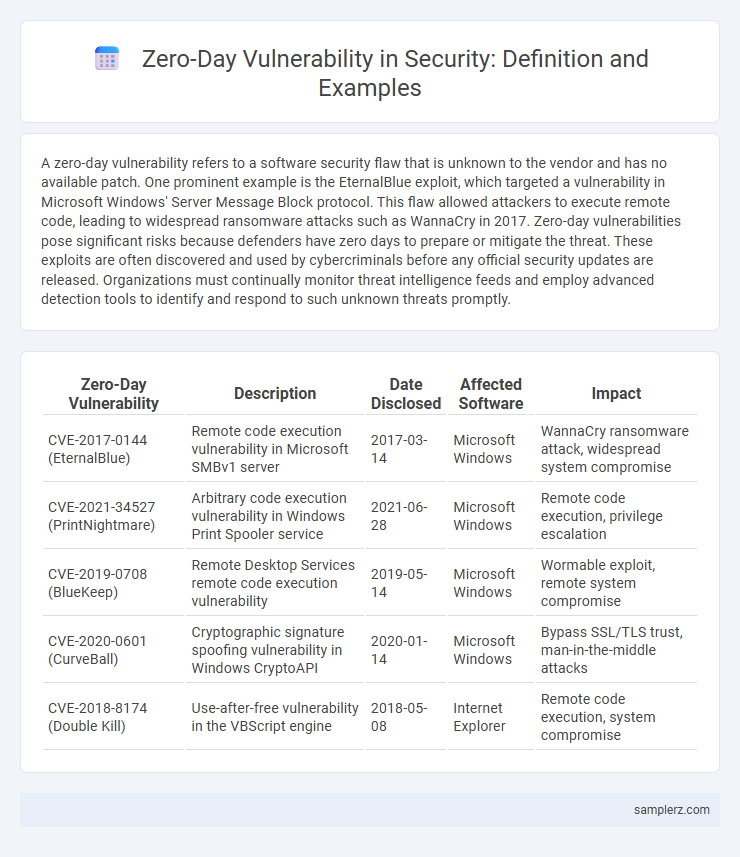
A zero-day vulnerability refers to a software security flaw that is unknown to the vendor and has no available patch. One prominent example is the EternalBlue exploit, which targeted a vulnerability in Microsoft Windows' Server Message Block protocol. This flaw allowed attackers to execute remote code, leading to widespread ransomware attacks such as WannaCry in 2017. Zero-day vulnerabilities pose significant risks because defenders have zero days to prepare or mitigate the threat. These exploits are often discovered and used by cybercriminals before any official security updates are released. Organizations must continually monitor threat intelligence feeds and employ advanced detection tools to identify and respond to such unknown threats promptly.
Table of Comparison
| Zero-Day Vulnerability | Description | Date Disclosed | Affected Software | Impact |
|---|---|---|---|---|
| CVE-2017-0144 (EternalBlue) | Remote code execution vulnerability in Microsoft SMBv1 server | 2017-03-14 | Microsoft Windows | WannaCry ransomware attack, widespread system compromise |
| CVE-2021-34527 (PrintNightmare) | Arbitrary code execution vulnerability in Windows Print Spooler service | 2021-06-28 | Microsoft Windows | Remote code execution, privilege escalation |
| CVE-2019-0708 (BlueKeep) | Remote Desktop Services remote code execution vulnerability | 2019-05-14 | Microsoft Windows | Wormable exploit, remote system compromise |
| CVE-2020-0601 (CurveBall) | Cryptographic signature spoofing vulnerability in Windows CryptoAPI | 2020-01-14 | Microsoft Windows | Bypass SSL/TLS trust, man-in-the-middle attacks |
| CVE-2018-8174 (Double Kill) | Use-after-free vulnerability in the VBScript engine | 2018-05-08 | Internet Explorer | Remote code execution, system compromise |
Understanding Zero-Day Vulnerabilities
Zero-day vulnerabilities refer to software flaws unknown to developers and security vendors, leaving systems defenseless until a patch is released. A notable example is the EternalBlue exploit used in the 2017 WannaCry ransomware attack, which leveraged an unpatched Windows SMB vulnerability to spread rapidly. Understanding zero-day vulnerabilities is critical for implementing proactive security measures like intrusion detection systems and encouraging timely software updates.
