Polymorphic malware is a sophisticated type of malicious software designed to evade detection by continuously changing its code while maintaining its original functionality. An example of polymorphic malware is the "Marburg" virus, which alters its encryption method and code structure with each infection, making it challenging for traditional antivirus programs to identify and remove it. This dynamic nature of polymorphic malware requires antivirus solutions to implement heuristic and behavioral analysis techniques in addition to signature-based detection. Modern antivirus software like Avast and Kaspersky leverage machine learning algorithms to detect polymorphic malware by analyzing the behavior of suspicious files rather than relying solely on fixed signatures. These antivirus solutions use artificial intelligence to detect anomalies in file behavior, such as unusual system calls or network activity. By focusing on entity behavior and data patterns, they enhance security measures against polymorphic threats, reducing the risk of undetected infections and system breaches.
Table of Comparison
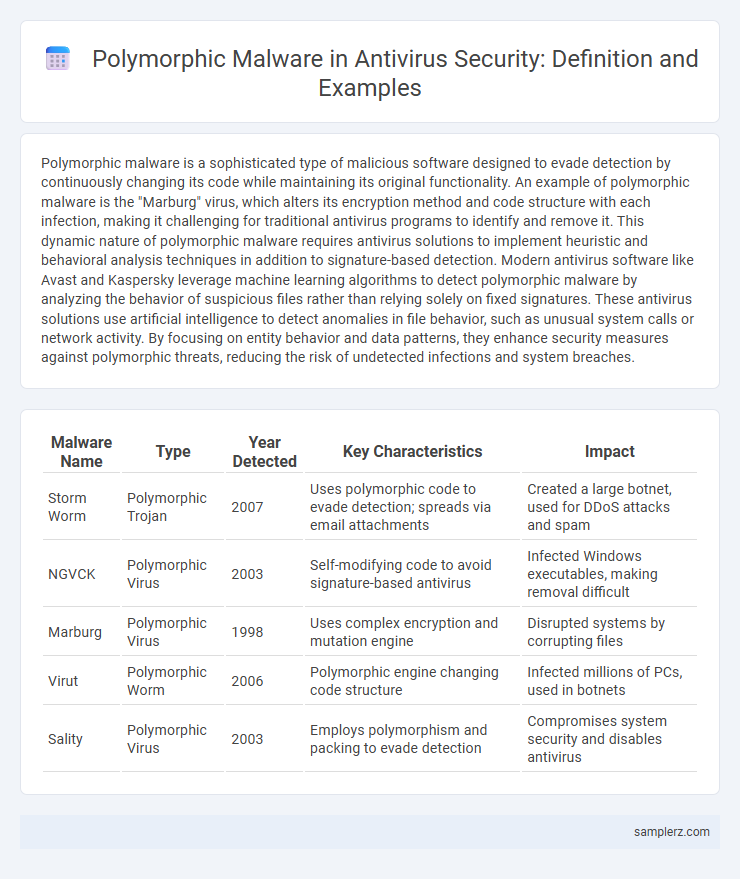
| Malware Name | Type | Year Detected | Key Characteristics | Impact |
|---|---|---|---|---|
| Storm Worm | Polymorphic Trojan | 2007 | Uses polymorphic code to evade detection; spreads via email attachments | Created a large botnet, used for DDoS attacks and spam |
| NGVCK | Polymorphic Virus | 2003 | Self-modifying code to avoid signature-based antivirus | Infected Windows executables, making removal difficult |
| Marburg | Polymorphic Virus | 1998 | Uses complex encryption and mutation engine | Disrupted systems by corrupting files |
| Virut | Polymorphic Worm | 2006 | Polymorphic engine changing code structure | Infected millions of PCs, used in botnets |
| Sality | Polymorphic Virus | 2003 | Employs polymorphism and packing to evade detection | Compromises system security and disables antivirus |
Understanding Polymorphic Malware in Antivirus Security
Polymorphic malware continuously changes its code to evade detection by traditional antivirus software, making it a significant threat in cybersecurity. Examples include the Marburg virus, which alters its encryption key and code structure with each infection to avoid signature-based detection. Advanced antivirus solutions leverage heuristic analysis and machine learning to identify behavioral patterns rather than relying solely on static signatures, enhancing the detection of polymorphic threats.
