Shoulder surfing in social engineering occurs when an attacker observes confidential information by looking over someone's shoulder. This technique is commonly used to capture sensitive data such as passwords, PINs, or security codes entered on devices in public spaces. Attackers may exploit crowded environments like cafes or airports to discreetly collect personal or corporate security credentials. Instances of shoulder surfing involve observing victims as they input login details at ATMs or type passwords on laptops. This method poses significant risks in corporate environments where unauthorized access to secure systems can lead to data breaches. Employing tactics like privacy screens and awareness training can mitigate the threat posed by shoulder surfing in cybersecurity.
Table of Comparison
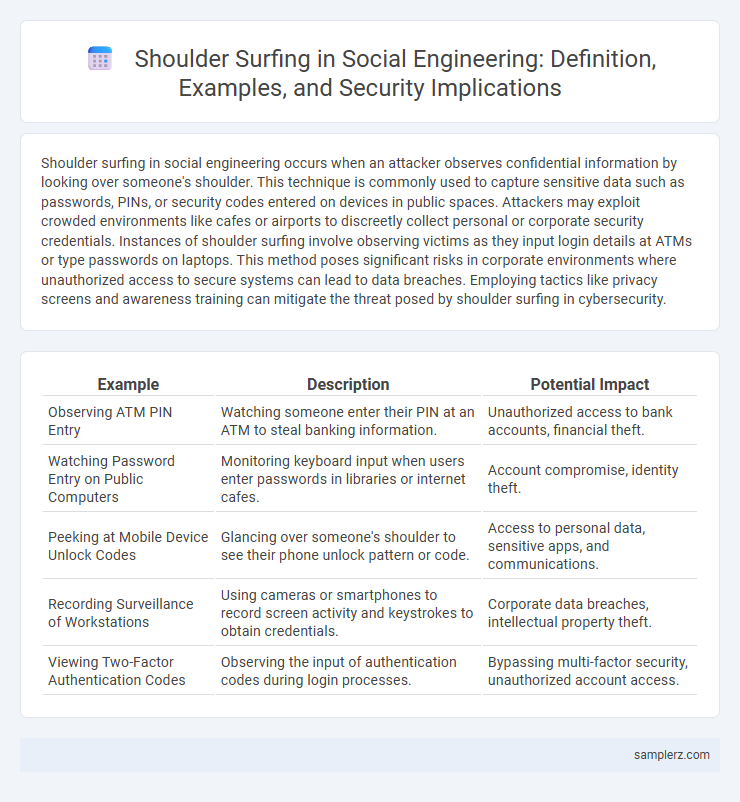
| Example | Description | Potential Impact |
|---|---|---|
| Observing ATM PIN Entry | Watching someone enter their PIN at an ATM to steal banking information. | Unauthorized access to bank accounts, financial theft. |
| Watching Password Entry on Public Computers | Monitoring keyboard input when users enter passwords in libraries or internet cafes. | Account compromise, identity theft. |
| Peeking at Mobile Device Unlock Codes | Glancing over someone's shoulder to see their phone unlock pattern or code. | Access to personal data, sensitive apps, and communications. |
| Recording Surveillance of Workstations | Using cameras or smartphones to record screen activity and keystrokes to obtain credentials. | Corporate data breaches, intellectual property theft. |
| Viewing Two-Factor Authentication Codes | Observing the input of authentication codes during login processes. | Bypassing multi-factor security, unauthorized account access. |
Common Real-World Scenarios of Shoulder Surfing
Shoulder surfing commonly occurs in crowded public places such as ATMs, coffee shops, and public transportation where attackers glance over victims' shoulders to capture sensitive information like PINs, passwords, or credit card details. Employees in open office environments are also vulnerable when entering confidential data on computer screens exposed to nearby coworkers or visitors. This social engineering tactic exploits human negligence, emphasizing the importance of vigilance and privacy awareness in everyday security practices.