Historical Overview of Major Zero-Day Attacks
The 2017 WannaCry ransomware attack exploited a zero-day vulnerability in Microsoft Windows' SMB protocol, crippling thousands of systems globally and highlighting the catastrophic potential of undisclosed flaws. In 2010, the Stuxnet worm leveraged multiple zero-day exploits to target Iranian nuclear facilities, marking a significant moment in cyber warfare using zero-day vulnerabilities. Another notable event was the 2013 Adobe Flash zero-day exploit, which facilitated widespread malware distribution before the vulnerability was patched, emphasizing the importance of timely vulnerability management.
Anatomy of a Zero-Day Vulnerability
A zero-day vulnerability is a software flaw unknown to the vendor and exploited by attackers before a patch is available, making it highly dangerous. The anatomy of a zero-day includes an undisclosed security weakness, an exploit code designed to take advantage, and the vulnerability's lifecycle starting from discovery, through active exploitation, to eventual remediation. Understanding this process helps cybersecurity teams prioritize threat detection, containment, and patch management to mitigate the impact of zero-day attacks.
Real-World Zero-Day Exploit Case Studies
The 2021 Microsoft Exchange Server zero-day vulnerabilities, exploited by the Hafnium group, demonstrated how attackers leveraged undisclosed flaws to access email accounts and deploy malware. This real-world case highlighted the critical need for timely patch management and threat intelligence sharing in cybersecurity defenses. Exploits like these emphasize the persistent risk posed by zero-days in enterprise environments.
How Zero-Day Vulnerabilities Are Discovered
Zero-day vulnerabilities are often discovered through advanced threat hunting techniques, including automated scanning tools that analyze software behavior for anomalies. Cybersecurity researchers and ethical hackers also uncover zero-day flaws by performing rigorous code audits and penetration testing on applications and operating systems. In some cases, zero-day exploits surface when malicious actors report or use the unknown vulnerability before developers patch the software.
Famous Zero-Day Incidents in Popular Software
The 2017 WannaCry ransomware attack exploited a famous zero-day vulnerability in Microsoft Windows' SMB protocol, causing widespread disruption globally. Another significant zero-day incident was the Stuxnet worm in 2010, which targeted Siemens industrial control systems, showcasing the potential of cyberattacks on critical infrastructure. Adobe Flash Player also faced multiple zero-day vulnerabilities exploited by attackers before being officially discontinued due to security risks.
Impact of Zero-Day Vulnerabilities on Cybersecurity
Zero-day vulnerabilities pose critical risks to cybersecurity by enabling attackers to exploit unknown flaws before patches are available, leading to data breaches and system compromises. High-profile incidents like the WannaCry ransomware attack demonstrate how zero-days can disrupt global networks and cause significant financial and operational damage. Effective threat intelligence and proactive vulnerability management are essential to mitigate the impact of zero-day exploits on organizational security.
Zero-Day Vulnerability Lifecycle Explained
Zero-day vulnerability lifecycle begins with the discovery of an unknown flaw in software or hardware that attackers can exploit before developers release a patch. Cybercriminals often weaponize zero-day exploits to infiltrate systems undetected, causing data breaches or system failures. The lifecycle concludes when a vendor issues a security update, and organizations deploy patches to mitigate risks associated with the zero-day vulnerability.
Prevention and Mitigation of Zero-Day Attacks
Zero-day attacks exploit undisclosed vulnerabilities, making early detection and prevention critical through robust endpoint security solutions and continuous behavioral analysis. Implementing network segmentation and applying strict access controls reduce the attack surface, limiting potential damage from unknown exploits. Regular patch management, threat intelligence sharing, and employing machine learning-based anomaly detection further strengthen defenses against zero-day threats.
Future Trends in Zero-Day Exploitation
Zero-day vulnerabilities continue to evolve with the rise of AI-driven attack methodologies, enabling cybercriminals to identify and exploit unknown flaws faster than ever before. The integration of machine learning techniques in malware allows dynamic adaptation to security defenses, increasing the stealth and impact of zero-day exploits. Future trends indicate a growing emphasis on automated vulnerability discovery tools and advanced persistent threat (APT) groups leveraging zero-day exploits in supply chain attacks and IoT device breaches.
example of zero-day in vulnerability Infographic
 samplerz.com
samplerz.com