Skimming in card fraud involves the illegal capture of data from the magnetic stripe of a payment card. Criminals use small devices called skimmers, which are often attached to ATMs, gas station pumps, or point-of-sale terminals. These devices record card information, including the cardholder's name, account number, and expiration date, enabling unauthorized transactions. The stolen data collected through skimming can be cloned onto counterfeit cards or used for online purchases. Fraudsters exploit this data to bypass security measures, resulting in financial losses for consumers and businesses. Timely detection of skimming devices and advanced transaction monitoring are critical in minimizing card fraud incidences.
Table of Comparison
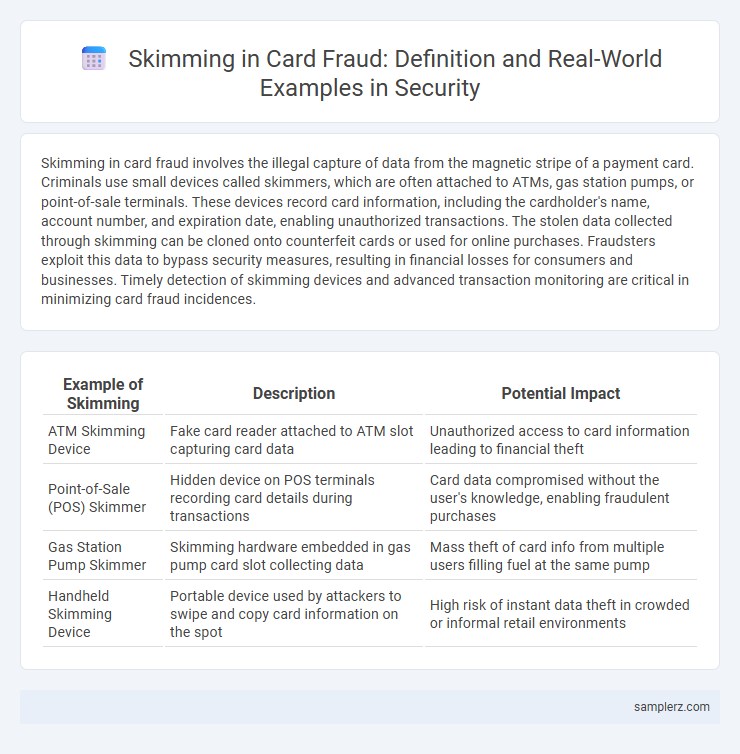
| Example of Skimming | Description | Potential Impact |
|---|---|---|
| ATM Skimming Device | Fake card reader attached to ATM slot capturing card data | Unauthorized access to card information leading to financial theft |
| Point-of-Sale (POS) Skimmer | Hidden device on POS terminals recording card details during transactions | Card data compromised without the user's knowledge, enabling fraudulent purchases |
| Gas Station Pump Skimmer | Skimming hardware embedded in gas pump card slot collecting data | Mass theft of card info from multiple users filling fuel at the same pump |
| Handheld Skimming Device | Portable device used by attackers to swipe and copy card information on the spot | High risk of instant data theft in crowded or informal retail environments |
Understanding Skimming: A Major Card Fraud Technique
Skimming is a card fraud technique where criminals use a small device called a skimmer to illegally capture data from the magnetic stripe of credit or debit cards during legitimate transactions. These devices are often attached to ATMs, gas pumps, or point-of-sale terminals, allowing fraudsters to steal card information without the victim's knowledge. Understanding skimming's methods and recognizing suspicious equipment at payment terminals are critical steps in preventing unauthorized access to sensitive card data.
How Skimming Devices Are Installed on ATMs
Skimming devices are often discreetly installed on ATM card slots by criminals to capture card information during transactions. These devices are designed to look like part of the ATM, making them difficult for users to detect while they secretly record magnetic stripe data and PIN entries via hidden cameras or keyloggers. Bank customers should be vigilant for unusual attachments or loose card readers to protect against skimming fraud.
Real-World Skimming Incidents: Case Studies
Real-world skimming incidents frequently involve criminals installing covert card readers on ATMs and gas station pumps to capture magnetic stripe data and PINs, leading to massive financial losses. One notable case is the 2018 compromise of gas stations in the US Midwest, where over 200,000 debit and credit cards were skimmed, resulting in millions of dollars in fraudulent transactions. Effective countermeasures include EMV chip adoption and enhanced ATM surveillance to reduce card-present fraud.
Signs Your Card May Have Been Skimmed
Unexplained charges or small test transactions on your bank statement can indicate card skimming. Physical signs include unusual attachments or scratches on the card reader at ATMs or gas pumps. Slow or malfunctioning card readers and sudden declines during transactions may also signal that your card information has been compromised.
Common Locations Targeted by Skimmers
Skimming devices are frequently found on ATMs, gas station pumps, and convenience store card readers, where they covertly capture card information. These devices are often installed on the card slot or keypad to record magnetic stripe data and PINs without detection. High-traffic areas with limited surveillance are especially vulnerable to skimming attacks, increasing the risk of card fraud for unsuspecting consumers.
Skimming in Restaurants and Retail: Tactics Explained
Skimming in restaurants and retail often involves discreetly installing card readers on point-of-sale terminals or handheld payment devices to capture card data during legitimate transactions. Criminals use overlay devices or small cameras to record card numbers and PINs without alerting customers or employees. This data is then cloned onto counterfeit cards for unauthorized purchases, highlighting the importance of secure payment systems and vigilant staff training.
The Role of Technology in Detecting Card Skimming
Advanced technology, such as EMV chip readers and AI-driven transaction monitoring systems, plays a critical role in detecting card skimming by identifying unusual patterns and unauthorized data captures. Machine learning algorithms analyze real-time transaction data to flag anomalies indicative of skimming devices or cloned cards. Enhanced surveillance tools and encryption methods further prevent fraud by securing cardholder information during transactions.
How Criminals Profit from Skimmed Card Data
Criminals profit from skimmed card data by cloning magnetic stripe information to create counterfeit cards, enabling unauthorized purchases or cash withdrawals. They also sell stolen card details on the dark web, where fraudsters use the information for online transactions without physical cards. The illicit gains stem from exploiting merchant and cardholder vulnerabilities before transactions are detected and blocked.
Methods to Protect Yourself Against Skimming
Use RFID-blocking wallets and sleeves to prevent unauthorized scanning of contactless cards, minimizing the risk of skimming. Regularly monitor bank statements and set up fraud alerts to detect suspicious transactions early. Avoid using ATMs or payment terminals in untrusted or poorly lit locations where skimming devices are often installed.
Reporting and Responding to Skimming Fraud
Victims of card skimming should immediately report suspicious transactions to their bank or card issuer to prevent further unauthorized charges. Promptly notifying law enforcement and providing details such as transaction history and locations of suspected skimming devices enhances the investigation process. Cardholders must also monitor account statements regularly and request card reissuance when skimming fraud is detected to secure their financial information.
example of skimming in card fraud Infographic
 samplerz.com
samplerz.com