A canary token is a security mechanism designed to detect unauthorized access or data breaches by embedding a unique identifier within a file. When an attacker opens or interacts with the file containing the canary token, it triggers an alert to the system administrator, indicating potential malicious activity. Common examples include embedding a URL, email address, or document metadata that sends an immediate notification upon access. In security environments, canary tokens are often placed in sensitive files such as PDFs, Word documents, or spreadsheets to monitor insider threats or external breaches. The token's data typically includes an identifiable string or code that links back to the monitoring system, allowing precise tracing of the source of the breach. Effective implementation of canary tokens helps organizations rapidly respond to threats and minimize damage from unauthorized data exposure.
Table of Comparison
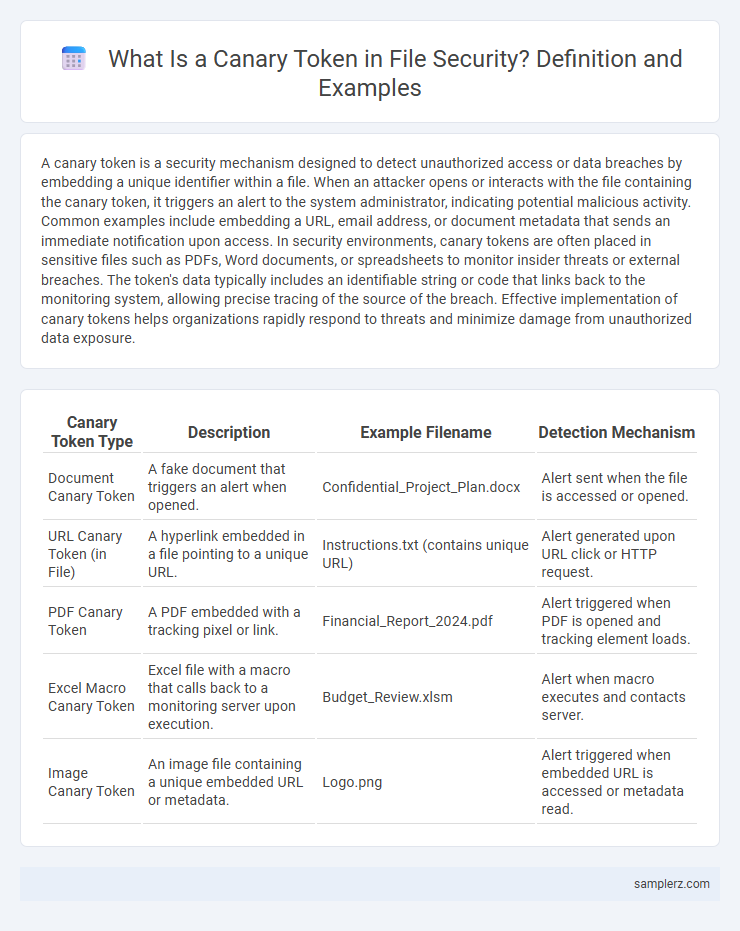
| Canary Token Type | Description | Example Filename | Detection Mechanism |
|---|---|---|---|
| Document Canary Token | A fake document that triggers an alert when opened. | Confidential_Project_Plan.docx | Alert sent when the file is accessed or opened. |
| URL Canary Token (in File) | A hyperlink embedded in a file pointing to a unique URL. | Instructions.txt (contains unique URL) | Alert generated upon URL click or HTTP request. |
| PDF Canary Token | A PDF embedded with a tracking pixel or link. | Financial_Report_2024.pdf | Alert triggered when PDF is opened and tracking element loads. |
| Excel Macro Canary Token | Excel file with a macro that calls back to a monitoring server upon execution. | Budget_Review.xlsm | Alert when macro executes and contacts server. |
| Image Canary Token | An image file containing a unique embedded URL or metadata. | Logo.png | Alert triggered when embedded URL is accessed or metadata read. |
What Are Canary Tokens?
