A rainbow table is a precomputed database used to reverse cryptographic hash functions in password cracking attacks. It stores hash values of common passwords along with their plaintext equivalents, enabling attackers to quickly identify passwords by matching stored hashes from target systems. This technique significantly reduces the time required to crack hashed passwords compared to brute force methods. In the context of security, rainbow tables pose a major risk to weakly hashed password systems without salting. Modern authentication systems often use salts, which add unique random data to passwords before hashing, rendering rainbow tables ineffective by producing distinct hash outputs for identical passwords. Protecting password data with strong hashing algorithms and salts remains a critical defense against rainbow table attacks.
Table of Comparison
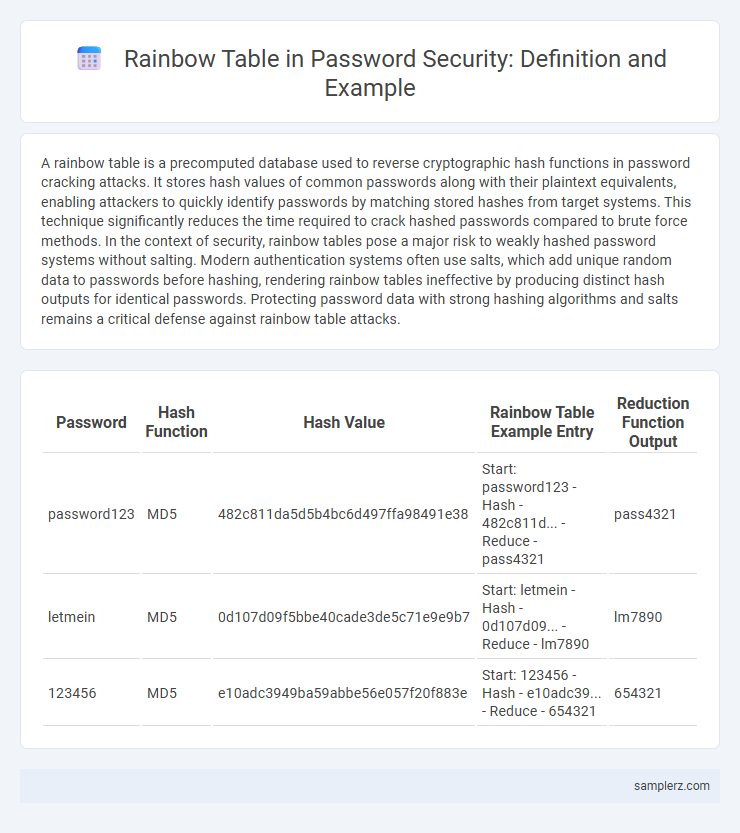
| Password | Hash Function | Hash Value | Rainbow Table Example Entry | Reduction Function Output |
|---|---|---|---|---|
| password123 | MD5 | 482c811da5d5b4bc6d497ffa98491e38 | Start: password123 - Hash - 482c811d... - Reduce - pass4321 | pass4321 |
| letmein | MD5 | 0d107d09f5bbe40cade3de5c71e9e9b7 | Start: letmein - Hash - 0d107d09... - Reduce - lm7890 | lm7890 |
| 123456 | MD5 | e10adc3949ba59abbe56e057f20f883e | Start: 123456 - Hash - e10adc39... - Reduce - 654321 | 654321 |
Introduction to Rainbow Tables in Password Security
Rainbow tables are large precomputed datasets used to reverse cryptographic hash functions, enabling attackers to efficiently crack hashed passwords by matching hash outputs to original password inputs. These tables exploit the trade-off between time and storage, significantly reducing the computational effort required compared to brute-force attacks. Commonly targeted hash algorithms include MD5 and SHA-1, which, without salting, remain vulnerable to this method of password compromise.
How Rainbow Tables Work: A Simplified Overview
Rainbow tables work by precomputing hash values for a large set of possible passwords and storing them in a compressed form, enabling rapid reverse lookup during password cracking attempts. Instead of brute-forcing each password hash individually, an attacker uses the rainbow table to match a hashed password against precomputed hash chains, drastically reducing the time required to discover the original password. These tables exploit the deterministic nature of cryptographic hash functions, trading off storage space for speed in password recovery.
