A canary in breach detection is a security mechanism that acts as an early warning system to identify unauthorized access within a network. It involves deploying fake data or decoy resources that alert security teams when accessed or altered by attackers. These artificial canaries generate alerts that provide critical entity information, such as the source IP address and the method of intrusion, facilitating rapid incident response. In practical applications, a canary might be a bogus database entry, a fake login credential, or a dummy file strategically placed within a system. Monitoring tools track interactions with these decoys to detect breaches, leveraging metadata and access patterns to distinguish genuine users from malicious actors. This approach enhances data security by proactively detecting exploitation attempts before real assets are compromised.
Table of Comparison
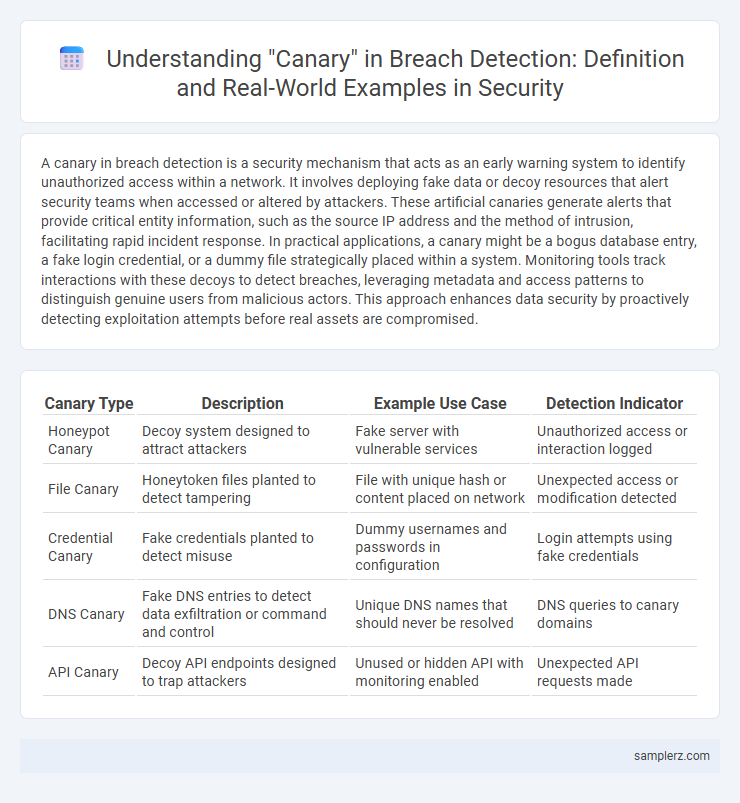
| Canary Type | Description | Example Use Case | Detection Indicator |
|---|---|---|---|
| Honeypot Canary | Decoy system designed to attract attackers | Fake server with vulnerable services | Unauthorized access or interaction logged |
| File Canary | Honeytoken files planted to detect tampering | File with unique hash or content placed on network | Unexpected access or modification detected |
| Credential Canary | Fake credentials planted to detect misuse | Dummy usernames and passwords in configuration | Login attempts using fake credentials |
| DNS Canary | Fake DNS entries to detect data exfiltration or command and control | Unique DNS names that should never be resolved | DNS queries to canary domains |
| API Canary | Decoy API endpoints designed to trap attackers | Unused or hidden API with monitoring enabled | Unexpected API requests made |
Introduction to Canary Tokens in Breach Detection
Canary tokens act as deceptive digital tripwires embedded within systems or documents, designed to silently detect unauthorized access or data exfiltration attempts. These tokens generate instant alerts when triggered, enabling rapid identification of breaches before significant damage occurs. Implementing canary tokens enhances breach detection by providing early warning signs, improving incident response times, and reducing overall security risks.
How Canary Tokens Work in Modern Security
Canary tokens operate by embedding unique, stealthy identifiers within files, links, or network requests, triggering immediate alerts when accessed by unauthorized users. These tokens mimic valuable assets, enabling rapid breach detection and limiting the window for potential data exfiltration. Integrating canary tokens into security infrastructure enhances real-time monitoring and strengthens incident response capabilities.
Real-World Examples of Successful Canary Deployment
In 2022, a major financial institution deployed canary tokens embedded in decoy database entries, which triggered immediate alerts when accessed by unauthorized users, preventing a potential data leak. Another example involves a healthcare provider that utilized email-based canary tokens hidden in sensitive reports, successfully detecting phishing attempts targeting patient records. These real-world deployments highlight how strategic placement of canary tokens enhances breach detection by providing early warnings of insider threats and external attacks.
Types of Canary Tokens Used in Networks
Canary tokens in breach detection include file canaries, URL canaries, and DNS canaries, each designed to silently alert administrators upon unauthorized access or use. File canaries involve creating decoy files that trigger an alert when opened or modified, while URL canaries consist of unique, unused web links monitored for unexpected clicks or requests. DNS canaries monitor domain name system queries for rare or suspicious lookups, providing early warning of lateral movement or reconnaissance by attackers within a network.
Setting Up Canaries for Early Breach Alerts
Setting up canaries for early breach alerts involves deploying decoy resources such as fake files, user accounts, or network services strategically within an organization's infrastructure. These canaries are designed to trigger immediate notifications upon unauthorized access or interaction, enabling rapid detection of cyber threats. Effective implementation requires continuous monitoring, integration with security information and event management (SIEM) systems, and regular updates to maintain their stealth and relevance against evolving attack techniques.
Case Studies: Canaries Thwarting Cyber Attacks
Case studies demonstrate how canaries play a crucial role in breach detection by acting as decoy assets that alert security teams to unauthorized access attempts. For example, in a notable incident, a financial institution deployed canary tokens that triggered immediate alerts when cybercriminals attempted lateral movement within the network, preventing data exfiltration. These real-time warnings enabled swift response and containment of sophisticated ransomware attacks, proving canaries as an effective layer in multi-faceted cybersecurity strategies.
Best Practices for Using Canary Tokens Effectively
Deploying canary tokens across critical systems and sensitive files enhances breach detection by triggering alerts when accessed, indicating unauthorized activity. Regularly updating token locations and ensuring they mimic legitimate data prevent attackers from easily identifying and disabling them. Integrating canary tokens with centralized monitoring tools allows swift incident response, minimizing potential damage and improving overall security posture.
Common Mistakes in Canary Implementation
Common mistakes in canary implementation include deploying insufficiently obfuscated canaries that attackers quickly identify, reducing their effectiveness in breach detection. Another frequent error is placing canaries in predictable locations, making it easier for intruders to avoid triggering alerts. Failure to regularly update and monitor canary logs can lead to missed breach attempts, undermining overall security posture.
Integrating Canary Tokens with Security Systems
Integrating canary tokens with security systems enhances breach detection by embedding unique, invisible markers within critical data or applications that trigger alerts upon unauthorized access. These tokens seamlessly connect with SIEM platforms and intrusion detection systems to provide real-time notifications, enabling rapid response to potential threats. Leveraging canary tokens alongside traditional security measures significantly strengthens an organization's ability to identify and mitigate data breaches early.
Future Trends in Canary-Based Breach Detection
Future trends in canary-based breach detection emphasize the integration of artificial intelligence and machine learning to enhance anomaly detection and reduce false positives. Advanced canaries will leverage behavioral analytics to predict and preempt sophisticated cyberattacks in real-time. The deployment of decentralized canary tokens across distributed networks will improve breach visibility and response times in complex IT environments.
example of canary in breach detection Infographic
 samplerz.com
samplerz.com