A Trojan in application security is a type of malware that masquerades as legitimate software to deceive users and gain unauthorized access to systems. One common example is the Zeus Trojan, which targets banking information by embedding itself into seemingly trustworthy applications. Zeus captures sensitive data such as passwords and financial details without alerting the user, making it a significant threat in cybersecurity. Trojan malware often exploits vulnerabilities in software to infiltrate networks and exfiltrate data. The Emotet Trojan exemplifies this behavior by spreading through malicious email attachments and compromising enterprise environments. Both Zeus and Emotet showcase how Trojans leverage social engineering and hidden payloads to undermine application security and steal crucial information.
Table of Comparison
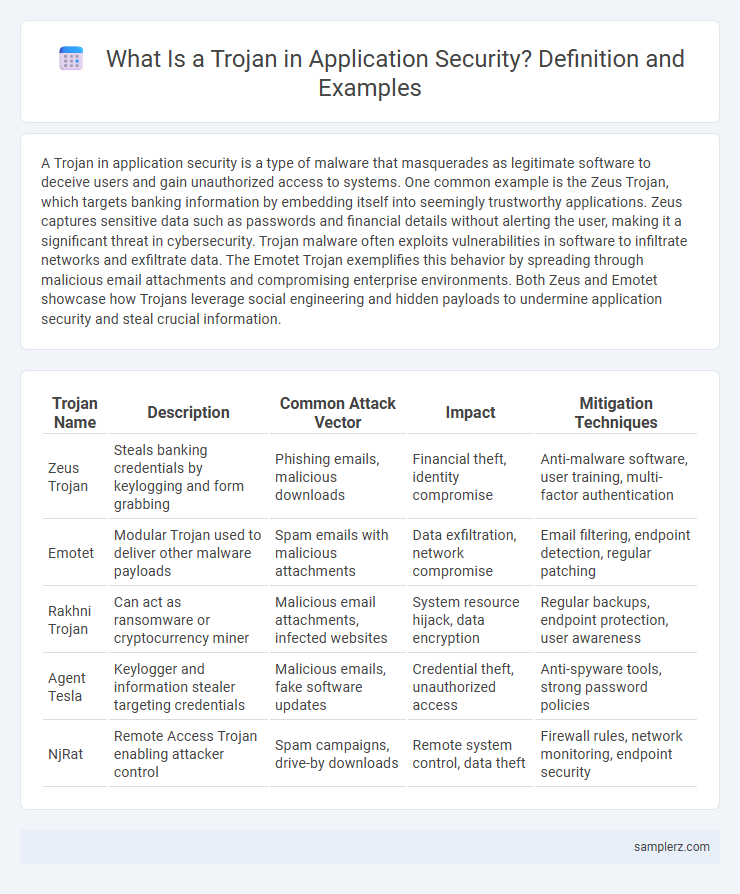
| Trojan Name | Description | Common Attack Vector | Impact | Mitigation Techniques |
|---|---|---|---|---|
| Zeus Trojan | Steals banking credentials by keylogging and form grabbing | Phishing emails, malicious downloads | Financial theft, identity compromise | Anti-malware software, user training, multi-factor authentication |
| Emotet | Modular Trojan used to deliver other malware payloads | Spam emails with malicious attachments | Data exfiltration, network compromise | Email filtering, endpoint detection, regular patching |
| Rakhni Trojan | Can act as ransomware or cryptocurrency miner | Malicious email attachments, infected websites | System resource hijack, data encryption | Regular backups, endpoint protection, user awareness |
| Agent Tesla | Keylogger and information stealer targeting credentials | Malicious emails, fake software updates | Credential theft, unauthorized access | Anti-spyware tools, strong password policies |
| NjRat | Remote Access Trojan enabling attacker control | Spam campaigns, drive-by downloads | Remote system control, data theft | Firewall rules, network monitoring, endpoint security |
Understanding Trojans in Application Security
Trojans in application security disguise malicious code as legitimate software, enabling unauthorized access or control over a system. Common examples include Remote Access Trojans (RATs) like Emotet, which steal sensitive information and enable attackers to remotely manipulate infected devices. Detecting Trojans often requires behavioral analysis and real-time monitoring to identify unusual application activity and prevent data breaches.