Key Components of a Rainbow Table Attack
Rainbow table attacks exploit precomputed hash chains to reverse cryptographic hash functions, enabling the attacker to recover plaintext passwords efficiently. Key components include the reduction function that maps hashes back to plaintexts, the generation of hash chains that link multiple hash-reduction iterations, and the extensive precomputed tables that store these chains to facilitate rapid lookup. The effectiveness depends on the size and coverage of the table, making salted hashes a critical defense by introducing unique randomness to each password hash.
Real-World Example: Cracking Passwords with Rainbow Tables
Rainbow tables have been effectively used to crack passwords in various data breaches, such as the LinkedIn hack in 2012 where over 6.5 million hashed passwords were exposed. Attackers precomputed common password hashes using rainbow tables to reverse the MD5 hashes, enabling rapid recovery of weak or unsalted passwords. This real-world example highlights the critical importance of strong hashing algorithms combined with salting to defend against rainbow table attacks in password security.
Comparison: Rainbow Tables vs. Brute Force Attacks
Rainbow tables accelerate password cracking by using precomputed hash values, drastically reducing the time needed compared to brute force attacks that attempt every possible combination sequentially. While brute force methods require exponential time with increasing password length, rainbow tables exploit common hash algorithms and known salts to achieve faster retrieval of plaintext passwords. The efficiency of rainbow tables, however, diminishes against salts and strong hashing algorithms like bcrypt, where brute force remains a fallback despite its higher computational cost.
Famous Incidents Involving Rainbow Table Exploits
The LinkedIn data breach in 2012 is a notorious example of rainbow table exploits, where millions of hashed passwords were cracked due to inadequate salting. Attackers leveraged the precomputed hash chains to reverse-engineer encrypted passwords rapidly, exposing user credentials. This incident underscored the critical importance of strong password hashing algorithms combined with unique salts to prevent rainbow table-based attacks.
Limitations of Rainbow Tables in Modern Security
Rainbow tables, precomputed databases of hashed passwords used for cracking encrypted passwords, face significant limitations in modern security due to widespread implementation of salting techniques that add unique random data to each password before hashing. The computational cost and storage requirements of generating and maintaining rainbow tables increase exponentially with the complexity of hashing algorithms like bcrypt, Argon2, and SHA-3, rendering traditional rainbow table attacks less effective. Furthermore, the adoption of multi-factor authentication (MFA) reduces the reliance on password strength alone, further diminishing the practical impact of rainbow table attacks in secure environments.
Defending Against Rainbow Table Attacks: Best Practices
Using salted hashes significantly strengthens password security by incorporating unique random data into each password before hashing, rendering rainbow tables ineffective. Employing strong, computationally intensive hashing algorithms like bcrypt, scrypt, or Argon2 increases the time required to generate hashes, deterring attackers from using precomputed rainbow tables. Regularly updating hashing techniques and educating users about creating complex passwords further reduces the risk of successful rainbow table attacks.
The Role of Salting in Preventing Rainbow Table Attacks
Rainbow tables store precomputed hash values for common passwords, enabling attackers to quickly reverse hashed passwords without salting. Salting adds a unique random value to each password before hashing, which drastically increases the complexity and size of the hash space, rendering rainbow tables ineffective. This crucial security measure ensures that identical passwords produce different hash outputs, preventing attackers from leveraging precomputed hash databases.
Future Trends: The Evolving Threat of Rainbow Tables
Rainbow tables remain a significant threat to password security as they enable rapid password recovery by matching hashed passwords against precomputed tables of hash values. Future trends indicate an increase in the scale and complexity of rainbow tables due to advancements in GPU processing power and distributed computing, making attacks faster and more accessible to cybercriminals. Implementing robust salting techniques and adopting adaptive hashing algorithms like Argon2 and bcrypt are critical defenses against the evolving rainbow table attacks.
example of rainbow table in password Infographic
 samplerz.com
samplerz.com