The implementation of strict access controls, combined with rigorous manual data transfer processes, exemplifies the effective use of air gaps in safeguarding critical defense infrastructure.
Air Gaps in Financial Institution Data Centers
Air gaps in financial institution data centers create physical isolation between critical systems and external networks, preventing cyber threats and unauthorized access. These isolated environments ensure transaction data integrity and protect sensitive customer information from ransomware and advanced persistent threats. Implementing strict air gap protocols enhances regulatory compliance and reduces the risk of data breaches in banking infrastructure.
Industrial Control Systems Utilizing Air Gaps
Industrial Control Systems (ICS) often implement air gaps by physically isolating critical network segments from external or corporate networks to prevent cyber threats and unauthorized access. This isolation blocks remote connections and malware infiltration, ensuring operational technology remains secure and uninterrupted. In manufacturing plants and utilities, air-gapped ICS protect sensitive control processes from internet-based vulnerabilities and targeted attacks.
Air Gap Implementation in Healthcare IT Environments
Air gap implementation in healthcare IT environments involves physically isolating sensitive medical devices and electronic health record (EHR) systems from unsecured networks to prevent cyber threats and unauthorized access. This separation ensures critical patient data remains protected against ransomware attacks and data breaches by eliminating direct network connectivity. Hospitals often deploy dedicated air-gapped workstations for diagnostic equipment and offline backups, significantly enhancing the resilience of their cybersecurity posture.
Critical Infrastructure: Power Grids and Air-Gapped Solutions
Power grids utilize air-gapped solutions by physically isolating control systems from external networks to prevent cyber intrusions and ensure operational continuity. These isolated networks manage real-time data for substations and grid management, minimizing exposure to remote attacks. Implementation of air gaps in critical infrastructure enhances resilience by allowing secure manual data transfers and offline system updates.
Limitations and Risks of Air-Gapped Networks
Air-gapped networks, physically isolated from unsecured networks, face limitations including challenges in data transfer, requiring manual intervention that increases human error risk. They are vulnerable to insider threats and sophisticated attacks like electromagnetic or acoustic signal leaks, which can bypass isolation. Maintenance complexity and costs also rise due to stringent security protocols and lack of automated updates.
Real-World Breaches: Circumventing Air Gaps
Real-world breaches have demonstrated that air gaps are not impervious to attack, with adversaries exploiting supply chain vulnerabilities, insider threats, and compromised removable media to infiltrate isolated networks. For instance, the Stuxnet malware famously bypassed air-gapped systems by spreading via infected USB drives, targeting Iran's nuclear facilities. These incidents highlight the critical need for comprehensive security protocols beyond physical separation to safeguard sensitive infrastructure.
Best Practices for Maintaining Air Gaps in Modern Infrastructure
Maintaining air gaps in modern infrastructure involves physically isolating critical systems from unsecured networks by using dedicated hardware and network segmentation to prevent unauthorized data flow. Best practices include regular verification of physical separation, strict control of removable media, and implementing rigorous access controls coupled with monitoring to detect potential bridging attempts. Employing hardware-based firewalls and ensuring offline backups further fortify air gaps against cyber threats and ensure robust, uncompromised security.
example of air gap in infrastructure Infographic
 samplerz.com
samplerz.com