Notable Real-World Trojan Attacks on Applications
One notable real-world Trojan attack on applications is the Zeus Trojan, which targeted financial institutions by stealing banking credentials through keylogging and form grabbing techniques. Another significant example is Emotet, initially a banking Trojan that evolved into a modular malware distributing other malicious payloads like ransomware, impacting global business networks. The Dridex Trojan also stands out, primarily focusing on stealing banking information by exploiting email attachments and macros to infiltrate enterprise systems.
How Trojans Infiltrate Application Software
Trojans infiltrate application software by masquerading as legitimate programs or embedding malicious code within trusted applications, bypassing traditional security measures. Attackers exploit vulnerabilities in software distribution channels, such as downloading from unverified sources or injecting payloads during software updates, allowing the Trojan to execute malicious activities undetected. Once inside, Trojans can create backdoors, steal sensitive data, or manipulate application functionality, severely compromising application security.
Infamous Trojan Examples in Mobile Applications
Mobile applications are frequently targeted by notorious Trojans such as the Joker Trojan, which secretly subscribes users to premium services, and the Anubis Trojan, known for harvesting banking credentials. Another infamous example is the Triada Trojan, which gains root access to manipulate system processes and steal sensitive data. These Trojans exploit vulnerabilities in app permissions to compromise mobile security, making them critical threats in application security.
Case Study: Zeus Trojan in Banking Apps
The Zeus Trojan is a notorious example of malware targeting banking applications by stealing login credentials through keylogging and form grabbing techniques. This Trojan has been responsible for millions in financial losses by intercepting sensitive user data during online transactions. Security measures like multi-factor authentication and behavior-based detection are crucial to mitigating the impact of such threats in application security.
Application Backdoors: Trojans in Software Updates
Application backdoors embedded through trojans in software updates expose critical vulnerabilities by granting unauthorized access and control to attackers. These trojanized updates often exploit trusted distribution channels, compromising the integrity of widely deployed applications and enabling covert data exfiltration or system manipulation. Notable incidents like the SolarWinds attack highlight the severe impact of such backdoors on enterprise security and supply chain trustworthiness.
Remote Access Trojans (RATs) Targeting Desktop Applications
Remote Access Trojans (RATs) like Gh0st RAT and DarkComet specifically target desktop applications to gain unauthorized control over victim systems. These RATs exploit vulnerabilities in commonly used software such as Microsoft Office and web browsers to establish stealthy backdoors, allowing attackers to remotely monitor, manipulate files, and steal sensitive data. Defending against these threats requires robust endpoint protection, timely patch management, and user awareness to detect suspicious activities within desktop environments.
Supply Chain Attacks Involving Trojanized Applications
Trojanized applications in supply chain attacks exploit trusted software distribution channels to infect legitimate applications with malicious code, compromising enterprise security. A notable example is the SolarWinds Orion attack, where trojaned updates were delivered to thousands of organizations, allowing attackers to gain persistent access and exfiltrate sensitive data. These attacks highlight the critical need for rigorous supply chain integrity verification and continuous monitoring of application updates to prevent the insertion of trojans.
Techniques for Detecting Trojans in Application Security
Techniques for detecting Trojans in application security include static code analysis, which examines source code for suspicious patterns, and dynamic behavior monitoring that tracks application actions during runtime to identify anomalies. Signature-based detection uses databases of known Trojan characteristics to flag malicious code, while heuristic analysis employs algorithmic detection of deviations from normal application behavior. Incorporating machine learning models enhances detection accuracy by identifying previously unknown Trojans through pattern recognition in vast datasets.
Preventing and Mitigating Trojan Threats in Applications
Trojan threats in application security often manifest as malicious code disguised within legitimate software, leading to unauthorized access or data breaches. Preventing Trojans requires implementing robust code validation, employing advanced malware detection tools, and regularly updating application security protocols to identify and block suspicious behavior early. Mitigation strategies include continuous monitoring of application activity, isolating compromised components quickly, and conducting thorough incident response to minimize damage and restore system integrity.
example of trojan in application security Infographic
 samplerz.com
samplerz.com