Canary tokens are small, covert security triggers embedded within files or systems to detect unauthorized access by alerting administrators when the token is accessed or manipulated. Common examples include embedded unique URLs, fake login credentials, or specially crafted documents that activate notifications upon interaction. These tokens serve as early warning mechanisms, enabling rapid response to potential breaches or insider threats in cybersecurity environments.
How Canary Tokens Enhance File Security
Canary tokens embedded within files act as covert tripwires, triggering alerts when unauthorized access or tampering occurs, thereby providing real-time breach detection. These tokens can be crafted as unique links, hidden documents, or executable scripts, ensuring that any interaction signals potential insider threats or external attacks. Their strategic placement in sensitive files strengthens file security by facilitating early intervention and forensic analysis.
Common Types of Canary Token Files
Common types of canary token files include fake PDFs, images, and Word documents embedded with tracking mechanisms that alert administrators upon unauthorized access. These files often contain hidden links or unique identifiers that trigger notifications when opened or copied, enabling early detection of breaches. Utilizing diverse file formats increases the likelihood of catching malicious insiders or hackers attempting to exfiltrate sensitive data.
Step-by-Step: Embedding Canary Tokens in Documents
Embedding canary tokens in documents involves generating a unique, trackable token from a canary token service and embedding it within the text or metadata of the file. Save the document and upload it to a monitoring platform linked to the canary token, allowing real-time alerts when the file is accessed or copied. This proactive measure helps security teams detect unauthorized use or data exfiltration with precise contextual information.
Real-World Examples of Canary Token Use
A common real-world example of a canary token in a file is embedding a unique, invisible watermark or a disguised URL that triggers an alert when accessed, indicating unauthorized use or data exfiltration. Financial institutions often use canary tokens in sensitive spreadsheets to detect insider threats by monitoring for unauthorized downloads or openings. Similarly, tech companies embed canary tokens within software builds or configuration files to identify breaches when someone tampers with or extracts these files without permission.
Detecting Unauthorized Access with Canary Tokens
Embedding canary tokens within sensitive files enables real-time detection of unauthorized access by triggering alerts when the files are opened or copied. These tokens can take the form of unique URLs, fake credentials, or hidden data snippets strategically placed to monitor file interactions. Implementing canary tokens enhances cybersecurity by providing early warnings of potential breaches and insider threats within secured environments.
Industry Applications for File-Based Canary Tokens
File-based canary tokens are strategically embedded within sensitive documents or critical system files in sectors like finance, healthcare, and government to detect unauthorized access instantly. When these tokens are triggered by malicious actors or intruders, they send real-time alerts to cybersecurity teams, enabling rapid incident response and minimizing data breaches. This proactive approach enhances threat detection by leveraging disguised markers within vital files, ensuring robust protection of confidential information in high-risk industries.
Case Study: Canary Token Alert Scenarios
A canary token embedded in a sensitive file can trigger alerts when unauthorized access or exfiltration attempts occur, providing real-time detection of insider threats or cyber intrusions. For example, a document containing a hidden URL or embedded beacon can notify security teams immediately upon file opening or copying, enabling rapid incident response. Such case studies demonstrate how canary tokens effectively enhance threat visibility and reduce dwell time in targeted attacks.
Best Practices for Deploying Canary Tokens in Files
Embedding canary tokens in critical system files, such as configuration or script files, ensures early detection of unauthorized access by triggering alerts when the file is accessed or modified. Best practices include using unique, non-obvious token names, encrypting token content to avoid flagging by security tools, and integrating alert systems with centralized monitoring platforms for real-time incident response. Regularly rotating canary tokens and combining them with file integrity monitoring enhances overall detection reliability and minimizes false positives.
Limitations and Considerations of Canary Token Files
Canary token files, while effective for detecting unauthorized access, have limitations such as the risk of false positives triggered by benign user activity or automated system scans. These tokens may be discovered and neutralized by sophisticated attackers who recognize the patterns or file signatures used in canary tokens. Organizations must consider deployment strategies, ensuring tokens are embedded in locations that balance stealth with detection coverage to minimize operational disruptions.
example of canary token in file Infographic
 samplerz.com
samplerz.com