How Polymorphic Malware Evades Detection
Polymorphic malware evades detection by continuously changing its code structure while maintaining its original malicious functionality, making signature-based antivirus tools ineffective. This malware uses encryption techniques combined with dynamic code mutation to alter its appearance each time it infects a system or attempts execution. Advanced polymorphic variants also employ code obfuscation and encryption keys that regularly update, complicating heuristic and behavioral detection methods utilized by modern cybersecurity solutions.
Notorious Examples of Polymorphic Malware Attacks
Notorious examples of polymorphic malware attacks include the Storm Worm, which used constantly changing code to evade detection, and the Mariposa botnet, known for its sophisticated polymorphic engine that helped it infect millions of systems worldwide. Another critical case is the WannaCry ransomware, which leveraged polymorphic techniques to modify its payload and bypass traditional antivirus signatures. These attacks highlight the challenges faced by antivirus software in identifying and neutralizing rapidly mutating threats.
Polymorphic Viruses and Antivirus Limitations
Polymorphic viruses evade traditional antivirus detection by dynamically changing their code with each infection, making signature-based methods ineffective. These viruses use encryption techniques and code obfuscation to alter their appearance while maintaining their malicious functionality. Antivirus software struggles to detect polymorphic malware due to the constant mutation of code patterns, necessitating more advanced behavioral analysis and heuristic approaches.
Case Study: The Storm Worm Polymorphic Malware
The Storm Worm polymorphic malware demonstrated sophisticated evasion techniques by constantly altering its code to bypass traditional antivirus detection methods. This malware's polymorphic engine generated unique variants in each infection cycle, making signature-based identification ineffective and requiring behavior-based detection approaches. Analysis of the Storm Worm highlights the critical need for adaptive security systems that leverage machine learning to identify evolving polymorphic threats accurately.
Real-World Impact of the CryptoLocker Ransomware
CryptoLocker ransomware exemplifies polymorphic malware by continuously altering its code to evade antivirus detection while encrypting victims' files. This malware encrypted over 250,000 systems globally, demanding ransom payments typically in Bitcoin to restore access. Its adaptive mutation techniques significantly challenged cybersecurity defenses, leading to enhanced heuristic and behavior-based detection methods in antivirus software.
Exploring the Virut Polymorphic File Infector
The Virut polymorphic file infector exemplifies advanced malware that mutates its code to evade signature-based antivirus detection, infecting executable files to propagate stealthily across networks. By continuously altering its encryption and decryption routines, Virut hinders traditional scanning techniques, posing significant challenges for endpoint security solutions. Understanding Virut's polymorphic behavior is crucial for developing heuristic and behavior-based detection methods that enhance protection against evolving file infectors.
Polymorphic Techniques Used by the Zeus Trojan
The Zeus Trojan employs advanced polymorphic techniques by constantly altering its code structure to evade traditional signature-based antivirus detection, utilizing encryption and code obfuscation methods. It generates unique encryption keys for each infection instance, enabling it to change its payload while maintaining functionality and complicating reverse engineering efforts. These adaptive polymorphic strategies significantly increase Zeus's persistence and effectiveness in bypassing security measures.
Effective Antivirus Strategies Against Polymorphic Malware
Effective antivirus strategies against polymorphic malware involve utilizing advanced heuristic analysis and behavior-based detection to identify malicious code despite its constant mutation. Employing machine learning algorithms enhances the ability to detect unknown polymorphic variants by recognizing suspicious patterns rather than relying solely on signature-based identification. Continuous updating of malware databases combined with sandboxing techniques enables antivirus software to analyze and quarantine polymorphic threats before they can execute harmful actions on the system.
Future Trends in Polymorphic Malware and Antivirus Protection
Polymorphic malware such as the Virut and SatanBot variants continuously evolve, using encryption and code mutation techniques to evade traditional antivirus detection. Future trends indicate a rise in AI-driven polymorphic malware capable of autonomously adapting its code to bypass behavioral analysis and signature-based defenses. Antivirus protection is advancing with machine learning algorithms and real-time heuristic analysis to detect and neutralize these dynamic threats more effectively.
example of polymorphic malware in antivirus Infographic
 samplerz.com
samplerz.com