Cold boot attacks exploit the residual data retained in a computer's memory after it is powered off. In this scenario, an attacker forcibly reboots a device without performing a proper shutdown, then quickly accesses the volatile memory to retrieve sensitive information. This method targets encryption keys, passwords, and other critical data stored temporarily in RAM, which remains accessible due to memory remanence. During a cold boot data extraction, the attacker typically uses a specially prepared external device or boots from an alternative operating system to bypass security protocols. The extracted data may reveal encryption keys, allowing unauthorized access to encrypted drives and networks. This attack highlights vulnerabilities in memory handling and emphasizes the need for robust full-disk encryption with hardware-based protections.
Table of Comparison
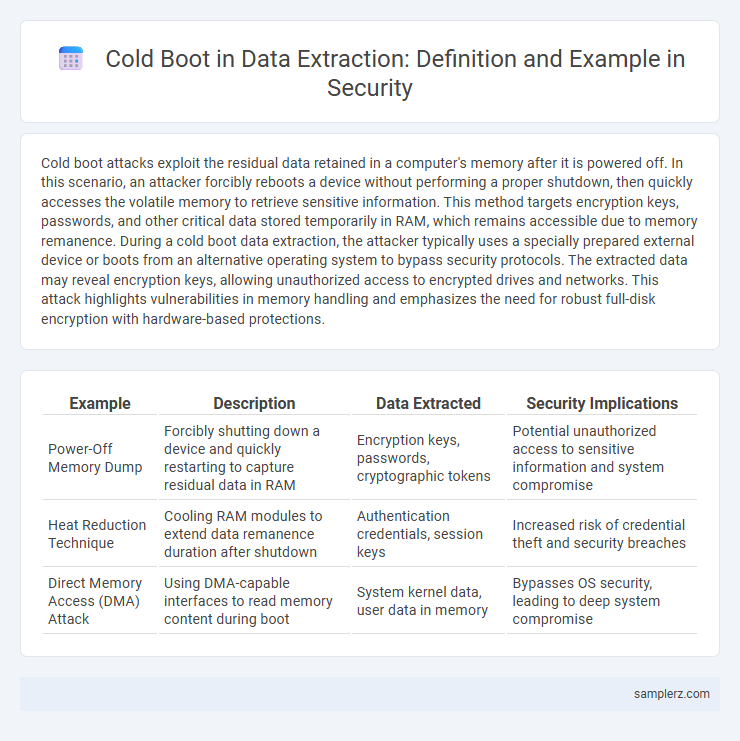
| Example | Description | Data Extracted | Security Implications |
|---|---|---|---|
| Power-Off Memory Dump | Forcibly shutting down a device and quickly restarting to capture residual data in RAM | Encryption keys, passwords, cryptographic tokens | Potential unauthorized access to sensitive information and system compromise |
| Heat Reduction Technique | Cooling RAM modules to extend data remanence duration after shutdown | Authentication credentials, session keys | Increased risk of credential theft and security breaches |
| Direct Memory Access (DMA) Attack | Using DMA-capable interfaces to read memory content during boot | System kernel data, user data in memory | Bypasses OS security, leading to deep system compromise |
Understanding Cold Boot Attacks in Data Extraction
Cold boot attacks exploit the residual data stored in a computer's RAM immediately after a system reboot or power loss, allowing attackers to extract sensitive information such as encryption keys and passwords. By quickly accessing memory before data fades, malicious actors bypass traditional security measures like full disk encryption. Understanding this vulnerability highlights the need for hardware-level protections and rapid memory clearing techniques to safeguard critical data from unauthorized extraction.
Key Stages of a Cold Boot Attack Explained
A cold boot attack exploits data remanence in a computer's RAM by forcibly rebooting the system and quickly dumping the memory contents before data decays. Key stages include powering off the device abruptly, rebooting from an external source or bootable media, and extracting residual encryption keys stored in the RAM. This attack targets encryption keys stored temporarily in volatile memory, enabling unauthorized access to protected data even after system shutdown.
Real-World Examples of Cold Boot Data Extraction
During a 2008 demonstration, researchers at Princeton University successfully retrieved encryption keys from a computer's RAM within seconds of a cold reboot, highlighting vulnerabilities in live memory. Law enforcement agencies have also exploited cold boot attacks to recover encryption keys from seized devices, bypassing traditional data protection methods. High-profile cases, like the extraction of data from encrypted hard drives in criminal investigations, underscore the real-world application and risks of cold boot attacks in cybersecurity.
Hardware Vulnerabilities Exposed by Cold Boot Attacks
Cold boot attacks exploit hardware vulnerabilities by retrieving sensitive data from a computer's RAM after a system shutdown or reboot, as residual data remains momentarily accessible due to DRAM's data remanence property. Attackers physically access the memory modules, rapidly cooling them to extend data retention time and then extract encryption keys or passwords from the memory contents. This hardware weakness highlights the critical need for memory encryption and secure key storage to mitigate the risk of data extraction through cold boot attacks.
Tools Commonly Used in Cold Boot Extraction
Cold boot data extraction commonly employs tools such as forensic memory imaging software like Volatility and DumpIt, which capture volatile data from RAM after system reboot. Hardware devices like PCIe RAM capture cards are utilized to directly access memory modules, enhancing data retrieval efficiency. Specialized scripts and memory analysis frameworks assist investigators in identifying residual data fragments critical for security breach analysis.
Memory Imaging Techniques in Cold Boot Scenarios
Cold boot attacks exploit residual data in RAM by rapidly rebooting a device to capture memory contents before they fade. Memory imaging techniques in these scenarios utilize specialized tools like Volatility or DumpIt to extract volatile data with minimal alteration to the system state. These methods prioritize speed and precision to preserve encryption keys, passwords, and sensitive artifacts critical for forensic analysis.
Case Studies: Sensitive Data Retrieved via Cold Boot
Case studies demonstrate that cold boot attacks enable attackers to extract sensitive data such as encryption keys and passwords from a device's RAM after a sudden power loss. For instance, researchers recovered full disk encryption keys from stolen laptops using cold boot techniques, bypassing traditional security protections. These incidents highlight critical vulnerabilities in memory remanence that threat actors exploit to compromise data confidentiality.
Preventative Measures against Cold Boot Data Extraction
Preventative measures against cold boot data extraction include encrypting sensitive data stored in RAM and implementing full memory encryption technologies like Intel SGX or AMD SEV. Utilizing hardware-based security modules and enabling BIOS-level memory overwriting during system shutdown can significantly reduce the risk of data remanence. Regularly applying firmware updates and employing endpoint security solutions with anti-tampering capabilities further safeguard against cold boot attack vectors.
Legal Implications of Cold Boot Forensic Methods
Cold boot attacks exploit residual data in RAM after a system is powered off, raising complex legal implications regarding evidence admissibility and privacy rights. Courts often scrutinize the chain of custody and the method's compliance with data protection laws such as GDPR or HIPAA. Organizations must ensure that forensic procedures align with jurisdictional regulations to avoid potential litigation or the exclusion of critical digital evidence.
Future Trends in Cold Boot Data Extraction Security
Future trends in cold boot data extraction security emphasize advanced encryption techniques such as full memory encryption and hardware-based key storage to prevent unauthorized data retrieval. Implementation of real-time memory integrity checks and AI-powered anomaly detection enhances early identification of cold boot attacks. Integration of secure enclave technologies within CPUs further restricts access to volatile memory during system resets, significantly mitigating cold boot vulnerabilities.
example of cold boot in data extraction Infographic
 samplerz.com
samplerz.com