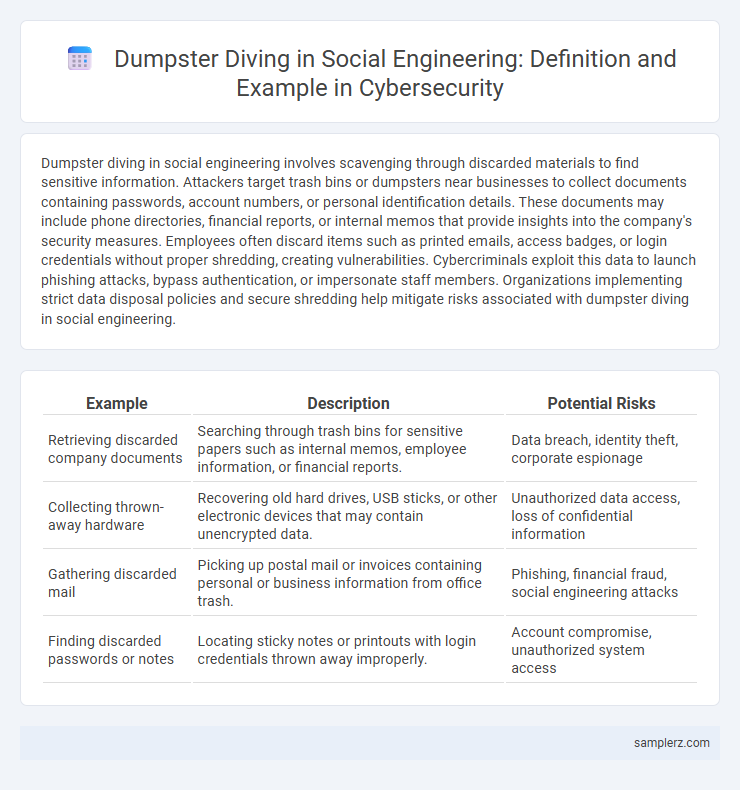
Dumpster diving in social engineering involves scavenging through discarded materials to find sensitive information. Attackers target trash bins or dumpsters near businesses to collect documents containing passwords, account numbers, or personal identification details. These documents may include phone directories, financial reports, or internal memos that provide insights into the company's security measures. Employees often discard items such as printed emails, access badges, or login credentials without proper shredding, creating vulnerabilities. Cybercriminals exploit this data to launch phishing attacks, bypass authentication, or impersonate staff members. Organizations implementing strict data disposal policies and secure shredding help mitigate risks associated with dumpster diving in social engineering.
Table of Comparison
| Example | Description | Potential Risks |
|---|---|---|
| Retrieving discarded company documents | Searching through trash bins for sensitive papers such as internal memos, employee information, or financial reports. | Data breach, identity theft, corporate espionage |
| Collecting thrown-away hardware | Recovering old hard drives, USB sticks, or other electronic devices that may contain unencrypted data. | Unauthorized data access, loss of confidential information |
| Gathering discarded mail | Picking up postal mail or invoices containing personal or business information from office trash. | Phishing, financial fraud, social engineering attacks |
| Finding discarded passwords or notes | Locating sticky notes or printouts with login credentials thrown away improperly. | Account compromise, unauthorized system access |
Real-Life Dumpster Diving Scenarios in Social Engineering
Real-life dumpster diving in social engineering often involves attackers retrieving discarded documents containing sensitive information such as passwords, financial records, or personal identification details from trash bins outside corporate offices. One notable example includes criminals sifting through company dumpsters to find unshredded printouts of employee login credentials or confidential client contracts, which are then exploited for unauthorized access. These scenarios emphasize the critical importance of secure document disposal methods like shredding and secure bins to prevent data breaches initiated through physical information retrieval.
Common Security Breaches Due to Dumpster Diving
Dumpster diving often leads to significant security breaches by exposing sensitive information such as passwords, financial records, and confidential corporate documents discarded carelessly. Attackers exploit this data to gain unauthorized access, resulting in identity theft, phishing attacks, and corporate espionage. Organizations lacking proper waste management protocols face increased risks of data leaks and compliance violations.
Corporate Espionage Through Dumpster Diving
Corporate espionage often employs dumpster diving to retrieve sensitive information discarded in trash bins, such as financial reports, employee credentials, and confidential project details. Attackers exploit this data to gain unauthorized access to company systems or to sell proprietary information to competitors. Implementing strict data disposal policies and secure shredding methods reduces the risk of valuable corporate data falling into malicious hands.
Case Studies: Dumpster Diving Attacks on Businesses
Several case studies highlight dumpster diving as a critical social engineering tactic, where attackers extract sensitive business information from improperly discarded documents. In one notable incident, a financial firm suffered a breach after attackers recovered confidential client data and passwords from discarded printed reports. This emphasizes the importance of secure document disposal methods like shredding to prevent unauthorized access to corporate secrets.
Sensitive Data Recovered from Trash: True Incidents
Dumpster diving in social engineering often leads to the recovery of sensitive data such as unshredded financial statements, discarded login credentials, and confidential corporate memos. True incidents reveal attackers retrieving printed passwords, employee personal information, and proprietary business plans directly from improperly disposed trash bins. These breaches underscore the critical need for secure data destruction policies to prevent unauthorized access through physical waste retrieval.
How hackers Use Dumpster Diving to Bypass Security
Hackers use dumpster diving to bypass security by scavenging through discarded documents, electronics, and storage media to find sensitive information such as passwords, account numbers, or confidential business plans. This technique exploits poor data disposal practices, allowing intruders to gather intelligence that can facilitate phishing attacks, unauthorized access, or identity theft. Implementing strict shredding policies and secure data destruction methods significantly reduces the risk posed by dumpster diving in social engineering attacks.
Notorious Dumpster Diving Attacks in History
Notorious dumpster diving attacks include the 2003 incident involving hackers infiltrating a major financial firm by retrieving discarded hard drives containing unencrypted customer data. Another infamous case occurred in 2005 when attackers gained access to sensitive military documents by sifting through improperly disposed paper waste at a defense contractor's facility. These examples highlight the critical need for comprehensive data disposal policies and secure shredding practices to prevent social engineering exploits via dumpster diving.
Dumpster Diving Success Stories in Social Engineering
Hackers gained access to a major corporation's confidential data by scavenging through improperly discarded employee documents containing login credentials and network diagrams. In another incident, social engineers retrieved discarded invoices and memos from a government agency's trash, enabling them to impersonate employees and gain unauthorized system access. These dumpster diving success stories highlight the critical importance of secure document disposal and stringent access controls in preventing data breaches.
Exposed: Leaked Confidential Information via Dumpster Diving
Dumpster diving exposes sensitive data by retrieving discarded documents containing confidential information such as passwords, internal memos, or employee records. Cybercriminals exploit this physical security lapse to gain unauthorized access to systems or launch targeted social engineering attacks. Proper shredding protocols and secure disposal methods significantly reduce the risk of leaking critical organizational data through dumpster diving.
Lessons Learned from Dumpster Diving Security Lapses
Dumpster diving exposes how sensitive information like passwords, financial records, and employee details are often discarded without shredding, leading to significant security breaches. Lessons learned emphasize secure data disposal methods, employee awareness training, and implementing strict document handling policies to prevent unauthorized access. Organizations must regularly audit waste management practices to mitigate risks associated with social engineering attacks exploiting improperly discarded materials.
example of dumpster diving in social engineering Infographic
 samplerz.com
samplerz.com