ATM PIN Theft: A Classic Shoulder Surfing Example
Shoulder surfing during ATM PIN entry occurs when an attacker closely observes or records a victim's PIN input to steal sensitive banking credentials. Criminals may use hidden cameras or simply glance over the shoulder in crowded or poorly monitored ATM locations to capture the four-digit code. This type of social engineering attack exploits human vulnerability to gain unauthorized access to financial accounts and commit fraud.
Shoulder Surfing in Crowded Public Transportation
Shoulder surfing in crowded public transportation occurs when attackers discreetly observe individuals entering sensitive information, such as PINs or passwords, on smartphones, ATMs, or transit cards. This form of social engineering exploits the close physical proximity and distractions typical in buses or subways to capture confidential data without victims' awareness. Using small cameras or simply peering over shoulders, perpetrators can easily gather personal credentials, leading to identity theft or unauthorized access to accounts.
Coffee Shop Wi-Fi: Observing Screen Activity
Shoulder surfing in social engineering often occurs in coffee shop Wi-Fi environments where attackers observe screen activity to capture sensitive information such as passwords or personal data. Public Wi-Fi networks lack strong encryption, making it easier for hackers to monitor unencrypted communications and gather credentials displayed on users' screens. Users should be cautious when accessing confidential information in public spaces and utilize virtual private networks (VPNs) to protect against shoulder surfing risks.
Entering Secure Passcodes at Workstations
Shoulder surfing in social engineering occurs when an attacker observes someone entering secure passcodes at workstations to gain unauthorized access. This technique exploits human vulnerability by capturing keystrokes or viewing screen inputs discreetly. Implementing privacy screens and awareness training can significantly reduce the risk of such breaches.
Mobile Device Unlock Patterns Exposed
Shoulder surfing in social engineering often targets mobile device unlock patterns, where attackers observe the unique swipe gestures users perform to access their phones. These patterns, easily replicated due to repetitive motion and visible screen traces, compromise device security by allowing unauthorized access. Enhanced awareness and privacy shields on screens can significantly reduce the risk of shoulder surfing attacks on unlock patterns.
Social Engineering at Hotel Check-In Counters
At hotel check-in counters, shoulder surfing occurs when attackers discreetly observe guests entering personal information, such as passport details or credit card numbers. This social engineering tactic exploits the busy environment to capture sensitive data without raising suspicion. Implementing privacy screens and positioning counters away from public view can mitigate the risk of such information theft.
Shoulder Surfing During Conference Registration
Shoulder surfing during conference registration occurs when an attacker discreetly observes sensitive information such as personal identification numbers, passwords, or registration details as attendees input data at kiosks or check-in counters. This form of social engineering exploits the physical proximity and lack of privacy in crowded registration areas to capture credentials or personal information for unauthorized access. Implementing privacy screens, physical barriers, and staff awareness training can mitigate the risk of shoulder surfing incidents during event registration processes.
Eavesdropping on Sensitive Calls in Open Offices
Eavesdropping on sensitive calls in open offices is a common example of shoulder surfing in social engineering, where attackers overhear confidential information such as passwords, financial data, or strategic plans. Open office layouts with minimal sound barriers increase the risk of unauthorized listeners capturing critical conversations. Implementing privacy measures like sound masking systems and designated quiet zones helps protect sensitive communications from eavesdropping threats.
Visual Hacking in Airports and Public Waiting Areas
Shoulder surfing in airports and public waiting areas involves attackers visually capturing sensitive information by observing victims enter passwords, PINs, or personal data on devices or boarding passes. This form of visual hacking exploits crowded, unsecured environments where individuals may unknowingly expose confidential details due to limited attention to their surroundings. Security measures such as privacy screens, awareness training, and strategic seating arrangements can mitigate the risks of shoulder surfing in these high-traffic locations.
example of shoulder surfing in social engineering Infographic
 samplerz.com
samplerz.com